We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Information Technology Infrastructure Library (ITIL) came into existence as a result of technological advancement especially in Information Technology (IT) industry. ITIL 4 DPI drives business success, as it supports businesses with globally recognised framework for standard IT management system. In short, ITIL focuses on a set of best practices which help in aligning IT services with the organisation.
According to the data provided by peoplecert, there are more than 2,000,000 professionals on the ITIL certification path worldwide. ITIL certificate is one of the most widely accepted approaches in the IT Service Management (ITSM) world.
If you want to advance your career in ITIL analytics, but you're not sure how to get ready for the ITIL interview questions and answers, you're at the right place. In this blog, we have discussed the most commonly asked ITIL interview question and their answers. We have divided the ITIL interview questions into four categories.
Table of Contents
1) ITIL Interview Questions for Beginners
2) ITIL Interview Questions for Intermediate Professionals
3) ITIL Interview Questions for Experienced Professionals
4) Scenario based Interview Questions and Answers
5) Conclusion
ITIL Interview Questions for Beginners
We will start with basic ITIL interview questions that will help beginners to land their dream job in ITIL analytics.
1) What is ITIL®?
ITIL focuses on aligning IT services with the business needs of an organisation. It is a set of practices encompassing various IT activities, including IT Asset Management, IT Service Management, and the crucial aspect of ITIL 4 demand management.
2) What does ITIL stand for? Explain in detail.
ITIL stands for Information Technology Infrastructure Library. It is a framework that assists software professionals in delivering highest quality IT services to organisations. The ITIL framework consists of best practices that are updated from time-to-time to meet emerging challenges.
It consists of a set of best practices for IT Service Management (ITSM) that assist in aligning IT services with the needs of customers and businesses according to the current market trends. These best practices may differ depending on the framework they use. they use, such as ITIL V4 Processes and Framework. Comparing ITSM vs ITIL can help you understand the similarities and differences between them.
3) ITIL consists of which processes?
ITIL process are divided into five service lifecycle phases. They are:
a) Service strategy
b) Service design
c) Service transition
d) Service operation
e) Continual service improvement.
4) Describe the benefits of ITIL.
The major benefits of ITIL are as follows:
a) Effective alignment between IT and business
b) Building customer relationships and emphasising customer satisfaction by delivering quality services
c) Managing business risk and service disruption
d) Putting in place cost-effective practices through better utilisation of resources
e) Establishing a robust IT environment
f) Increased transparency of IT costs and resources
g) Supports constant and sudden business change for a stable service environment
h) Helps in creating clear structure of an organisation
i) Improves service availability
j) Assists in improved decision-making process
5) What are the features of ITIL?
Following are the few important features of ITIL:
a) Consistent quality is delivered
b) Follows a single terminology
c) Provides service desk support
d) Capable of data integration
e) Capable of automating processes
f) Organising and implementing the function is flexible
6) Explain the phases of the ITIL® lifecycle.
The different phases or stages of the ITIL Lifecycle are:
a) Service Strategy:
This stage ensures the strategy is in sync with the objectives of the business to add value to the services delivered to customers.
b) Service Design:
This phase concerns the services designed and introducing supporting elements into the live environment. When designing a service, you must consider the four Ps of Service Design (People, Processes, Products, & Partners).
c) Service Transition
Service Transition is a stage to ensure that the changes to management and service processes are carried out in an organised way. This process coordinates to build and deploy IT services.
d) Service Operations
This stage balances costs and unearths any potential problems to meet customer expectations. This is the only phase which involves both functions and processes. Service Operations also include resolving service failures, realising user requests, fixing problems, and running regular operational functions.
e) Continual Service Improvement
The main agenda of this stage is to analyse the methods used earlier to reflect and learn from the previous success and failures. It aims at improving the quality management and overall effectiveness of IT processes and services.
Each major category of the ITIL Lifecycle has a certain number of subcategories, as mentioned in the image above.
7) What is ITIL Service Desk and explain its benefits?
ITIL service desk is the point of contact between the service provider and users. It serves as a communication point for users to report operational problems, questions, and other requests. The service desk must possess excellent customer service abilities like empathy and emotional intelligence in order to succeed.
The major benefits of ITIL service desk are listed below:
a) Higher first call resolution rate
b) Skill-based assistance
c) swift restoration of service
d) Improved reaction time to risks
e) Improved service quality monitoring
f) Enhanced identification of trends and risks
g) Improved employee satisfaction
h) Rapid service restoration
8) What do you Understand by SLA?
SLA is an acronym for Service Level Agreement. It refers to the commitment between a service provider and the end user or client. SLA represents the level of service assumed by the external/internal service provider.
It emphasises the standards of service that the customer expects from the provider, the factors that determine if success is achieved, and the consequences or remedies that the service provider would face if the standard of service isn't fulfilled.
9) What does SACM stand for?
SACM stands for Service Asset and Configuration Management. It primarily deals with maintaining and verifying assets and database, which are also made accessible to other processes.
10) Explain the Service Value System.
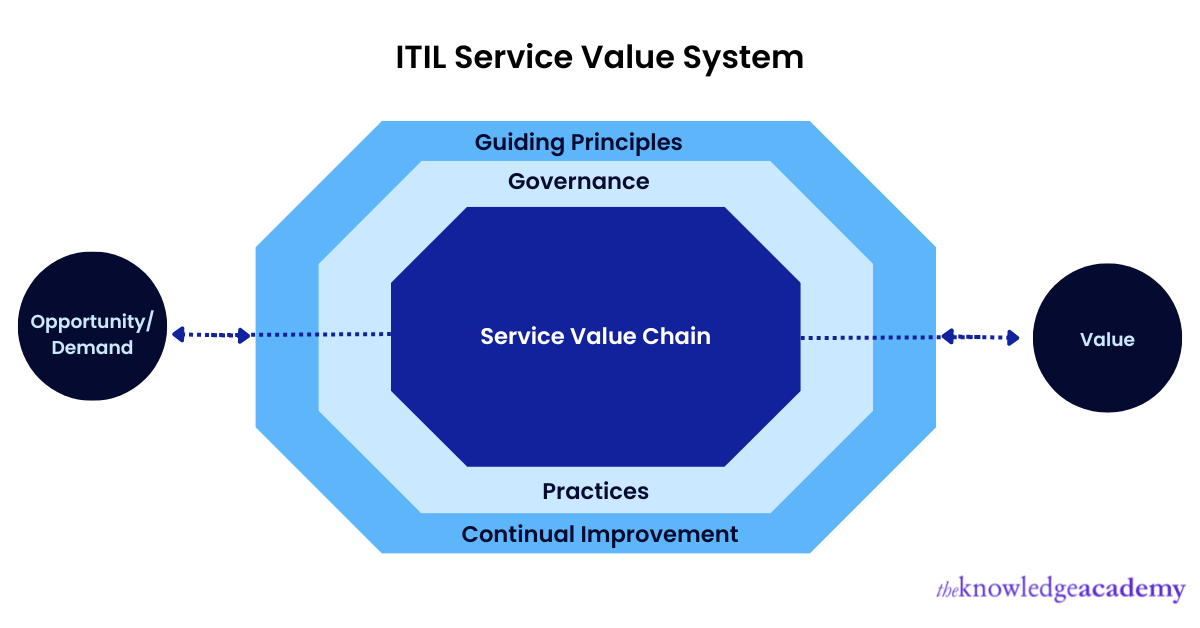
The various elements and activities that work together to produce value are represented by the Service Value System. These consist of relevant ITIL service management inputs, elements, outputs, and other components.
a) Guiding principles - Organisation can use these principles in every situation, regardless of its objectives, goals, strategies, type of work, management style, or structure.
b) Governance: It provides a structure that will aid the organisation in establishing and preserving control. Every investment the company makes is intended to add value and guarantee that it will achieve its business goals.
c) Service Value Chain: It is a method for developing, providing, and constantly enhancing services. It comprises six activities that can all be integrated in various ways to produce various value streams.
d) Practices: These are a set of resources that are used to carry out specific task or achieve specified goals.
e) Continual Improvement: It focuses on improvement through increasing the effectiveness and effectiveness of the service while cutting costs associated with resources, services, and other IT management strategies.
11) What is Utility?
Utility is the requirement to satisfy a certain market by a service or a product. It examines a certain service's functionality to see whether it is "suited for its purpose.”
12) What Processes are utilised by the ITIL Service Desk?
The processes utilised by ITIL service desk are workflow and procedure diagrams.
13) Mention the goals of Problem Management in ITIL
The main goals of Problem Management in ITIL are, which encompass the ITIL Problem Management roles and responsibilities, are:
a) To identify recurring incidents
b) To recognise the reason or cause of the incidents that occurred
c) To prevent such incidents from happening in future
14) What are the key steps involved in the Problem Management Process?
The key steps involved in the problem management process are:
a) Identification of the problem
b) Classification of the problem and prioritizing it
c) Determining root cause of the problem
d) Find a workaround for the problem
e) Creation of a known error record
f) Resolving
g) Closing the problem
h) Examining the problem
15) What is ITSM?
ITSM stands for Information Technology Service Management. This includes a set of activities used by an organisation to plan, design, build, deliver, operate, and support IT services that are offered to customers.
16) List a few ITIL-Based Models that organisations have adopted.
a) Microsoft - MOF
b) Hewlett – Packard (HP ITSM Reference Model)
c) IBM - (IT Process Model)
17) What are the ITIL® 4 Ps?
a) People: These refer to people involved in the processes and procedures.
b) Processes: The company's capacity to put processes in place.
c) Products: These emphasise the service and the technology that supports it.
d) Partners: The parties who collaborate with the IT department to make sure the service is reliable.
18) Explain a known Error in ITIL.
A known error in ITIL refers to an identified problem whose root cause and solution are analysed. But the problem is not fixed. It consists of these:
a) Status
b) Error description
c) Root cause
d) Workaround
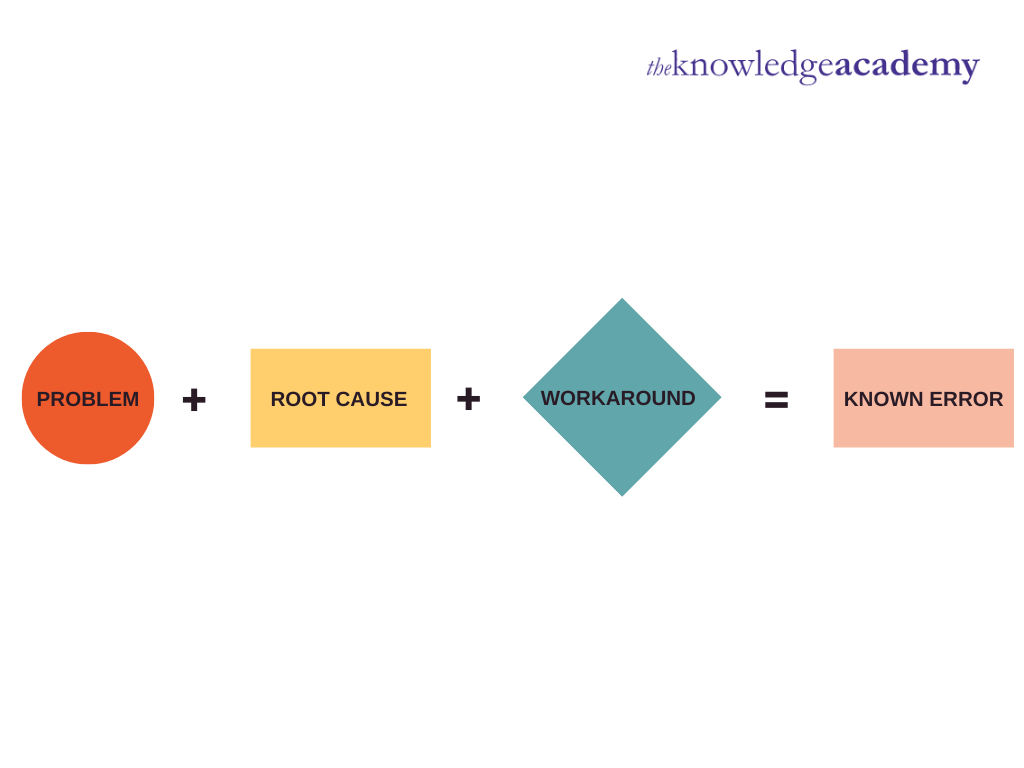
Problem + Root Cause + Workaround = Known Error
19) How can you close a known Error?
You can close known errors based on these conditions:
a) When all Request for Change (RFC) are closed.
b) The known error must have root cause, solution, and workaround.
c) When a record is found in the error closure phase.
ITIL Interview Questions for Intermediate Professionals
20) What are the objectives of Incident Management?
The main objectives of Incident Management are:
a) To identify, report, and solve the incidents that can occur in IT services.
b) Strive towards achieving customer satisfaction.
c) Effectively align activities of incident management.
d) To ensure efficient and regulated methods are used to prevent future incidents.
e) To ensure that the documentation, response analysis, and operational management follows the approved or appropriate methods.
21) List the objectives of IT Service Continuity Management.
The main objectives of IT Service Continuity Management are:
a) Effectively analyse the involved risks
b) Test the status of backup preparations for handling the situations
c) Finalise the adequate backup service arrangements
22) What is Configuration Management’s purpose in ITIL?
The purpose of Configuration Management is to receive, collect, store, manage, and verify the data from IT assets.
23) What is the difference between a Project and a Process?
The main difference noticed between a Project and a Process is Timespan. A project has a fixed time with a definite start and end point. At the same time, a Process is usually continuous or repetitive without a definite start and an endpoint.
Process Management will produce recurring results, such as working on ongoing strategies. In comparison, Project Management will involve one-time events or tasks with a fixed time constraint.
24) Give the difference between customers and end-users.
End-users are the actual recipients of services or goods, whereas customers are entities with the ability to select products from suppliers.
A customer is a person who establishes the requirements for a service or product. An end-user or end customer direct receives a product or service or directly receives or uses the product.
25) When is a known error recognised?
Known error can be recognised when the root cause of the problem is determined.
26) Describe the differences between incidents, problems, and known errors.
a) Incident – It refers to an event that results in unplanned disruptions to an IT service. These events were not expected during the planning stage and were not intended to be a part of the standard operation. ITIL Incident management focuses on resolving the issue right away to get the user back on track.
b) Problem – It refers to the underlying cause of one or more incidents which is still unknown. Problem management refers to finding the root cause for the issue.
c) Known error - A problem that has already been identified and for which a workaround or long-term solution has been determined is referred to as a known error.
27) Explain different types of SLA.
The three types of Service Level Agreements (SLA) are:
a) Customer Service Level Agreement: It exists between the service provider and the external customer.
b) Internal Service Level Agreement: It exists between the service provider and an internal customer, which could be a department
c) Vendor Service Level Agreement: It exists between the developer and the vendor.
28) What is the significant difference between ITIL v2 and ITIL v3?
Below are the important differences between ITIL v2 Vs. ITIL v3 are:
|
ITIL v2 |
ITIL v3 |
|
Follows a process-oriented approach |
Follows a lifecycle-based approach |
|
Focus on product, process, and people |
Focus on product, process, people, and partners |
|
High focus on design and strategy |
Uniform focus on all processes |
|
Consists of 10 processes and two functions |
Consists of 26 processes and four functions |
|
Security Management is made part of the assessment |
Security Management is a completely different process |
29) How are ICT and BCP related?
The Business Continuity Plan (BCP) is a structured methodology or a process to predict, prevent, and control Information and communication technology (ICT). It is significant that every agency includes, validates, and maintains ICT Disaster Recovery (ICT DR) and BCP to mitigate ICP-related disruptions.
In the event of any disaster or disruptions, the ICT and BCP can help the agencies recover and function effectively.
30) Explain Event Management in ITIL.
Event Management is a process that keeps an eye on all the events that occur inside the IT Infrastructure of an organisation. It continually monitors to detect, filter, and report any exceptional conditions.
31) List the different Knowledge Management Systems.
Here is a list of different ITIL Knowledge Management Systems:
a) AMIS (Availability Management Information System)
b) CMDB (Configuration Management Database)
c) CMIS (Capacity Management Information System)
d) DML (Definitive Media Library)
e) KEDB (Known Error Database)
f) SKMS (Service Knowledge Management System)
32) What is the RACI Model?
The RACI Model is a tool that makes it simple to identify various roles and responsibilities during a project. RACI stands for:
a) Responsible: The responsibilities of an individual to complete the assigned job. They are given responsibilities in accordance with their tasks.
b) Accountable: The person or people in charge of carrying out specific task accurately and completely.
c) Consulted: The group or individual that is consulted for the completion of a task.
d) Informed: People who are kept up to date on the task's progress. In this case, the communication is usually only one-way.
33) What are the Service Value System's guiding principles?
Guiding principles are established to direct the organisation's decisions and actions. Regardless of the scenario, objective, goal, strategy, work style, management, or organisation, these principles apply. The seven guiding principles are:
a) Focus on value
b) Progress iteratively with feedback
c) Collaborate and promote visibility
d) Start where you are
e) Optimize and automate
f) Keep it simple and practical
g) Think and work holistically
34) What is ISO/IEC 27002?
Information Security Standard ISO/IEC 27002 was created by ISO and IEC. It places a significant emphasis on best practices, particularly
Give a kick-start to your career by becoming an ITIL Specialist – Register for our ITIL Certification today!
35) What are 7R’s of Change Management?
Organisations can implement changes using ITIL® Change Management without experiencing any downtime or any other disruptions. The 7R’s are:
a) Who Raised the change?
b) What’s the Reason for the change?
c) What Return will the change deliver?
d) What Risks are there if we do or do not carry out the change?
e) What Resources will be required to perform this change?
f) Who is Responsible for this change being performed?
g) What Relationships are there between this and other changes?
36) What distinguishes Utility from Warranty?
|
Utility |
Warranty |
|
A service or product's utility is its capacity to meet a certain need from the customer perspective. |
A warranty is a promise that a service or product will meet predetermined requirements. |
|
The utility must fit the intended purpose and satisfy customer requirements. |
Warranty is concerned with how service delivered. |
|
Utility has the potential to raise performance standards. |
Warranty operates the function of the service. |
|
Utility provides an answer to "what the product achieves" or "whether the service is up to standard." |
A product's "fitness for use" or "how well the service performs" are insured by the warranty. |
|
Utility deals with what the customer will get. |
Warranty may help to minimise performance variance. |
37) What is Service Transition?
The service transition is the third stage of the ITIL service lifecycle. The aim of this stage is to build and deploy IT services for various organizations. Enterprises can ensure continuous service improvement and operations by using the methods and procedures of ITIL Service Transition. This phase is also in charge of making sure that modifications to services and service management procedures are carried out in a coordinated manner. The processes included are:
a) Change Management
b) Change Evaluation
d) Application Development
f) Service Validation and Testing
g) Service Asset and Configuration Management
h) Knowledge Management
The ITIL Service Transition Process is focused on developing and implementing IT services.
Learn how you can successfully engage clients and stakeholders using ITIL – Register in ITIL 4 Specialist: Drive Stakeholder Value
ITIL Interview Questions for Experienced Professionals
38) What is the objective of Change Management in ITIL ®?
The main objective of Change Management is to effectively control and manage the change requests to mitigate the risks and disruptions by establishing standard policies and procedures.
39) Explain Capacity Management’s main objectives and mention its sub-processes.
Capacity Management is a process used to predict resource demands and strategically allocate them in a cost-effective manner. The main objective of ITIL Capacity Management is to ensure that adequate capacity is always available to match the agreed needs of the business within budget constraints.
Capacity Management has three sub-processes that are:
a) Business Capacity Management
b) Service Capacity Management
c) Component Capacity Management
40) Define Operational Level Agreement (OLA).
The Operational Level Agreement (OLA) represents the interdependent relationships between the internal support group (such as an IT service provider) and the other support groups (like the process and timeframe for delivery) of the IT organisation.
41) Explain the difference between ITIL and COBIT.
|
ITIL |
COBIT |
|
ITIL is the acronym for Information Technology Infrastructure Library. |
COBIT is the acronym for Control Objectives for Information and Related Technologies. |
|
It is a set of guidelines for the managing IT services. |
It is a framework for integrating information and technology. |
|
Provides the ability to put the company's policies into action. |
Allows the creation of business norms. |
|
Features include: a) Service strategies b) Design, transitions c) Operation implementations |
Features include: a) Control objectives b) Management guidelines c) Maturity models. |
42) What are the Responsibilities of Service Desk?
The responsibilities of service desk include:
a) To log, categorise and prioritise incidents
b) To find and resolve incidents
c) To manage risks
d) Create incident management report
e) To restore normal operations when disruptions occur
f) To escalate requests to support other IT Service Management activities and processes.
43) Which is the most popular web-based service desk tools?
Most popular web-based service desk tools are:
a) CA service desk
b) Tivoli
c) Bugzilla
d) Oracle Service Cloud
e) SolarWinds Web Help Desk
f) Help Scout
g) JIRA Service Management
h) ServiceNow
i) BMC
j) Spiceworks Help Desk/Cloud Help Desk
k) C-Desk
l) OTRS Free
m) HappyFox
n) Salesforce Service Cloud
o) SysAid.
p) Vivantio
q) Zoho Desk
44) Who holds the responsibility of protecting and maintaining the known Error Database?
The Problem Manager is in charge of keeping the Known Error Database safe and secure as well as starting the official closure of all Problem entries.
45) Mention layers of Service Management Measurements.
Service Management Measurements has five layers, that are:
a) Progress:
Responsible for managing the progress of the existing services.
b) Compliance:
It is concerned with the processes trending in the industry and compliance with market standards.
c) Effectiveness:
This measurement calculates the effectiveness of the services.
d) Efficiency:
It deals with workflow efficiency and continuity of services.
e) Productivity:
This measurement calculates the productivity of the existing services.
46) Mention the applications of ITIL.
The fundamental areas where ITIL plays an important role are:
a) IT and strategic business planning
b) Assisting in Development and Testing
c) Design and Portfolio planning
d) Implementing Continuous improvement strategies
e) Aids in measuring the effectiveness and efficiency of IT organisations
f) Reducing unnecessary costs
g) Managing and retaining the right resources and skillsets
47) Define service reporting.
Service reporting primarily deals with building and delivering reports of trends and achievements in an agreed format and frequency against the Service Levels.
48) Explain RACI-VS.
RACI-VS refers to: Verifies Sign off – It is the person who ensures that the acceptance criteria have been met and gives the sign off to the project.
49) List the Common Workaround Recovery Options.
Common Workaround Recovery Options are classified as:
a) Manual workaround
b) Reciprocal arrangements
c) Gradual recovery
d) Intermediate recovery
e) Fast recovery
f) Immediate recovery
50) Why is Service Transition used?
The service transition is used for the following:
a) To provide high-quality information on change
b) To plan and oversee the capability, resources, and requirements needed to complete a release.
c) To manage the risks connected to newly added, upgraded, or discontinued services.
d) To check to see if the service adjustments are giving the company the expected value.
e) It ensures that recently introduced or modified services are easy to maintain and cost effective.
51) What is Configuration Baseline in ITIL?
In ITIL®, a configuration baseline is a setup that has been specifically agreed upon, monitored through a board cycle modification, and is exclusively used for that setup. It is controlled by the change management process.
52) What is work-around?
A workaround offers a short-term solution for problems for which the underlying root cause has not yet been addressed. A workaround's duration is typically not specified and could be anywhere from a few seconds to many years.
53) Define Post Implementation Review.
The final working solution is assessed and analysed in the post-implementation review, or PIR. Following the submission of a change request, a review is conducted to determine whether the change and its implementation were effective. PIR assists in determining whether a change has effectively addressed the issue it set out to solve. It answers these questions:
a) Did the change solve the aimed problem?
b) Has the change affected the customers?
c) Was the method effective in allocating resources?
d) Was the change carried out on schedule and within budget?
Begin your career in IT Service Management – Register in ITIL® 4 Foundation Certification Training Course today!
Scenario based Interview Questions and Answers
54) How does ITIL help minimise the Total Cost of Ownership (TCO) for IT investments?
The staff of IT organisations have found that the regular work schedule gets disrupted often due to the unscheduled work taking priority over the planned work. Hence, ITIL can help an organisation break this cycle and therefore aid the employees to focus on the Total Cost of Ownership (TCO) and the respective job roles or activities per their departments.
55) How Crucial is Information Security Policy in ITIL?
The Information security policy protects the information and data of the organization from security risks or cyber threats. Data leaks and breaches are security disasters that quickly damage consumer trust. This kind of incident can be avoided with the use of a strong information security policy while retaining client confidence.
56) Why are Information Security Management Systems necessary?
Information security management systems ensure that information is effectively managed across services and service management activities while also assisting in the alignment of business and IT security. These guarantee that information is accessible and used when necessary. It also helps with:
a) To make sure that these systems can resist, recover quickly, or avoid failures.
b) Only those who have a right to know have access to information.
c) The information is accurate, updated, and secure from unauthorised access.
d) Information communication and commercial interactions are trustworthy.
57) What are the five characteristics of information assets in IT Security Management?
In IT security management, information assets have the following five characteristics:
a) Confidentiality: This guarantees that only one person has access to the asset.
b) Integrity: It makes sure that no unapproved party has altered any asset.
c) availability: ensures the availability of the asset that can be used when necessary.
d) Authenticity: Assures that the parties' identities are real.
e) Nonrepudiation: It assures that once a transaction is finished, it cannot be undone without permission.
58) How does the Incident Management System work?
The incident management controls the flow of incident information, along with:
a) Recording incidents
b) Classifying the incidents based on their impact and urgency
c) Authorizes the incident to the relevant member
d) Resolution and recovery after the occurrence of the incident
59) Why do we need to ‘engage’ as part of the Service Value Chain?
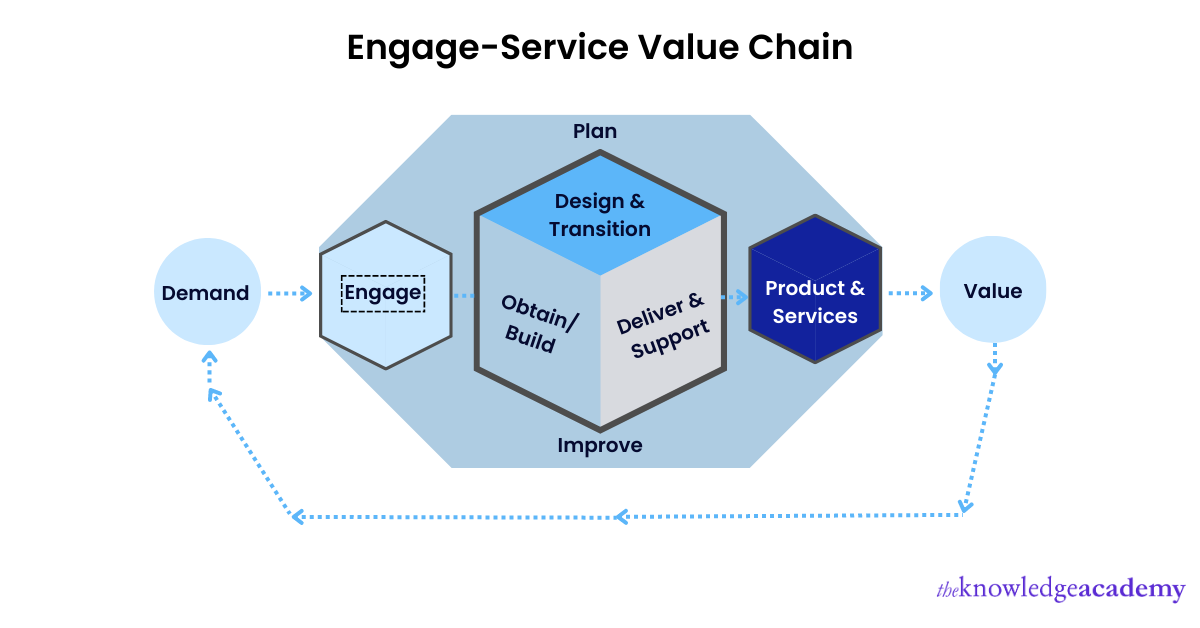
The Engage component in the ITIL4 Service Value System provides an understanding of needs, regular engagement, maintaining transparency, and having a good relationship with the stakeholders.
60) Differentiate between a service request and an incident.
The Service request is a request raised by a user in a formal way to receive information, advice, or access to a service.
An incident is an unplanned interruption or disruption of an IT service hindering the operations and quality of the work.
61) What is Service Strategy?
Service Strategy is a set of policies and strategic decisions to determine and deliver the targeted services to achieve a deliberate goal.
62) Name the four Ps of Service Strategy.
The four Ps of a Service Strategy in ITIL are:
a) Perspective
b) Position
c) Plan
d) Pattern
63) Explain Service Portfolio, Service Catalog, and Service Pipeline.
a) The service portfolio contains all the information related to the IT services provided by a service provider across the organization.
b) The service catalog consists of lists to active services with the help service design package. It is the subset of service portfolio. It consists of services ready to be Offered to customers.
c) The Service pipelines are references to services that are not yet operational. These plans might already exist or be under development.
64) What do you understand by Change Advisory Board (CAB)?
A change advisory board refers to group of powerful individuals who support the execution of the change management process by approving, evaluating, prioritising, and scheduling the requested changes. They are responsible for evaluating all high-impact Requests for Change from both a commercial and technical standpoint.
65) Provide examples of Proactive Problem Management.
The examples for proactive problem management are pain value analysis and trend analysis.
66) Explain freeze period in ITIL.
Freeze period in ITIL is referred to a particular time period in the development procedure, after which severity and strictness are observed in the rules. Rules are required for making changes to the source code.
67) What does a balanced scorecard aim to achieve?
A balanced scorecard's aim is to turn an organisation's mission and vision into concrete steps. It is a strategic planning and management approach used to identify and enhance different internal organisational functions and the outcomes they provide.
68) What is a warranty?
Warranty is the assurance that an organisation or service provider gives the customer that the product or service will meet the agreed standards and requirements for a particular period. Warranty focuses on a product's performance, quality, continuity, capacity, and security to determine if it is ‘fit for use’.
69) What is an IT asset?
IT asset typically includes financially valuable components owned by the company, such as software, hardware, cloud services, networking, and others, which can contribute to the delivery of an IT product or a service (business activities).
70) Explain the Plan-Do-Check-Act (PDCA) cycle.
The PDCA cycle is used by businesses to manage, control, and keep up with the continuous improvement of their products and services. Now let us understand the parts of the PDCA cycle.
Plan:
All kinds of planning for improvements are done at this stage. Improvements can be planned to reduce the gap after performing a gap analysis.
Do:
All the improvement plans are implemented at this stage to close the gap identified in the previous phase.
Check:
The results obtained here by monitoring, measuring, and reviewing are compared to the success factors, discussed in the planning stage.
Act:
At this stage, the determined improvements are successfully implemented.
71) Why do we need Relationship Management?
Relationship Management aims to ensure that the relationship between the service provider and the customer is established and maintained. It helps to provide quality products and services while retaining trust to improve the relationship.
72) Explain the difference between Emergency Changes and Urgent Changes?
The differences between emergency changes and urgent changes are as follows:
a) Emergency changes are the highest priority changes in an organisation that needs to be implemented quickly.
b) Urgent changes are changes that meets a critical business or legal requirement but isn’t related to restoring service.
73) Explain CSI
CSI in ITIL refers to Continuous Service Improvement. CSI is the final stage in the ITIL service Lifecycle, focusing on aligning the services with the change in business needs. It is a routine organisational activity performed to identify and implement improvements to the IT services according to the stakeholders' expectations.
74) List down the 7 steps involved in CSI.
Following is the list of 7 steps involved in Continuous Service Improvement (CSI):
a) Identify improvement strategies
b) Define what will be measured
c) Gather data
d) Process data
e) Analyse data
f) Presenting and using the information collected
g) Implement action for improvement
75) What is Financial Management?
ITIL Financial Management is one of the main processes of the Service Strategy stage This stage mainly deals with the following financial requirements:
a) Accounting
Responsible for generating business reports by performing cost analysis on the profitability of services.
b) Budgeting
Responsible for allocating necessary funds and costs for the business to function and perform the services with proper financial planning.
c) Charging activities
Providing invoices for the services accepted by the customer.
76) What are the various types of service providers in ITIL processes?
Below is a list of various types of ITIL service providers:
a) Internal Service Provider
Internal Service Providers (ISPs) are service providers that provide services within the individual business unit.
b) External Service Provider
External Service Providers (ESPs) are service providers that provide IT services to external customers.
c) Shared Services Unit
Services of shared functions of an organisation (such as finance, IT, HR, and logistics) are consolidated into a particular independent unit called Shared Services Unit (SSU).
77) Explain how availability, agreed service time, and downtime are related.
Availability: Ability of an IT service or configuration to perform the expected functions as and when required.
Agreed Service Time: Expected time of service to be operational as agreed.
Downtime: It is the duration; your service is not operational as per the Agreed Service Time.
78) Explain the objective of ‘design and transition’ on the Service Value Chain.
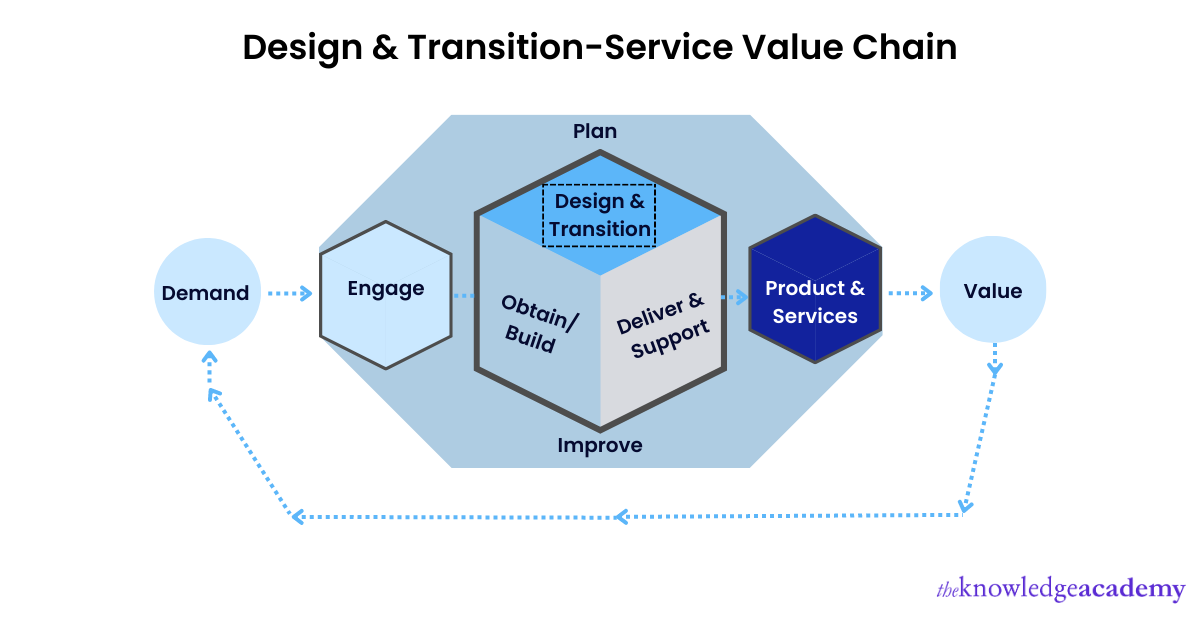
The main objective of the design and transition component in the ITIL Service Value Chain is to ensure that the products and services match the stakeholders' expectations for cost, quality, and marketing time.
79) What is the purpose of the deployment management practice?
The purpose of deploying the management process is to plan, organise, and control the deployment of releases that are built, updated, and tested to deliver the expected functionality required by the business.
80) What is CSF?
CSF stands for Critical Success Factors, referring to steps or measures taken to enhance the performance and success rate of the business. CSFs are the elements that are significant for a strategy to be successful in achieving a determined objective.
Learn how to create impactful digital strategies – Register for ITIL® 4 Foundation Bridge Training today!
Conclusion
We have discussed the most commonly asked ITIL interview questions and their answers in this blog. This blog will help you prepare for cracking the ITIL interview and securing job in your dream company. Let us know in the comments below if you have any doubts or questions.
Understand the key concepts of Direct, Plan & Improve – Register for ITIL® 4 Strategist: Direct, Plan And Improve DPI Today!
Frequently Asked Questions
Upcoming IT Service Management Resources Batches & Dates
Date
 ITIL® 4 Foundation Certification Course
ITIL® 4 Foundation Certification Course
Mon 29th Apr 2024
Wed 1st May 2024
Sat 4th May 2024
Tue 7th May 2024
Thu 9th May 2024
Mon 13th May 2024
Wed 15th May 2024
Sat 18th May 2024
Mon 20th May 2024
Wed 22nd May 2024
Tue 28th May 2024
Thu 30th May 2024
Mon 3rd Jun 2024
Wed 5th Jun 2024
Mon 10th Jun 2024
Wed 12th Jun 2024
Sat 15th Jun 2024
Mon 17th Jun 2024
Wed 19th Jun 2024
Mon 24th Jun 2024
Wed 26th Jun 2024
Sat 29th Jun 2024
Mon 1st Jul 2024
Wed 3rd Jul 2024
Mon 8th Jul 2024
Wed 10th Jul 2024
Sat 13th Jul 2024
Mon 15th Jul 2024
Wed 17th Jul 2024
Mon 22nd Jul 2024
Wed 24th Jul 2024
Sat 27th Jul 2024
Mon 29th Jul 2024
Wed 31st Jul 2024
Mon 5th Aug 2024
Wed 7th Aug 2024
Sat 10th Aug 2024
Mon 12th Aug 2024
Wed 14th Aug 2024
Mon 19th Aug 2024
Wed 21st Aug 2024
Sat 24th Aug 2024
Tue 27th Aug 2024
Thu 29th Aug 2024
Mon 2nd Sep 2024
Wed 4th Sep 2024
Sat 7th Sep 2024
Mon 9th Sep 2024
Wed 11th Sep 2024
Mon 16th Sep 2024
Wed 18th Sep 2024
Sat 21st Sep 2024
Mon 23rd Sep 2024
Wed 25th Sep 2024
Mon 30th Sep 2024
Wed 2nd Oct 2024
Sat 5th Oct 2024
Mon 7th Oct 2024
Wed 9th Oct 2024
Mon 14th Oct 2024
Wed 16th Oct 2024
Sat 19th Oct 2024
Mon 21st Oct 2024
Wed 23rd Oct 2024
Mon 28th Oct 2024
Wed 30th Oct 2024
Sat 2nd Nov 2024
Mon 4th Nov 2024
Wed 6th Nov 2024
Mon 11th Nov 2024
Wed 13th Nov 2024
Sat 16th Nov 2024
Mon 18th Nov 2024
Wed 20th Nov 2024
Mon 25th Nov 2024
Wed 27th Nov 2024
Sat 30th Nov 2024
Mon 2nd Dec 2024
Wed 4th Dec 2024
Mon 9th Dec 2024
Wed 11th Dec 2024
Sat 14th Dec 2024
Mon 16th Dec 2024
Wed 18th Dec 2024







 Top Rated Course
Top Rated Course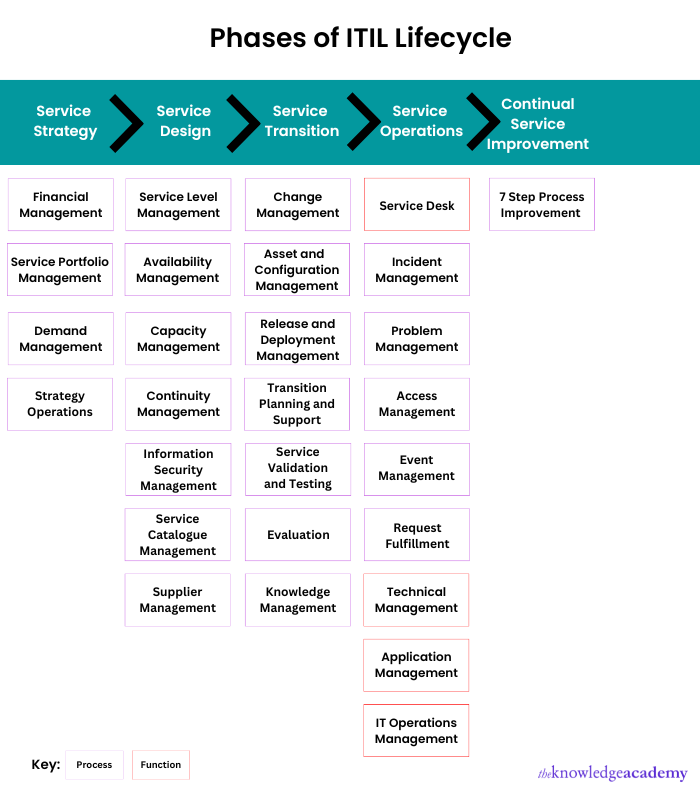




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


