Plymouth is located within the county of Devon and has a population of around 250,000 inhabitants. The city is south west of London and is located on the river Plym and Tamar. Plymouth has been named the 30th most popular place to live in the United Kingdom. Plymouth is known for its shipping port by handling exports and imports, the city offers shipbuilding and major ferry links. There are around 8.9% inhabitants unemployed within Plymouth, the national average is 7.3%.The United Kingdom’s 9th largest university is the University of Plymouth with a staggering 26,000 students. The university has its main campus in Plymouth and several all over south west England. With around 2,000 staff members the university is the largest employer within the county. Students are offered graduate and undergraduate courses including, law, psychology, geographical science and computing.
Popular searched areas in and around Plymouth include:-
- Beacon Park
- Bickleigh
- Brixton
- Crabtree
- Derriford
- Devonport
- Ford
- Greenbank
- Hartley
- Mount Batten
- Mountbatten
- Mutley
- Newton Ferrers
- Noss Mayo
- Plympton
- Plymstock
- Saltram
- Stoke
- Stonehouse
- Wembury








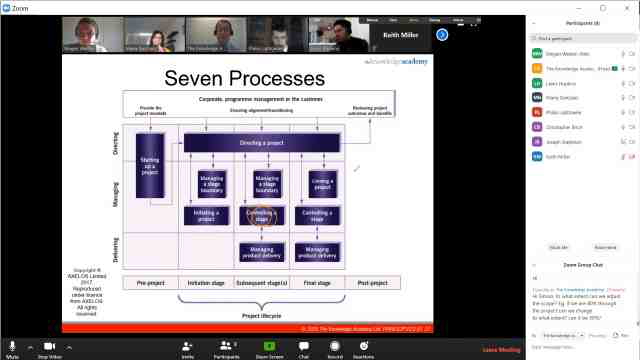
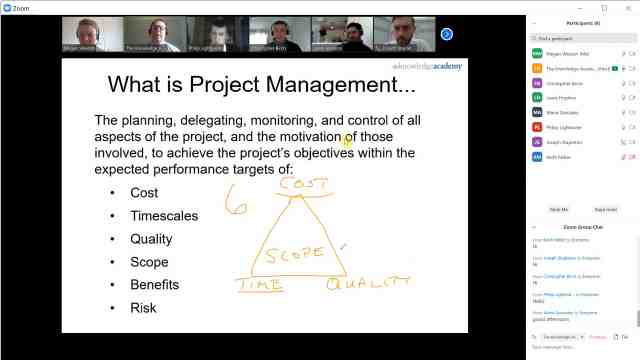
























 Back to course information
Back to course information




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please

