We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

In today’s world, everything is driven by the latest technological trends. A wave of digital transformation has made digitally available information paramount for everyone. Hence theft of information has become a real threat these days. Every organisation is exposed to security threats, and while some technologies can help combat attacks – organisations must ensure their business processes mitigate these risks.
In order to do that, companies adopt Information Security Management Services (ISMS) frameworks that operate on standards such as ISO 27001 and SOC 2. While both frameworks are similar, there is a difference between ISO 27001 and SOC 2.
According to Statista, a total 21% of a 2017 survey were aware of ISO 27001, while 57% of large global firms also knew about the standard. On the other hand, SOC 2 is used by several organisations in the United States of America and Canada. Due to their prevalence in the cybersecurity domain right now, many organisations often inquire about the differences between the two. While many organisations pose the question of which standard will suit them better, we have all you need to know about your potential choice. This blog will elucidate on the difference between ISO 27001 and SOC 2, as well as a few of their commonalities.
Table of Contents
1) What are ISO 27001 and SOC 2?
2) What is the difference between ISO 27001 and SOC 2?
a) Scope
b) Market Applicability
c) Certification vs Attestation
d) Certification/Attestation Process
e) External Deliverables
f) Project Timeline
3) Do ISO 27001 and SOC 2 have anything in common?
4) ISO 27001 vs SOC 2: Which one is right for you?
5) How to become ISO 27001 compliant?
6) How to become SOC 2 compliant?
7) Conclusion
What are ISO 27001 and SOC2?
ISO 27001, also known as ISO/IEC 27001, is a set of standards for an ISMS. These standards or requirements represent the most suitable practices for Information Security Management in an organisation. ISO 27001 Latest Version provides security across several assets such as financial information, employee data, intellectual property, and third-party data. ISO 27001 emphasises ensuring three aspects of Data Security, namely – availability, confidentiality, and integrity. The framework was formulated jointly by the International Electrotechnical Commission and the International Organization for Standardization (ISO).
On the other hand, Service Organisation Control 2 or SOC 2 enlists Organisational Controls for five main service principles established by the American Institute of Certified Public Accountants (AICPA). These principles include security, availability, processing integrity, confidentiality, and privacy of customer data. Collectively, these Organisational Controls provide a framework for the protection of data. Organisations implement SOC 2 to assess their security and identify avenues of Cybersecurity improvement according to the practices suggested by the SOC 2 report.
There are two main types of SOC 2 compliance, namely Type 1 and Type 2. While Type 1 verifies an organisation’s use of compliant systems and processes at a point in time, Type 2 attests compliance over a period. A Type 1 report encompasses all the security controls used by an organisation and attests to their proper designing and enforcement. On the other hand, a Type 2 report includes everything a Type 1 report consists of, along with verification that the said controls are effective in operation.
Secure your future in Cybersecurity with our ISO 27001 Foundation Training – your gateway to mastering Information Security Management Systems!
What is the difference between ISO 27001 and SOC 2?
This section of the blog will explore the differences between ISO 27001 and SOC 2 based on several parameters
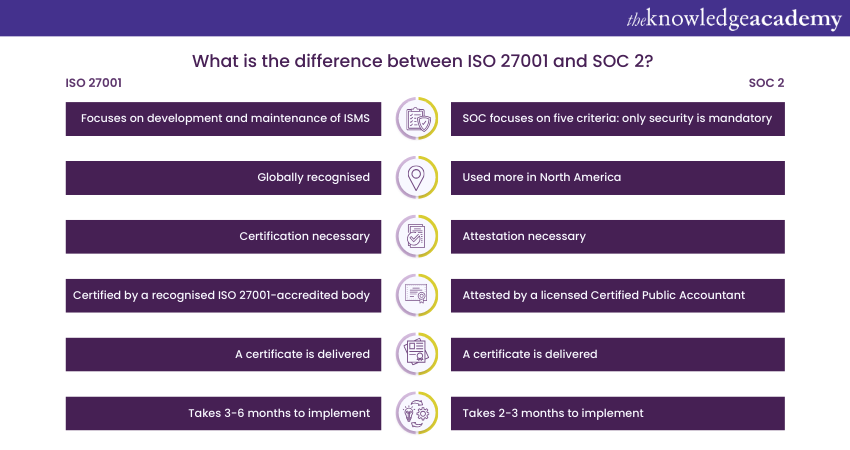
Scope
The key difference between ISO 27001 and SOC 2 lies in the scope of the two frameworks. Both ISO 27001 and SOC 2 host security control procedures that encompass processes, policies, and technologies to protect sensitive data and information. While studies states that the two frameworks share 96% of the same security protocols, the difference lies in the approaches implemented. ISO 27001 Framework emphasises the development and maintenance of what is known as an Information Security Management System (ISMS). An ISMS offers an organisation a structured approach to managing its Information Security. To comply with organisational standards, you must conduct a Risk Assessment along with identifying and implementing security controls – and review their effectiveness regularly.
In contrast, SOC 2 is a lot more flexible. SOC 2 consists of five trust services criteria: security, availability, processing integrity, confidentiality, and privacy. Of the five criteria, only security is mandatory. Organisations have the option to implement internal controls related to other principles.
Market applicability
It should be noted that the market applicability should also drive your decision to choose between ISO 27001 or SOC 2. While both frameworks have global recognition, SOC 2 is more associated with North America. However, ISO 27001 is a global standard and is more prevalent if you are outside North America.
Certification vs attestation
One of the most important differences between the standards is that SOC reports are not generally considered to be certifications. As SOC examination services take place under the AICPA attestation standards, they are considered to be attestation reports. While certifications are granted by a recognised body, attestation reports provide an opinion by an independent Auditor about the control environment of an organisation. In the case of SOC 2, the attestation focuses on the internal controls at an organisation to meet criteria such as security, availability, processing integrity, confidentiality, and/or privacy. On the other hand, in the case of ISO 27001, an organisation receives certification if the conformity of the organisation ISMS is up to the ISO 27001 global standard.
Certification/attestation process
One must complete an external audit to achieve certification/attestation in either framework. However, the difference in the process lies in who conducts the inspection. For ISO 27001, an accredited certification body must attest to it. On the other hand, for SOC 2 attestation, it can only be performed by a licensed Certified Public Accountant (CPA).
External deliverables
Another important difference between the two standards is the type and content of the external deliverables for each engagement. In the case of SOC 2, the final external deliverable is an attestation report that consists of an opinion letter from the service organisation audit, an assertion letter from the service organisation’s management, and a system description with emphasis on the five key components of the organisation’s system under review. The description will contain an extensive narrative on the five key components, namely – infrastructure, software, people, procedures, and data. Other than that, the report will also contain organisational-level procedures and the applicable trust services criteria, related control, and the test results from the Auditor's test.
On the other hand, the external deliverable for ISO 27001 is a certificate. The certificate is a one or two-page document that contains relevant information pertaining to the engagement. The certificate contains information such as the certified organisation’s ISMS scope, in-scope locations, standard certified against, date issued, and date of expiration. A report is also issued after the end of every stage (stage 1, stage 2, surveillance audits, recertification reviews). However, these reports are for general internal use and are not intended to be a deliverable like in the case of SOC 2 reports.
Project timeline
Once the external audit is completed, both ISO 27001 and SOC 2 Certifications need to be obtained. The certification process is similar for ISO 27001 and SOC 2, consisting of three stages that must be completed. The first stage of the process requires a gap analysis to identify areas of improvement and for the organisation to define its ISO 27001 Physical Security objectives. The second stage requires the organisation to identify appropriate security controls based on its needs and take steps to implement them. This step also involves documentation of practices and establishment of a method to review and improve processes. The final step is an internal audit, which aims to identify and fix any mistakes.
Once all three stages are completed, an organisation can arrange for an ISO 27001 Audit or SOC 2 audit by contacting a certification body. While the certification process is the same for both frameworks, the difference lies in the time taken to implement the framework. The implementation time is usually determined by the amount of work needed to meet the standards. SOC 2 takes about two to three months to implement, while ISO 27001 takes three to six months. Another notable distinction between the two lies in the fact that SOC 2 places emphasis on the implementation of security controls for safeguarding customer data, whereas ISO 27001 mandates the establishment of an operational Information Security Management System (ISMS) along with the implementation of specific ISO 27001 controls.
Do ISO 27001 and SOC 2 have anything in common?
Despite plenty of differences between the two, ISO 27001 and SOC 2 also have several similarities. Both ISO 27001 and SOC 2 are important for organisations willing to evaluate and improve their Data Security in accordance with industry standards. Both involve important aspects of Information Security, such as confidentiality, availability, and integrity. In fact, both frameworks can also work in tandem. ISO 27001 and SOC 2 overlap in more ways than one and hence can be implemented together. While ISO 27001 can help organisations build ISMS, SOC 2 can ensure improvement and assessment of Data Security.
Both certifications/attestations need an independent assessor to verify the controls and check whether they meet the Trust Service Principle (TSP) criteria (SOC 2) and standard requirements (ISO). In addition, both standards are globally applicable and benefit organisations with an international presence. Both ISO 27001 Compliance efforts emphasise the organisation’s approach to mitigating Information Security risk and making sure that there are proper controls to maintain Information Security risk. Both compliance standards are valuable in an organisation’s attempt to generate customer trust and overall market trust as well. Certification in either standard displays the organisation’s commitment to ensuring Information Security and that it has been attested by a certified, competent third-party assessor.
Completing certification in either of the two or both assures customers and investors about the level of security that your organisation has. And owing to the significant overlap between the two frameworks, being certified in one is a step towards meeting standards for the other. While neither of the framework is mandatory, getting certified in SOC 2 helps organisation achieve several benefits of ISO 27001. Certification in either or both frameworks helps an organisation build trust with vendors, comply with regulatory standards, as well as evaluate and improve Data Security practices.
Become an ISO 27001 Lead Auditor with our comprehensive ISO 27001 Lead Auditor Training – enhance your organisation's Information Security and achieve audit excellence!
ISO 27001 vs SOC 2: Which one is right for you?
This section of the blog will describe the different scenarios and needs for which you should choose either ISO 27001 or SOC 2, or a combination of both.
When to choose ISO 27001?
You will be better suited to opt for ISO 27001 if you are looking to fulfil the following needs:
a) Global compliance needs: ISO 27001 is an international standard, suitable for organisations with a global presence. If your business operates across multiple countries and you need a universally accepted framework, ISO 27001 is the way to go.
b) Comprehensive Information Security Management: ISO 27001 key features provides a holistic approach to Information Security, covering people, processes, and technology. Choose this standard if you want a comprehensive management system that encompasses Risk Management, legal compliance, and continuous improvement.
c) Third-party assurance: ISO 27001 Certification demonstrates your commitment to Information Security to clients, partners, and regulators. If your stakeholders require tangible evidence of your security measures, ISO 27001 Certification can provide the assurance they need.
When to choose SOC 2?
You will be better suited to opt for SOC 2 if you are looking to fulfil the following needs:
a) Industry-specific requirements: SOC 2 is particularly relevant for technology and cloud computing organisations. If your business involves handling sensitive customer information, like in Software as a Service (SaaS) or data hosting, SOC 2 compliance ensures you meet industry-specific requirements.
b) Trust and transparency: SOC 2 focuses on controls that are relevant to the security, availability, processing integrity, confidentiality, and privacy of customer data. Choose SOC 2 if your clients need assurance about the safety of their data, enhancing trust and transparency between you and your customers.
c) US market focus: While SOC 2 is recognised globally, it is often a preferred choice for companies operating primarily in the United States. If your target market is the US and your clients demand stringent Data Security standards, SOC 2 compliance aligns with their expectations.
When to choose both?
You will be better suited to opt for a combination of ISO 27001 and SOC 2 if you are looking to fulfil the following needs:
a) Diverse client base: If your business serves a diverse client base with varying compliance requirements, pursuing both ISO 27001 and SOC 2 Certifications might be necessary. This dual certification approach demonstrates your commitment to international and industry-specific standards, accommodating the needs of different clients.
b) Enhanced security posture: Combining ISO 27001's comprehensive approach with SOC 2's specific focus on customer data results in a robust security posture. This dual approach not only meets general security standards but also addresses the unique demands of your industry, offering a higher level of protection against potential threats.
Unlock the expertise to ensure robust Information Security – join our ISO 27001 Internal Auditor Training and safeguard your organisation with confidence!
How to become ISO 27001 compliant?
Becoming ISO 27001 compliant requires a systematic approach and dedication to robust Information Security practices. Firstly, establish a clear framework outlining your security objectives, policies, and procedures. Conduct a thorough ISO 27001 risk assessment to detect potential vulnerabilities and assess their impact. Create and implement a comprehensive set of security controls and measures to mitigate these risks effectively.
Engage employees at all levels, ensuring they are aware of their roles and responsibilities concerning Information Security. Regular training and awareness programmes are crucial. Establish a method for monitoring, measurement, analysis, and evaluation of your security processes.
Additionally, conduct internal audits to identify areas of improvement and compliance gaps. Seek certification from an accredited certification body, which involves a final assessment of your compliance with the ISO 27001 Standard. Continuous improvement is key; regularly review your security measures and adapt them to emerging threats and changing business needs, ensuring a persistent and evolving commitment to Information Security.
How to become SOC 2 compliant?
Achieving SOC 2 compliance is a meticulous process that demands careful planning and rigorous implementation of security measures. To become SOC 2 compliant, organisations must follow a structured approach. Firstly, conduct a thorough internal assessment to identify potential vulnerabilities and areas for improvement. Next, develop and implement robust security policies and procedures that align with SOC 2 requirements, focusing on areas such as Data Security, access controls, and incident response.
It's crucial to create a documented system for tracking and managing security incidents. Employee training and awareness programmes are vital to make sure everyone knows their role in maintaining security standards. Engaging with a qualified Auditor experienced in SOC 2 assessments is essential. They will perform an independent evaluation, testing your security controls and processes.
Make sure to address any identified weaknesses and refine your security practices accordingly. Regular monitoring and continuous improvement are key; staying SOC 2 compliant is an ongoing commitment to maintaining a high level of Data Security and trust with your clients.
Conclusion
All in all, both standards are efficient compliance efforts for organisations to undertake. Both ISO 27001 and SOC 2 can be used to gain a competitive edge over industry counterparts.
While SOC 2 is easier to implement and less expensive to maintain, it is also less rigorous. On the other hand, ISO 27001 is more rigorous and requires more work to be done, but it is more efficient in terms of protecting organisations from information security threats. While ISO 27001 and SOC 2 both have their differences, they also have their similarities, which enables them to work in tandem.
Become an expert in ISO 27001 by signing up for our ISO 27001 Certification course!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 12th Aug 2024
Mon 9th Sep 2024
Mon 14th Oct 2024
Mon 11th Nov 2024
Mon 9th Dec 2024
Mon 27th Jan 2025
Mon 24th Feb 2025
Mon 24th Mar 2025
Tue 22nd Apr 2025
Tue 27th May 2025
Mon 23rd Jun 2025
Mon 28th Jul 2025
Mon 25th Aug 2025
Mon 22nd Sep 2025
Mon 27th Oct 2025
Mon 24th Nov 2025
Mon 15th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


