We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Data is extremely integral to the optimal functioning of a modern organisation. Organisations use data to their advantage to help maximise revenue generated as well as increase efficiency, and hence, the adequate protection of data is a priority for businesses.
To safeguard their data better, organisations seek compliance with globally recognised information security standards – the most popular of which is the ISO 27001 standard. However, gaining compliance with ISO 27001 is complicated – which is where our ISO 27001 Checklist comes in to make it simpler. The ISO 27001 checklist assists firms in preparing for a screening in order to obtain certification in accordance with the worldwide standard for ISMS.
Cyber incidents are the leading risk to organisations across the world, as per the Statista amongst risk management experts. Therefore, in order to curb the threat that cyber attacks pose to your organisation’s valuable data resources, implementing a security standard such as ISO 27001 is of paramount importance. But, before implementing it, it’s important understand the requirements. This blog will provide you with an ISO 27001 Checklist consisting of steps you will need to follow to gain ISO 27001 Certification.
Table of Contents
1) ISO 27001 Checklist
2) A step-by-step guide to ISO 27001 implementation
3) Tips to achieve ISO 27001 compliance
4) Conclusion
ISO 27001 Checklist
To be compliant with ISO 27001, organisations must adhere to a Checklist that outlines the necessary steps to be taken to improve their Information Security Management Sytems (ISMS). Given below is the complete ISO 27001 Checklist that you can follow to ensure high-quality Information Systems:
Develop an implementation team and plan
1) Establish roles and responsibilities for team members
Understand ISO 27001 requirements
1) Review each clause of ISO 27001
2) Review Annex A of ISO 27001
Find your security baseline
1) Understand the current state of security in your organization by questioning the security protocols in existence.
Define the ISMS scope
1) Determine your ISMS scope in terms of your organization’s business functions, information processing systems, and information processing environments.
2) Determine which aspects of your business are in and out of scope.
3) Inform stakeholders of your ISMS scope.
4) Conduct a risk assessment.
5) Complete your Statement of Applicability (SoA).
Create and Implement an ISMS plan
1) Create a plan document that clearly defines the responsibilities and authority structures within your ISMS.
2) Document procedures and processes for handling various security incidents, including:
a) Managing access control
b) Confidentiality
c) Integrity
d) Availability of information assets
e) Incident response
Train employees on policies and procedures
1) Train all team members on new ISMS policies and procedures
2) Train relevant team members on your incident response plans
3) Establish disciplinary or sanctions policies or processes for team members found out of compliance with mandatory infosec requirements
Conduct an Internal Audit
1) Secure a non-biased individual or group to examine your ISMS
2) The internal auditor will:
a) Review all documentation
b) Review your ISMS
c) Conduct penetration testing
d) Collect evidence on what is and isn’t working
3) The auditor will produce an internal audit report that details corrective actions and recommendations, limitations, and other observations
4) After you receive the report, work with your ISO 27001 team to address listed non-conformities
Find an accredited Auditor to lead the ISO 27001 Certification Audit
1) Find an accredited Auditor to conduct your ISO 27001 Certification Audit
2) Undergo a Stage 1 Audit
3) Obtain and address feedback from the Stage 1 Audit
4) Undergo a Stage 2 Audit
5) Address specific non-conformities identified by your Auditor
6) Receive ISO 27001 Certification
Cryptographic controls
1) Use encryption and cryptographic techniques to protect sensitive information during storage, transmission, and processing, as appropriate.
Want to elevate your Cybersecurity prowess to new heights? Register for our ISO 27001 Lead Auditor Course now!
A Step-by-step guide to ISO 27001 implementation
Implementing an ISMS that is compliant with ISO 27001 Checklist can be challenging; however, the process is certainly worth the benefit. Let's explore the step-by-step guide to help an organisation gain insights into ISO 27001 implementation:
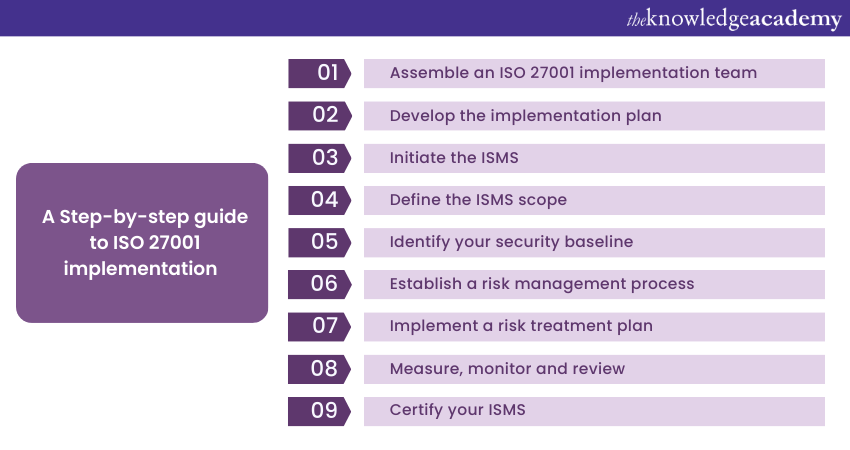
Assemble an ISO 27001 implementation team
In the procedure to gain ISO 27001 Certification, your first task is to assemble a dedicated team to oversee the ISO 27001 implementation process. The team of your selection will determine the following:
a) Scope of the ISO 27001 implementation process
b) Develop information management practices and policies
c) Gain buy-in from the stakeholders
d) Work directly with the Auditor
Next, you will need to appoint a project leader to oversee and monitor the implementation of the ISMS.
The size of your organisation and the amount of data you handle will determine whether one person can lead the project or if a larger team is needed. Your project leader should have a well-rounded knowledge of information security controls as well as the authority to lead a team. Once the team is assembled along with their project leader, a project mandate should be created. The mandate is essentially a set of answers to the following questions:
1) What are we hoping to achieve?
2) How long will our task take to achieve?
3) How much money will it cost?
4) Does the project have management support?
Develop the implementation plan
For the next step of the ISO 27001 implementation process, you will need to start planning for the implementation process itself. The implementation team that you have chosen will use the abovementioned project mandate to develop a more detailed structure of their information security objectives, plan, and risks register. This includes setting out high-level policies for the ISMS that establishes:
1) Roles and responsibilities
2) Rules for its continuous improvement
3) How to raise awareness of the project through both internal and external communication
Want to elevate your Cybersecurity prowess to new heights? Register for our ISO 27001 Lead Auditor Course now!
Initiate the ISMS
Now that you have your implementation plan is in place, it is time to determine which continual improvement methodology to use. ISO 27001 does not specify a particular methodology but recommends a “process approach” - which is essentially a Plan-Do-Check-Act strategy.
You can make use of any model, provided that the ISO 27001 Requirements and processes are clearly defined, correctly implemented, and regularly reviewed and improved. You also need to create an ISMS policy, which does not need to be detailed – it simply needs to outline what your implementation team aims to achieve and how they plan on doing it. Once your team is done with creating an ISMS policy, it should be approved by higher-level management.
At this point of the ISO 27001 implementation process, you can start developing the remaining parts of your document structure. It is recommended to use a four-tier strategy for this, as discussed as follows:
a) Policies should be at the top of the document, which defining the organisation’s position on certain specific issues such as acceptable use and password management.
b) Procedures that enact the policies’ requirements.
c) Well-defined work instructions that describe how the employees of the organisation should meet those policies.
d) Records that track and monitor the procedures and work instructions.
Define the ISMS scope
The next phase of ISO 27001 implementation involves understanding the framework of the ISMS that is mentioned in Clauses 4 and 5 of the ISO 27001 Standard. You need to define the ISMS scope.
In this way, you will be able recognise everything relevant to ISMS and its scale. That is why it is so important to define the ISMS scope because the ISMS can meet all your organisation particular needs only this way.
Determining the ISMS scope includes identifying places which contain data, either they are physical or digital, e.g. storage systems or removable devices. Precisely identifying your ISMS scope before implementing ISO 27001 is an important step.
The process must be undertaken with utmost care. If your ISMS scope is tiny, then a part of information can be missed out and you eventually put your organization security into risk. In comparison, if your ISMS extent is too wide the ISMS will get too complicated to handle.
Identify your security baseline
For the next step in the ISO 27001 implementation process, you will have to identify your security baseline. An organisation’s security baseline can be defined as the minimum level of activity that is required to conduct business in a secure manner. You can identify your organisation’s security baseline with the help of the information that you have gathered as part of your ISO 27001 risk assessment. Doing this will help you identify your organisation’s most significant security vulnerabilities and the corresponding security control measures to help mitigate the risk (as outlined in Annex A of the ISO 27001 standard).
Unlock the secrets of secure data fortification - Join our ISO 27001 Foundation course and safeguard your digital kingdom today!
Establish a risk management process
In the next phase of the ISO 27001 implementation process you are expected to implement a Risk Management process for your organisation. Risk Management is the core of an ISMS because a great deal of your Security System entirely depends on the hazards that you have perceived and prioritised. Also, for a company that wants to achieve the ISO 27001 Certification, Risk Management is a fundamental process.
The framework enables the organisations to define their own Risk Management tools. The traditional way to do so is by homing in on risks attached to certain assets or risks known to be associated with specific scenarios. Whether you opt for one of the five steps or all of them, your choices will need to be guided by risk assessment methods. The five steps in this process are:
1) Establishing a risk assessment framework
2) Identifying risks
3) Analysing risks
4) Evaluating risks
5) Selecting risk management options
You will then need to establish your risk acceptance criteria, i.e., the damage that the potential threats will cause and the likelihood of their occurrence. Project Managers often tend to quantify risks by scoring them on a risk matrix; the higher the score for a risk, the bigger the potential threat it poses. You will then have to select a threshold for the point at which risk must be addressed. There are a total of four approaches you can take, listed as follows:
1) Tolerate the risk
2) Treat the risk by applying security controls
3) Terminate the risk by completely avoiding it
4) Transfer the risk with an insurance policy, or with the help of an agreement with other parties
Finally, ISO 27001 requires organisations to complete a mandatory Statement of Applicability (SoA) documenting the ISO 27001 controls, such as the following:
a) Information security policies
b) Organisation structure
c) Human resources
d) Asset management
e) Access control
f) Cryptography
g) Physical security
h) Operations
i) Communications
j) System development
k) Supplier relationships
l) Incident management
m) Continuity
n) Compliance
It primarily contains the controls you have selected or omitted for your organisation – as well as a justification for your choices.
Implement a risk treatment plan
For instance, the risk treatment plan is the component which you will have to implement after the ISO 27001 implementation process. Defining implementation of the risk treatment plan further is the process of developing the security controls that can ensure confidentiality, integrity, and availability of your information resources.
This will be followed by developing procedures for identifying, evaluating and reviewing ISMS competencies that the organisation needs to attain its objectives. Firstly, for achieving this goal you will have to go through the needs analysis and give your targeted level of knowledge.
Measure, monitor, and review
After your implemented treatment plan is in place, you will probably have to go back to see whether the ISMS is still effective or not. It is recommended to carry out ISMS reviews at least annually as this will help you to keep a close eye on the risks that are developing.
In the approval phase, you must reveal your criteria that is based on the objectives in the project's mandate.
A quantitative approach involves assigning a number to whatever that you generalize. This is beneficial in case you are involving matters that are financial related such as time and cost. The other effective approaches to identify criteria are qualitative analysis, which weighs the measurements through judgment. Qualitative analysis can be used when your assessment is basically within the range of categories, ‘high’,’medium’,’low’ and you should also do internal audits to your ISMS on a regular basis.
An ISO 27001 Audit, despite it having no fixed way in performing the process, can take various periods of time to complete. This makes it possible to avert huge levels of loss in productivity and makes sure that the manpower of your team is not dissipated over various tasks.
Nonetheless, your main goal should be finishing the process as soon as possible because then you will have to get the results and then assess them to align your audit plan for the next year beforehand. You are going to use the results of your internal audit as the raw material for the management review which is the final stage in the stage of continual improvement.
Certify your ISMS
After the ISMS is established, you can decide to go for an ISO 27001 certification, a stage that will take the auditors. The first thing the audit decides is whether the organization’s ISMS has been developed as per the ISO 27001 specs. If auditor is happy, they would conduct a thorough investigation.
Before certification, you should be certain about your capabilities because the procedure is long (and you will be charged irrespective of whether you pass or fail immediately). The other thing to remember before you try you get certified is that you should pick the right certification body to certify you.
There are several certification bodies you can choose from, but you should always verify that the certifying agency is accredited by a national certification body, which must be a member of the International Accreditation Body (IAF) in your case.
With this, the review is in line with ISO 27001 as it does not offer accreditation to companies that have not implemented a compliance framework compliant with ISO 27001. The cost of the certification audit is usually the main concern as people decide what body to go for; but you shouldn’t make your decision only on the cost – you should go for a reviewer who has experience with your industry. An ISMS is always being designed for a specific firm and it is your auditor who must know particularly the requirements of your organisation.

Tips to achieve ISO 27001 compliance
Organisations can acquire their ISO 27001 compliance mark by following these tips:
Creation of a solid policy
The organisation must promptly address all the non-conformities that are recognised by the Auditor. Having a comprehensive policy that covers all the aspects of IT security, is a fundamental component of the ISO 27001 implementation. It helps the organisation in protecting confidential information, other valuable assets and instituting efficient security controls.
Ensure compliance of third-party suppliers with ISO 27001
Organisations must not overlook the compliance by their partner companies and third-party suppliers. They must ensure that they comply with the standard thoroughly if they are sincere about their ISO 27001 accreditation.
They should maintain transparency about their requirements so that the parties involved can collaborate and work efficiently. The inclusion of contractual obligations helps ensure that all parties are comfortable complying with the standard. The obligation includes that the suppliers comply with the regular audit sessions of their ISMS.
Improve the ISMS continually
After an organisation has been rewarded the ISO 27001 compliance mark, their journey does not end there, rather it is just the beginning of a continual process. Additionally, a commitment to the improvement of the ISMS through regular audit sessions and policy updates helps the organisation ensure their consistency in maintaining effectiveness behind protecting their Information Security.
Moreover, this process obligates the organisation to assess, test, review and measure the performance quality of their ISMS. The review sessions also establish the ground rule that the company cannot duplicate any work in the ISMS for convenient proof of improvement taking place.
Conclusion
In conclusion, gaining ISO 27001 Certification is a complicated and time-consuming process. However, if done right, gaining compliance to the global information security standard ensures that your organisation’s data resources are properly protected. To comply with the standard, make sure to follow all the steps listed in the ISO 27001 Checklist. Hope this blog provided you with all the information you needed to know to protect your data better and more effectively!
Boost your organisation's cybersecurity with your choice from our list of extensive our ISO 27001 Certification - sign up now!
Frequently Asked Questions

ISO 27001 covers 14 domains: Information Security Policies, Organization of Information Security, Human Resource Security, Asset Management, Access Control, Cryptography, Physical and Environmental Security, Operations Security, Communications Security, System Acquisition, Development, and Maintenance, Supplier Relationships, Incident Management, Continuity Management, and Compliance.

ISO 27001 requires establishing, implementing, maintaining, and improving an Information Security Management System (ISMS). It involves defining scope, conducting risk assessments, implementing controls, establishing policies, conducting audits, and ensuring compliance with legal and regulatory requirements.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various ISO 27001 Training, including ISO 27001 Foundation Course, ISO 27001 Lead Auditor Course and ISO 27001 Internal Auditor Course. These courses cater to different skill levels, providing comprehensive insights into ISO 27005 Risk Assessment Process: A Quick Guide.
Our ISO & Compliance Blogs covers a range of topics offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27002 Foundation Training
ISO 27002 Foundation Training
Mon 13th May 2024
Mon 2nd Sep 2024
Mon 2nd Dec 2024







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


