We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Data is arguably the most critical resource in today's data-driven modern organisations. However, its sensitivity makes it vulnerable to advanced cyber-attacks. To help protect their data, organisations must adopt global standards such as ISO 27001 standard that validates an organisation's approach toward protecting information. However, merely adopting the standard doesn’t fulfil the purpose, one of the essential requirements to comply with the standard is Performing ISO 27001 Penetration Testing.
According to the UK Government’s Cyber Security Breaches Survey 2023 32% of businesses have faced any breaches or attacks in 2022. To protect from these breaches the global standard in Cybersecurity, ISO 27001 can greatly help in reducing these numbers. But here the catch, to comply with this standard, an organisation must fulfill the ISO 27001 Penetration Testing requirements Want to know how one can fulfil these requirements? In This blog, we will explain how ISO 27001 Penetration Testing can improve the effectiveness of your organisation's information security controls. Keep reading to learn more!
Table of Contents
1) What is Penetration Testing?
2) What are the requirements for ISO 27001 Penetration Testing?
3) Why is Penetration Testing important for ISO 27001 compliance?
4) What are the types of Penetration Testing?
5) What are the benefits of Penetration Testing?
6) Who would need to conduct Penetration Testing?
7) Alternatives to Penetration Testing
8) How to define the scope of an ISO 27001 Penetration Test?
9) How frequently should you conduct ISO 27001 Penetration Testing?
10) Conclusion
What is Penetration Testing?
Let's start with a brief introduction to ISO 27001 before delving deeper into Penetration Testing. The ISO 27001 framework is a top global standard for Information Security that offers a path for organisations to protect their data.
ISO 27001 Compliance not only equips businesses with the knowledge to secure their data but also assures their clients of their commitment to data security. To maintain compliance with ISO 27001, businesses must adhere to several requirements, including Penetration Testing. This critical risk management technique, alongside vulnerability scanning and security testing, simulates data breaches and attacks through ethical hacking to verify the effectiveness of the organisation's incident response and security controls.
During the Penetration, security policy experts identify security vulnerabilities in a simulated environment to improve security measures. While a simple vulnerability assessment can suffice in some systems, standard scanning tools may not recognise certain vulnerabilities, even those specifically designed for web applications. Therefore, ISO 27001 Penetration Testing is necessary to verify all aspects of Information Security.
What are the requirements for ISO 27001 Penetration Testing?
According to the ISO 27001:2013 controls outlined in Annex A, it is stipulated that information pertaining to technical vulnerabilities in Information Systems must be regularly acquired as part of the ISO 27001 controls framework. The organisation’s exposure to such vulnerabilities must be evaluated, and appropriate measures must be taken to address the associated risk.”
Penetration Testing fulfils these requirements by providing a gap analysis in the form of a simulated malicious attack. The Testing should be conducted by certified professionals who offer Testing services. The non-conformity findings help one determine the corrective actions to improve an organisation’s existing Information Security controls.
Why is Penetration Testing important for ISO 27001 compliance?
Conducting effective Penetration Testing comprises simulating a malicious attack on the security systems being assessed, typically utilising a range of techniques and tools. Certified ethical professionals carry out these tests, and the results serve as a basis for enhancing security measures.
Penetration Testing plays a vital role in the ISO 27001 Information Security Management System (ISMS) at all stages, from initial development to ongoing maintenance and continuous enhancement. ISO 27001 control objective A12.6, i.e., Technical Vulnerability Management, specifies that organisations must promptly acquire information about technical vulnerabilities in their Information Systems, assess the organisation'’s vulnerability to these issues, and implement appropriate measures to mitigate the associated risks.
What are the types of Penetration Testing?
Several types of Penetration Testing engagements vary in emphasis, depth, and duration. Understanding the different types of Penetration Testing before implementing them into an organisation’s Risk Management process is crucial. The following are some typical ethical hacking projects:
1) Internal and external Infrastructure Vulnerability Testing: This type of Penetration Testing requires a thorough review of both on-premises and on-cloud components – such as the network infrastructure, including routers, switches, and system hosts.
2) Testing for wireless Penetration: Wireless penetration testing must be done by evaluating the number of wireless and guest networks, locations, and distinct Service Set Identifiers (SSID). Wireless penetration tests focus on Wireless Local Area Networks (WLAN) and aid in identifying malicious access points, encryption errors, and Wi-Fi Protected Access (WPA) vulnerabilities.
3) Testing of Web Applications: Web application testing involves the examination of web applications to identify code and design errors that could potentially be exploited. This type of Penetration Testing identifies the number of applications that require testing, the number of static and dynamic pages, as well as input fields that require evaluation before implementing test procedures.
4) Testing mobile applications: Mobile application testing helps identify issues with session handling, data leaks, authentication, and authorisation. Testers need to be aware of the types and versions of Operating System(OSs), as well as the number of Application Programming Interface (API) calls.
5) Review of build and configuration: A detailed review of network builds, and security is needed to find configuration errors in web and app servers, routers, and firewalls. To be able to do this, one needs to know the number of builds, Operating Systems, and application servers that are set to be examined.
6) Social Engineering: Social engineering evaluates an organisation’s employees’ ability to recognise and respond to e-mail phishing attempts. This type of Penetration Testing uses targeted phishing, spear phishing and Business E-mail Compromise (BEC) attacks to gain detailed information about the possible threats.
7) White Box Testing: White-box penetration Testing provides a Tester with advanced network operation know-how to facilitate more direct testing.
8) Black Box Testing: A Black-Box penetration test does not provide the Tester with any information but instead simulates an attack’s strategy from initial access and execution to exploitation. It is more time-consuming and costly than all the methods.
9) Gray Box Testing: As the name suggests, only a partial amount of information is disclosed to the Tester for a Gray-Box Test. Gray Box Tests offer a middle ground between depth and efficiency.
Attain in-depth knowledge about ISO 27001 for Information Security Management with our ISO 27001 Lead Auditor Course now!
What are the requirements for ISO 27001 Penetration Testing?
The ISO controls set of Annex A (ISO 27001:2013) says that information about the information systems’ technical vulnerabilities must be obtained in regular intervals. The organisation’s exposure to such vulnerabilities must be evaluated, and appropriate measures must be taken to address the associated risk.”
Penetration testing fulfils these requirements by providing a gap analysis in the form of a simulated malicious attack. The testing should be conducted by certified professionals who offer testing services. The nonconformity findings help one determine the corrective actions to improve an organisation’s existing information security controls.
How does Penetration Testing work?
Penetration Testing may include external tests to detect IP address issues or web application vulnerabilities. It also includes internal tests that analyse your network devices and Operating Systems to identify internal vulnerabilities, such as weak passwords, outdated software, badly coded sites, and insecure applications.
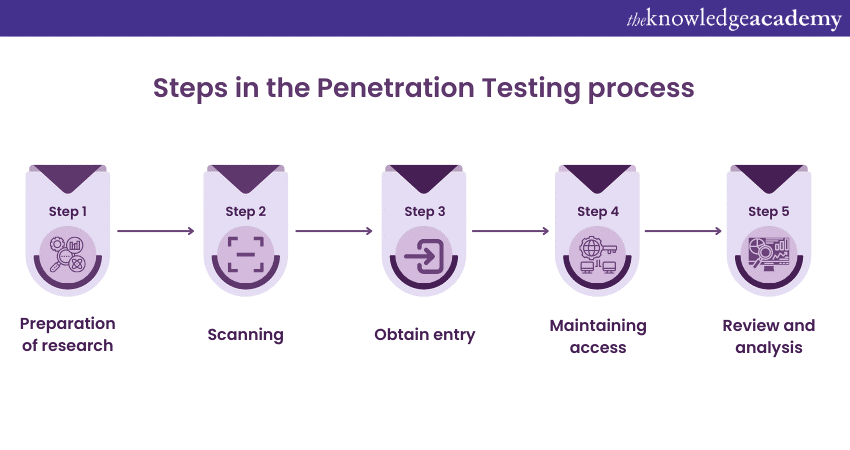
Preparation and research
The first stage of the process establishes the scope and objectives, along with the systems to be tested and the Testing techniques. It collects information to learn more about a target application’s operations and potential areas of weakness.
Scanning
The next step in the process is to know the reaction of the target application to various cyber-attacks. Usually, this is achieved by using two types of analysis: static and dynamic.
Static analysis requires one to analyse the source code of a program to predict its function when executed, and the entire code can be scanned in a single attempt. Dynamic analysis requires an examination of the code of a running application, and it is more helpful as it provides a real-time analysis of an application’s work.
Obtain entry
This step is about identifying a target application’s weaknesses by simulating web application attacks like cross-site scripting, SQL injection and backdoors. Testers attempt to exploit these weaknesses by elevating their privileges, stealing data, and intercepting communications – to understand the level of harm, these vulnerabilities may do.
Maintaining access
This step aims to determine whether the vulnerability can be used to establish a presence in the system long enough for a malicious factor to gain access. Sophisticated continuous attacks are initiated to steal the most sensitive data from a company, some of which may stay in a system for a long time.
Review and analysis
All the findings from the Penetration Test are then compiled into a report with other important information. These include flaws that were exploited, the ability to access private information, technical risk briefing, advice for correction, and strategic recommendations.
Join our ISO 27001 Certification to learn more about the global standard for Cybersecurity.
What are the benefits of Penetration Testing?
ISO 27001 Penetration Testing is an integral requirement for the ISO 27001 standard. It is essential for several reasons, beyond just for the purpose of following compliance obligations. Penetration Testing may provide plenty of ISO 27001 benefits to an organisation
Vulnerability Management
Penetration Tests often occur in tandem with a vulnerability scan to make sense of Data Security. This helps an organisation emphasise the prioritised ISO 27001 Physical Security issues and coordinate its security policies better. Additionally, the data collected from the test will help an organisation deploy its security policies more efficiently, prioritise correction and install the necessary security fixes. With this information, one may effectively address the existing vulnerabilities. Morever using this knowledge efficiently closes the security gap between the organisation and the malicious attacks, giving one greater control over their security policy.
Saving money by avoiding network outage
System breaches are expensive in more ways than one, as they can cause a variety of unexpected and unwanted costs. These include correctional costs, legal costs, monetary penalties, and lost revenue from offline systems or potential customers who have decided not to indulge in business with an organisation with poor Cybersecurity controls.
Penetration Testing helps an organisation avoid these costs. By conducting a Penetration Test, Testers ask organisations essential questions about how much harm was caused, how long it will take to correct the situation and what impact the vulnerabilities will have on the business operations.
Keep out of trouble by observing regulations
Penetration Testing is one of the several methods organisations can use to maintain compliance with various regulatory ISO 27001 Requirements and frameworks. Conducting Penetration Testing on their systems can help organisations avoid paying exorbitant fines for non-compliance.
Maintain the goodwill of customers and enhance business reputation
Lastly, Penetration Testing also helps an organisation to maintain its reputation and goodwill amongst clients and customers. Protecting data and restricting the possibility of data breaches safeguard an organisation’s reputation and maintain the customer’s goodwill.
Maintaining an organisation’s reputation and goodwill helps in its growth and, in turn, fosters revenue generation. Active security policies and continual testing assure the customer that the organisation cares about the safety of its clients and stakeholders’ data. It also helps establish a culture of cyber-hygiene and accountability amongst the employees in an organisation.
Who would need to conduct Penetration Testing?
Various industries require Penetration Testing to meet compliance standards tailored to their specific needs. It'’s crucial to conduct a Penetration test before applying for a compliance audit. Manual Penetration Testing may be necessary in specific scenarios like this. Here are some industries and their relevant compliance standards that necessitate Penetration Testing:
Healthcare facilities (HIPAA):
While the Health Insurance Portability and Accountability Act (HIPAA) doesn’t explicitly mandate Penetration Testing, it’s implied by the law’s risk analysis standards. To perform a thorough risk analysis, you must assess security controls, settings, patches, and more, making Penetration Testing essential. Many healthcare institutions lack fundamental Cybersecurity measures, making compliance with HIPAA crucial. Penetration Testing provides peace of mind by helping them meet HIPAA requirements and secure their data.
Payment Processing Industry (PCI-DSS):
The Payment Card Industry Data Security Standard (PCI-DSS) was established to safeguard credit card transactions. Although PCI-DSS itself doesn’t require Penetration Testing, organisations seeking PCI-DSS compliance must undergo a PCI scan. Level 1 companies must have both an internal audit and a security scan performed by an approved vendor to apply for PCI-DSS compliance. Conducting a Penetration Test is advisable to ensure there are no security vulnerabilities before pursuing PCI-DSS compliance.
Service Organization Control 2 (SOC 2) addresses security, availability, processing integrity, confidentiality, and privacy. Virtually all service providers, especially those handling data during service delivery, need to comply with the SOC 2 standard.
Meeting SOC 2 standards requires audits, network asset monitoring, anomaly notifications, and actionable forensics. Penetration Testing is a vital component of the SOC 2 compliance framework due to its focus on identifying and mitigating vulnerabilities.
Alternatives to Penetration Testing
Penetration Testing offers significant advantages to your organisation, but it can come with substantial costs, depending on the project’s scope. Additionally, there are various testing approaches, often categorised as black-box, white-b-box, or grey-b-box testing, which relate to where the tTest originates within the network and the level of prior knowledge the tTest possesses.
There are alternative methods to assess your technical network controls, including web-based port scans, vulnerability assessments, or utilising the auditing tools integrated into your security infrastructure. By meticulously documenting and analysing the scan results and promptly taking necessary actions, you can establish a fundamental level of security.
It'’s important to recognise that while Penetration Testing is valuable for identifying and addressing security weaknesses, it is not the sole means of enhancing your security posture. Several alternatives complement Penetration testing, bolstering your overall security:
a) Vulnerability scanning: This automated process identifies known vulnerabilities in your systems and networks, spanning software, configuration, and network-related issues.
b) Attack surface analysis: This method uncovers potential attack vectors that could compromise your systems and networks. It addresses both known and unknown vulnerabilities.
c) Phishing simulations: These assessments evaluate employees'’ vulnerability to phishing attacks and provide training on recognising and avoiding such threats.
d) Security awareness Training: Educating employees on security best practices and cyber threat protection reduces the risk of human error, a common contributor to cyber attacks.
e) Red teaming: A specialised form of Penetration Testing, red teaming simulates real-world adversary attacks to evaluate the effectiveness of your security measures and pinpoint potential vulnerabilities.
Signup for our course on ISO 27001 Internal Auditor and learn how to perform internal audits and secure ISMS
How to define the scope of an ISO 27001 Penetration Test?
The scope of a Penetration Test is determined through a collaborative effort involving various stakeholders from the client’s team, such as Compliance Officers, iInternal aAuditors, and IT Personnel, as well as eExternal aAuditors. Together, they define which systems, networks, databases, or applications should undergo assessment and specify the types of security testing required.
Drawing from historical experiences, organisations preparing for an ISO 27001 Audit often consider the following components when determining the scope of their Penetration Testing:
a) The organisation'’s flagship product, which could be a Software as a Service (SaaS) platform.
b) Internet-facing server infrastructure, typically hosted in the cloud.
c) The organisation'’s internal network, comprising servers and critical infrastructure elements like Active Directory and Kubernetes clusters. .
d) Application Programming Interfaces (APIs), covering various technologies such as REST, GraphQL, and legacy web services, as well as microservices.
e) Security evaluation of mobile applications, if applicable.
f) Any administrative panels or back-office systems that support user-facing SaaS offerings.
Many organisations use a staging environment to conduct Penetration Tests. This minimises potential disruptions to their production systems. The approach is widely accepted, provided that the staging environment faithfully replicates the production setup. However, it is advisable to seek approval from the ISO 27001 Auditor before commencing the Penetration Test to ensure alignment with their requirements.
How frequently should you conduct ISO 27001 Penetration Testing?
Penetration Testing, as mentioned above, is essential for any ISO 27001-compliant IT system. Hence, testing should be done throughout the system’s lifecycle. From initial planning to execution, it should be a part of an organisation’s standard maintenance program.
Information asset management houses several technical vulnerabilities that should be subjected to continuous monitoring and improvement. This is to keep up with the rapidly evolving criminal innovation and ensure that the security policy is kept updated. The testing should occur as soon as the assets to be included in one’s risk assessment and testing agreement are identified. During the post-mortem analysis, an appropriate frequency for future re-testing should be determined.
Conclusion
Overall, having ISO 27001 Checklist compliance is very important for the modern-day organisation to safeguard its data resources. Complying one’s ISMS with the ISO 27001 Latest Version global standard in cybersecurity provides plenty of benefits to an organisation and helps it maintain a competitive edge over its industry counterparts.
However, to maintain its ISO 27001 Compliance, an organisation needs to comply with several requirements – one of them being Penetration Testing. ISO 27001 Penetration Testing is one of the most integral requirements to maintain compliance with the standard and should be fulfilled by every organisation.
Strengthen your ISO 27001 Foundation by signing up for our ISO 27001 Foundation Course!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 12th Aug 2024
Mon 9th Sep 2024
Mon 14th Oct 2024
Mon 11th Nov 2024
Mon 9th Dec 2024
Mon 27th Jan 2025
Mon 24th Feb 2025
Mon 24th Mar 2025
Tue 22nd Apr 2025
Tue 27th May 2025
Mon 23rd Jun 2025
Mon 28th Jul 2025
Mon 25th Aug 2025
Mon 22nd Sep 2025
Mon 27th Oct 2025
Mon 24th Nov 2025
Mon 15th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


