We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Do you want to know How to Become CISM Certified? If yes, then you’re at the right place. The Chief Information Security Manager or CISM Certification is a globally recognised credential for professionals in the field of Information Security Management. According to the facts presented on Information Systems Audit and Control Association’s (ISACA) website, CISM certificate holders receive 42% higher pay after acquiring the certification. Read How to Become CISM Certified with our comprehensive blog and explore essential steps and expert tips for a successful journey towards becoming a CISM.
As you know, CISM Certification is a valuable credential that enhances professional credibility and opens doors to career advancement. Additionally, it equips individuals with comprehensive knowledge of Information Security Management and provides access to a supportive professional network. It is a significant milestone for individuals looking to excel in the field of Information Security Management. In this blog, we will provide a step-by-step guide on How to Become CISM Certified. In addition, we will discuss the CISM requirements for Certification and its benefits. Read to learn more!
Table of Contents
1) What is CISM
2) What are the steps to Become CISM Certified?
a) Pass the exam
b) Involve in the CPE program
c) Reinforcement of ethical conduct
d) Work experience
e) Submit CISM application to ISACA
3) Conclusion
What is CISM?
The CISM Certification, offered by ISACA, stands as a globally acknowledged credential for Information Security Managers. It affirms an individual's proficiency in crafting, executing, and managing Information Security initiatives. Esteemed worldwide, CISM holds considerable prestige within Information Security Management, making it a coveted qualification.
Possessing the CISM Certification is a marker of expertise, placing professionals in high demand. This recognition not only opens avenues for career advancement but also increases earning potential significantly. As businesses increasingly prioritise robust Cybersecurity measures, the demand for CISM Certified professionals continues to grow.
What are the steps to Become CISM Certified?
Becoming CISM Certified involves several steps. By following these steps, you can demonstrate your expertise in Information Security Management and become CISM Certified:
Pass the exam
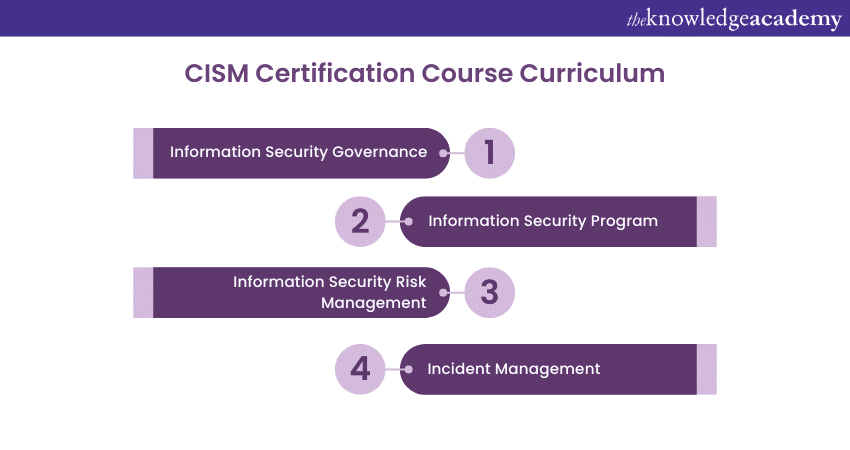
Passing the exam is one of the basic requirements for acquiring the CISM Certification. The CISM exam includes four key domains which include:
a) Information Security Governance
b) Information Risk Management
c) Information Security Program
d) Incident Management
Involve in the CPE program
Continuing Professional Education (CPE) refers to continuous professional development that must be ensured to maintain the certification. It is a process which promotes ongoing professional growth and development among CISM-Certified professionals. It helps in expanding the skillset of CISM holders. CPE aligns with the CISM job practice domains, increasing a professional’s relevance in the field of Information Security Management. The benefits of CPE include:
a) Enhances competence of CISM Certified individuals
b) Provides opportunities for networking and collaboration
c) Ensures the validity of the certification
d) Reinforcement of ethical conduct
e) Professional growth and development
f) Improves relevance in the industry
Additionally, annual maintenance costs and a minimum of 120 CPE hours attained in the last three years are required. You're required to have completed a minimum of 20 hours each meeting ISACA requirements.
Reinforcement of ethical conduct
To get a CISM Certification, it is essential to comply with the code of professional ethics, which will help in shaping your personal and professional conduct. These include:
a) Encourage and facilitate the adoption of suitable standards and procedures for effective governance and management of enterprise information systems and technologies. This includes promoting compliance with audit, control, security, and risk management practices.
b) Execute their responsibilities with impartiality, thoroughness, and professionalism, adhering to established professional standards.
c) Act in the best interest of stakeholders, upholding the law and maintaining exemplary conduct and character that reflects positively on their profession and the association.
d) Safeguard the privacy and confidentiality of information acquired during their work unless legal authorities mandate disclosure. They must refrain from exploiting such information for personal gain or sharing it with other unauthorised parties.
e) Sustain and enhance their competence in their respective fields, engaging only in activities for which they possess the necessary skills, knowledge, and proficiency.
f) Communicate the outcomes of their work to relevant parties, ensuring full disclosure of all significant facts that may impact the accuracy of the reported results.
g) Support the ongoing professional education of stakeholders, empowering them to comprehend the governance and management of enterprise information systems and technologies. This encompasses fostering an understanding of audit, control, security, and risk management aspects.
Gain an in-depth understanding of Information Security Governance with our comprehensive CISM Certified Information Security Manager Training today!
Work experience
To become CISM Certified you must have at least five years of work experience in Information Security Management. This must include at least three years of experience in each of the three CISM domains to become Certified as a CISM Certified professional. Some domains are information Security Management, Governance, Risk Management, Programme Development and Management, and Information Security Incident Management.
It is possible to replace some qualifications, such as up to two years of experience with certain professional certificates or up to one year of experience with pertinent educational credentials. CISM Certification requires more than just having the necessary job experience. To keep your Certification, you must also pass the CISM exam, abide by the Code of Professional Ethics, and complete the CPE requirements.
Submit CISM application to ISACA
The conclusive phase involves the submission of a Certified Information Security Manager (CISM) Certification application. This step becomes viable only upon successfully clearing the CISM examination and obtaining the requisite professional work experience.
Benefits of CISM Certification
As you have understood How to Become CISM Certified, it is time we get to know its benefits. When contemplating your choices, it is beneficial to focus on the future and consider the advantages of acquiring a CISM Certification. The following are some benefits associated with attaining a CISM Certification:
1) Integration into an exclusive community: A CISM Certification places you within an esteemed community of top-tier Information Security professionals. This affiliation acknowledges your expertise and provides valuable networking opportunities within this elite circle.
2) Demonstration of commitment: This certification is no mean feat, signifying your unwavering dedication to a career in Information Security. The challenges posed by the certification process underscore your commitment to continuous professional development and mastery in the field.
3) Expanded career prospects: A CISM Certification significantly broadens your horizons in terms of job opportunities. Employers, recognising the value of this certification, often seek certified professionals to fortify their information security teams, offering you a more comprehensive array of potential career paths.
4) Enhanced earning potential: With a CISM Certification, you can access more job opportunities and elevate your potential earning power. Employers are willing to remunerate certified professionals at a higher level, acknowledging the expertise and value they bring to the organisation.
5) Global recognition: The CISM Certification is internationally recognised, providing a respected and valued credential across borders. This global recognition enhances your marketability and allows for greater mobility in the ever-expanding field of information security.
Job potential
A Certified Information Security Manager (CISM) Certification significantly enhances job potential and opens a wide range of opportunities in the field of information security. The following are several avenues where CISM Certified professionals can excel:
1) Information security manager: CISM Certification is directly aligned with roles such as Information Security Manager, where professionals oversee and implement security policies and practices within an organisation. They play a pivotal role in protecting sensitive information and ensuring compliance with regulatory standards.
2) Chief Information Security Officer (CISO): CISM is often sought after for executive-level positions like CISO. In this capacity, professionals are responsible for the organisation's overall information security strategy, ensuring that it aligns with business goals and effectively mitigates risks.
3) Security consultant: CISM Certified individuals are well-equipped to work as security consultants, advising organisations on developing and implementing robust information security programs. They may provide insights into risk management, governance, and compliance, helping clients enhance their security posture.
4) Risk manager: The risk management focus of CISM makes certified professionals well-suited for roles as Risk Managers. They assess and manage risks associated with information security, develop strategies to mitigate potential threats and ensure that security measures align with organisational objectives.
Salary outlook
Certified Information Security Manager (CISM) professionals can anticipate a salary range influenced by experience, industry, location, and organisational size. Typically, entry-level CISM Certified individuals may earn between £40,000 and £60,000 annually, while mid-level professionals could command salaries in the range of £60,000 to £80,000 per year.
Those with extensive experience, particularly in leadership roles, may see earnings surpassing £80,000 annually. Industry sectors such as finance, healthcare, and technology often offer higher compensation due to the critical nature of their information assets. Additional certifications or specialised skills can also contribute to an individual's earning potential.
Conclusion
We hope this blog gives you a detailed understanding of How to Become CISM Certified or how to acquire CISM Certification. Earning the CISM or CRISC Certification can be a game-changer for your career, and it opens doors to exciting IT Management roles that companies value highly. This achievement boosts your professional reputation and paves the way for better pay, bonus, and benefits. It also deepens your understanding of Security Systems Management, giving you a competitive edge in the field.
Master Information Security Management with our expert-led CISM Training to learn more!
Frequently Asked Questions

Professionals gain significant competitive advantages with CISM Certification. It positions them as elite information security experts, fostering trust among employers and clients. The certification validates expertise in risk management, governance, and strategic alignment of security with business objectives. CISM holders often secure leadership roles, enhance job prospects, and command higher salaries due to their comprehensive skill set. Additionally, global recognition and adherence to ethical standards make CISM a powerful asset in the dynamic field of information security.

Aspiring individuals should prioritise structured study plans to enhance the path towards CISM Certification, leveraging reputable resources. Consistent practice with sample exams is vital, reinforcing conceptual understanding. Seeking mentorship or joining study groups fosters collaboration and insights. Gaining practical experience in information security roles is invaluable. Staying abreast of industry trends and updates is crucial, ensuring alignment with CISM domains. Lastly, perseverance and a growth mindset contribute to success in this rigorous certification journey.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various CISA Training, including CISA Certified Information Systems Auditor. These courses cater to different skill levels, providing comprehensive insights into CISM Certifications.
Our IT Security & Data Protection blogs covers a range of topics related to CISA Training, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Data Protection skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 CISM Certified Information Security Manager
CISM Certified Information Security Manager
Mon 20th May 2024
Sat 8th Jun 2024, Sun 9th Jun 2024
Mon 10th Jun 2024
Mon 15th Jul 2024
Sat 3rd Aug 2024, Sun 4th Aug 2024
Mon 12th Aug 2024
Mon 9th Sep 2024
Mon 14th Oct 2024
Sat 9th Nov 2024, Sun 10th Nov 2024
Mon 11th Nov 2024
Mon 9th Dec 2024







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


