We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
The Certified Information Security Manageror CISM Requirements are of the highest calibre owing to globally recognised standard Information Security Management. CISM professionals possess the expertise and knowledge required to establish and manage an enterprise's Information Security program effectively.
A 2023 Statista survey revealed that about 50 percent of employees in the security domain were CISM-certified, validating the importance of these skills in computing worldwide. Furthermore, salary statistics from Payscale indicate that accredited CISM professionals in the UK make around GBP 60,800 annually. Read this blog and learn about the CISM Requirements and to understand more about the difference between cisa vs cism.
Table of Contents
1) What is CISM?
2) CISM vs. CISSP
3) CISM Certification Requirements
4) Key features of CISM
5) Benefits of CISM
6) Use cases of CISM
7) CISM Certification and CISM Certification cost
8) CISM: Jobs and salary benefits
9) Conclusion
What is CISM?
Certified Information Security Manager (CISM) is a globally recognised certification, that is offered by ISACA, a non-profit professional association dedicated to the audit, control, and security of information systems. Here are some key points of the CISM certification:
1) Focus on management: Unlike some certifications, which focus on the technical aspects of Information Security, it is designed for the management side of Information Security and assurance.
2) Four domains: The CISM exam covers the following domains within the Information Security Management:
a) Information Security governance: Unlike some certifications which are heavily focused on the technical aspects of Information Security governance framework and supporting processes.
b) Information risk management: Identifying and managing Information Security risks to achieve business objectives.
c) Information Security program development and management: Planning, establishing and managing the capability to respond to and recover from disruptive and destructive information security incidents.
3) Experience requirements: The CISM requirements for a candidate answering the CISM exam, must have five years of experience, in more than three or four domains.
4) Continued education: ISACA requires CISM certificate holders to follow the organisation's continuing education and ethical standards. This ensures that certified professionals stay current in Information Security.
CISM vs. CISSP
Certified Information Systems Security Professional or CISSP is quite different from CISM. On one hand, CISSP looks at Information Security from a technical perspective. However, CISM, by ISACA requires the professionals to look at Information Security from a business point of view. CISM Certifications are directed towards the management, or those who want to reach the management position. However, a CISSP Certification is targeted towards candidates who want to gain an in-depth knowledge about Information Security. Along with technical knowledge, CISSP certification also requires some managerial responsibilities.
|
Criteria |
CISM |
CISSP |
|
Offered by |
ISACA |
(ISC)² |
|
Focus |
Management and governance |
Management and governance |
|
Domains |
4 |
8 |
|
Experience |
5 years (3 in three domains) |
5 years (in two or more domains) |
|
Duration |
4 hours |
3 hours |
|
Renewal |
Every 3 years |
Every 3 years |
Register for our CISM Training Course to avail better employment prospects!
CISM Certification Requirements
As per ISACA, to obtain the CISM Certification, candidates must meet specific requirements. These include a minimum of five years of work experience in Information Security Management, with at least three years in three or more of the CISM domains. Also, individuals interested in how to become CISM certified should familiarize themselves with these prerequisites.
Additionally, candidates must pass the CISM exam, which covering four domains: Information Security Governance, Information Security Program Development and Management, Risk Management, and Information Security Incident Management.
Key features of CISM
CISM comprises key features such as:
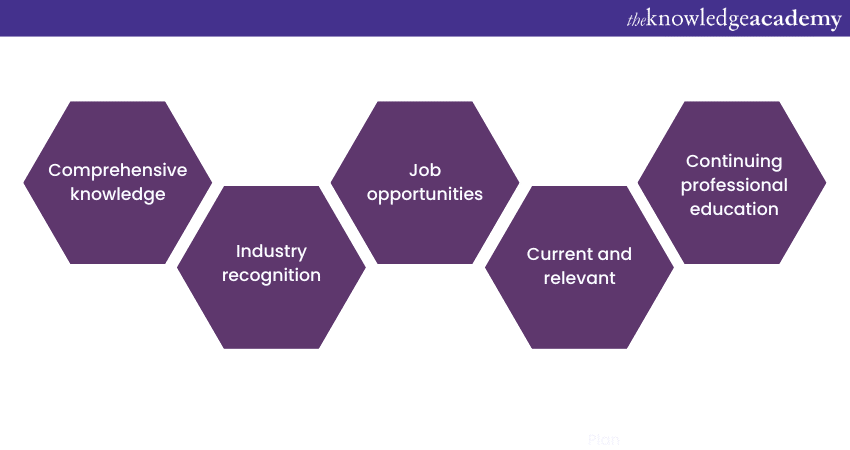
Comprehensive knowledge
CISM equips professionals with a holistic understanding of Information Security Management, covering essential concepts, practices, and frameworks.
Industry recognition
On global recognition, CISM Certification enhances professional credibility and demonstrates a commitment to the highest standards of Information Security.
Job opportunities
CISM opens doors to various career opportunities, including roles such as Information Security Manager, IT Auditor, Risk Analyst, and Compliance Officer.
Current and relevant
CISM's content is regularly updated to align with the latest industry trends, technologies, and best practices.
Continuing professional education
CISM requires ongoing professional education, ensuring certified professionals stay up-to-date with evolving security challenges and solutions.
Benefits of CISM
The benefits of CISM are as follows:
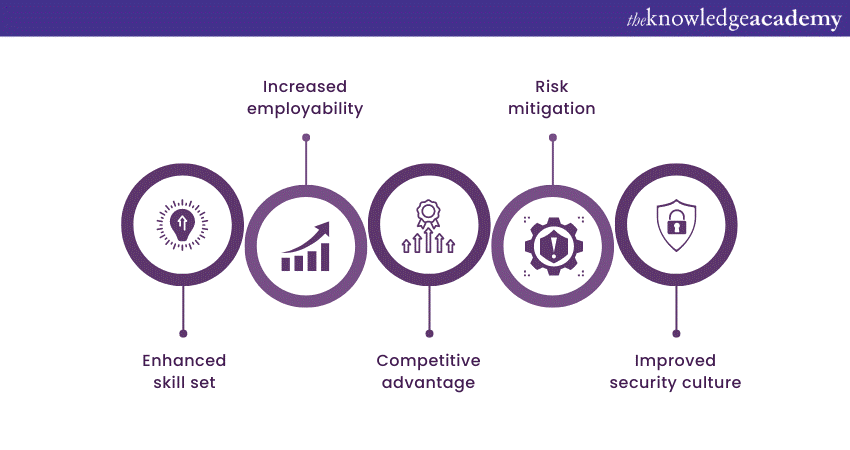
1) Enhanced skill set: CISM Certification provides professionals with a wide range of skills, enabling them to effectively address complex Information Security challenges.
2) Increased employability: Employers highly value CISM. Hence, CISM makes certified professionals more marketable and increases their chances of career advancement, especially when candidates are well-prepared with insights from CISM interview questions.
3) Competitive advantage: CISM Certification sets individuals apart from their peers, demonstrating their commitment to continuous learning and professional growth.
4) Risk mitigation: CISM professionals possess the expertise to identify and manage risks, safeguarding organisations against potential threats and vulnerabilities.
5) Improved security culture: CISM promotes a culture of security awareness within organisations, fostering a proactive approach to Information Security across all levels.
Enhance your Information Security management skills with CISM Training Sign up now!
Use cases of CISM
CISM comprises use cases, such as the following:
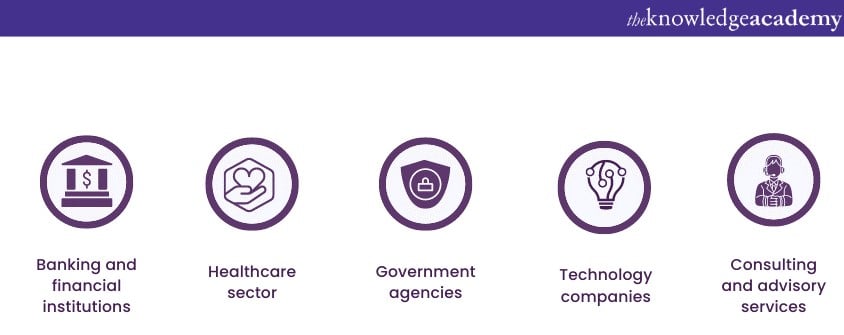
Healthcare sector
With the growing digitisation of healthcare records, CISM professionals are instrumental in maintaining the confidentiality of sensitive data such as patient information.
Government agencies
Government organisations handle vast amounts of sensitive data, making CISM professionals essential for establishing robust Information Security programs, detecting and mitigating cyber threats, and ensuring compliance with regulations.
Technology companies
CISM-certified experts help technology companies build secure products, protect customer data, and establish strong security practices across their organisations.
Consulting and advisory services
CISM professionals offer their expertise as consultants, assisting organisations in developing and implementing effective Information Security strategies tailored to their specific needs.
Consulting and advisory services
CISM professionals offer their expertise as consultants, assisting organisations in developing and implementing effective Information Security strategies tailored to their specific needs.
CISM Certification and CISM Certification cost
ISACA provides CISM Certification and is recognised globally. If you are a member of ISACA, early registration will cost £332.58. But if you are a non-member then it will cost around £436.76. For the final registration, ISACA members will have to pay £372.65, while non-members will pay around £476.83. However, before you register for ISACA Certifications, you should first know about the eligibility criteria and the CISM exam.
To take the exam, candidates need to have prior work experience. Candidates must have five years of experience in three or four domains. After candidates have attempted the exam and earned the CISM Certifications, they have to still maintain this certification. Candidates must take 120 Continuing Professional Education (CPE) hours over a span of three year, with a minimum of 20 hours in each year.
CISM: Jobs and salary benefits
After getting a CISM Certification, you can get jobs several roles with decent CISM Salary benefits. Some of these roles are:
1) Information Security Manager: This is the major role that candidates take up after completing this certification. This role involves looking after the Information Security program of an organisation. According to Glassdoor, the average salary of an Information Security Manager is £69,506/year.
2) IT Governance: In this role, candidates are given the responsibility to look after the IT and maintain the security controls of the organisation. According to Glassdoor, the average salary of IT Governance is around £44,732 per year.
3) Risk Manager: In this role, the professionals are responsible for identifying, assessing, and prioritising risks to an organisation's information assets. In this role, a Risk Manager can earn approximately around £67,384 /year, according to Glassdoor.
Conclusion
The Certified Information Security Manager (CISM) Requirements may be rigorous, but worth the effort. It is a valuable asset for professionals seeking a successful career in Information Security Management. And its rigorous requirements, comprehensive content, and industry recognition make it a sought-after credential. CISM-certified professionals have enhanced skill sets, increased employability, and can contribute to creating a secure digital landscape.
Learn to mitigate risk and manage data security, by signing up for the Certified Information Security Manager Training now!
Frequently Asked Questions

Professional development and continuing education can fulfil CISM eligibility criteria by providing relevant experience hours. CISM requires at least five years of work experience in Information Security Management, with at least three years of experience in at least three of the four CISM domains. Earning continuing education credits through relevant courses and certifications can contribute to meeting these experience requirements.

CISM prerequisites are flexible across varying industry backgrounds. Candidates need at least five years of work experience in Information Security Management, with at least three years in at least three of the four CISM domains. However, the nature of this experience can vary, allowing professionals from diverse industries to qualify, including those in IT, finance, and healthcare. The experience must demonstrate a comprehensive understanding of Information Security Management.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various CISM Courses. These courses cater to different skill levels, providing comprehensive insights into CISM Certifications.
Our IT Security & Data Protection blogs covers a range of topics related to CISM Training, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Data Protection skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 CISM Certified Information Security Manager
CISM Certified Information Security Manager
Sat 3rd Aug 2024, Sun 4th Aug 2024
Mon 12th Aug 2024
Mon 9th Sep 2024
Mon 14th Oct 2024
Sat 9th Nov 2024, Sun 10th Nov 2024
Mon 11th Nov 2024
Mon 9th Dec 2024
Mon 6th Jan 2025
Mon 3rd Feb 2025
Mon 3rd Mar 2025
Mon 14th Apr 2025
Tue 6th May 2025
Mon 2nd Jun 2025
Mon 7th Jul 2025
Mon 4th Aug 2025
Mon 1st Sep 2025
Mon 6th Oct 2025
Mon 3rd Nov 2025
Mon 1st Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


