We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Today, businesses rely heavily on technology. Hence, the threat of cyberattacks looms larger than ever. Understanding the intricacies of these attacks is crucial to developing effective defence strategies. One such method employed by hackers is the Cyber Kill Chain.
According to a digital defence report by Microsoft in 2022, more than 92% of companies were affected by critical data loss due to cyberattacks. Therefore, understanding the mindset of these hackers is essential if organisations want to protect themselves against these attacks. In this blog post, you will learn about Cyber Kill Chain, its stages and real-life examples to shed light on its significance in cybersecurity.
Table of Contents
1) What is Cyber Kill Chain?
2) The stages of Cyber Kill Chain
3) Why does Cyber Kill Chain matter?
4) Real-life examples of Cyber Kill Chain
5) Conclusion
What is Cyber Kill Chain?
The Cyber Kill Chain is a systematic framework used by cybersecurity professionals to understand and analyse the stages of a cyberattack. Derived from military strategies, this concept breaks down the attack lifecycle into distinct phases. Beginning with reconnaissance, where hackers gather information about their target, it progresses through stages like weaponisation, delivery, exploitation, installation, command and control, and culminates in actions on objectives. Each stage represents a critical step in the attack process, allowing organisations to anticipate, prevent, and mitigate potential threats effectively.
By comprehending the Cyber Kill Chain, security experts can gain valuable insights into the attacker's mindset and methodology. This understanding enables the development of proactive security measures, ensuring a robust defence against evolving cyber threats. By disrupting the chain at any point, organisations can thwart attacks, safeguard sensitive data, and maintain the integrity of their digital infrastructure.
Elevate your knowledge so that you can fortify your organisation against malware attacks. Register now for our Cyber Security Training!
The stages of Cyber Kill Chain
The stages of the Cyber Kill Chain outline the sequential steps followed by attackers to infiltrate a target system. Understanding these stages enables security professionals to fortify their defences effectively. These stages are as follows:
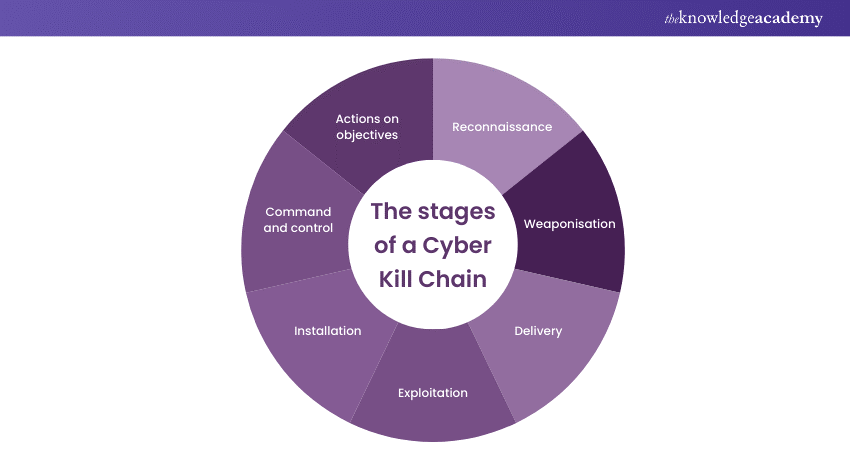
Reconnaissance
The Cyber Kill Chain begins with reconnaissance, where attackers gather information about the target. This phase involves meticulous exploration, wherein hackers employ various techniques such as passive scanning, social engineering, and open-source intelligence gathering. The objective is to identify potential vulnerabilities, understand the target's infrastructure, and recognise critical individuals within the organisation. By comprehensively mapping the target, attackers can refine their strategies, making subsequent stages more potent.
Weaponisation
Armed with valuable insights from the reconnaissance phase, attackers move on to weaponisation. In this stage, malicious tools and exploits are crafted or acquired to capitalise on the identified vulnerabilities. These tools can range from sophisticated malware and viruses to seemingly innocuous yet potent phishing emails. Weaponisation transforms gathered intelligence into deployable weapons, tailor-made to exploit specific weaknesses within the target's system. By embedding these tools into seemingly harmless files or emails, attackers set the stage for the subsequent phases of the kill chain.
Delivery
Once the malicious payload is ready, attackers focus on delivery, the phase where the weaponised content is transmitted to the target. Delivery methods are diverse, including email attachments, compromised websites, and removable media. Phishing emails, for instance, lure unsuspecting users into clicking malicious links or downloading infected attachments. Successful delivery marks a critical juncture in the Cyber Kill Chain, as it determines whether the attack gains entry into the target environment or is thwarted by vigilant security measures.
Exploitation
In the exploitation phase, attackers take advantage of vulnerabilities within the target system. These vulnerabilities can be related to software flaws, misconfigurations, or user behaviours. Exploitation allows the attacker to bypass security mechanisms and gain unauthorised access. Standard techniques include SQL injections, buffer overflows, and zero-day exploits. By exploiting these vulnerabilities, attackers achieve a pivotal breakthrough, paving the way for the subsequent stages of the kill chain.
Installation
Once inside the target system, attackers proceed with the installation phase. During this stage, the malicious payload is installed, establishing a persistent presence within the compromised environment. Malware, rootkits, or backdoors are deployed, enabling the attacker to maintain control over the system. Installation ensures that the attacker can re-enter the system even if discovered and ejected, supporting access for extended periods to conduct various malicious activities.
Command and control
Establishing command and control (C2) is a critical phase where attackers create a communication channel between the compromised system and their external infrastructure. Through this channel, attackers can remotely control the compromised system, execute commands, update malware, and exfiltrate data. C2 mechanisms are often designed to be stealthy, disguising their activities amidst legitimate network traffic to evade detection. This phase allows attackers to have control over the compromised environment, enabling them to adapt their tactics based on the evolving security landscape.
Actions on objectives
The final stage of the Cyber Kill Chain, actions on objectives, represents the attacker's goal. This could involve data theft, financial fraud, service disruption, or any other malicious activity intended to fulfil the attacker's objectives. By this stage, the attacker has navigated the entire kill chain, leveraging each phase to achieve their malicious intent. The success of actions on goals signifies the culmination of the cyberattack, with potentially severe consequences for the targeted organisation.
Gain expertise in cyber security with our Certified Cyber Security Professional (CCS-PRO) Course. Join now!
Why does Cyber Kill Chain matter?
Cyber Kill Chain matters due to the following reasons:
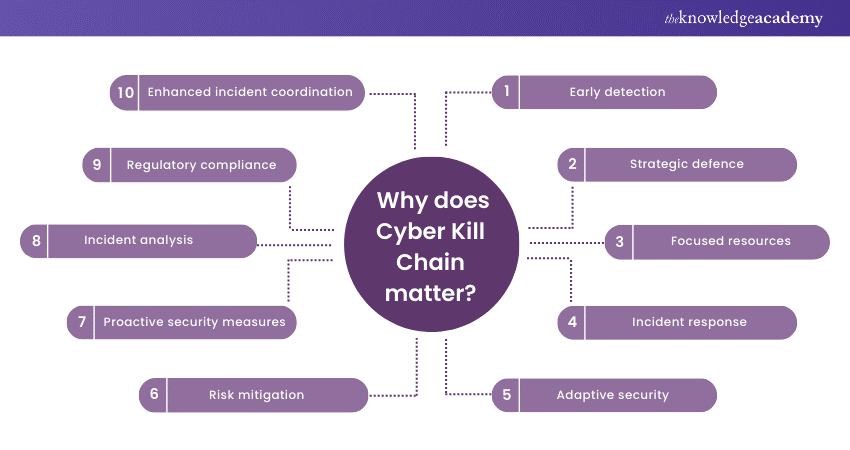
a) Early detection: Recognising the stages allows for early detection of an attack. Identifying and stopping an intrusion at an early stage can prevent significant data breaches and system compromises.
b) Strategic defence: It facilitates a strategic defence approach. Security teams can design specific countermeasures for each stage, making it difficult for attackers to progress.
c) Focused resources: By understanding where an attack is in the Cyber Kill Chain, organisations can allocate resources efficiently. They can concentrate efforts and investments on vulnerable stages, optimising their cybersecurity budgets.
d) Incident response: In the event of a successful breach, understanding the Kill Chain aids in incident response. It helps in tracing back the attack, understanding the extent of the damage, and fortifying defences to prevent future similar attacks.
e) Adaptive security: Cybersecurity strategies can evolve based on the evolving tactics of attackers. Understanding the Kill Chain allows for adaptive security measures to ensure that defences stay ahead of emerging threats.
f) Risk mitigation: By disrupting the Chain, organisations mitigate risks effectively. This disruption prevents attackers from reaching their objectives and safeguarding their critical data and infrastructure.
g) Comprehensive understanding: Deep comprehension of the Cyber Kill Chain provides a holistic view of an attack, enabling security professionals to anticipate attacker behaviour and tactics.
h) Proactive security measures: Armed with knowledge of the Kill Chain, organisations can proactively implement security measures at each stage, reducing the likelihood of successful attacks.
i) Threat intelligence utilisation: Understanding it aids in the effective utilisation of threat intelligence. It allows organisations to correlate threat data with specific stages, enhancing the accuracy of threat detection.
j) Incident analysis: Post-incident analysis benefits from the Cyber Kill Chain framework. Security teams can reconstruct the attack timeline, identify points of failure, and strengthen defences against similar future attacks.
k) Training and awareness: It forms a basis for educating employees and stakeholders about the anatomy of cyber threats. Understanding the Kill Chain helps in explaining the importance of security protocols and vigilance at all levels of an organisation.
l) Regulatory compliance: Many regulatory frameworks emphasise understanding and defending against cyber threats. Knowledge of the Kill Chain ensures compliance by demonstrating a proactive approach to cybersecurity.
m) Third-party risk management: For businesses dealing with multiple vendors, understanding the Kill Chain is vital. It helps in assessing the security postures of third-party entities, ensuring they adhere to the same rigorous standards.
n) Enhanced incident coordination: In case of a large-scale attack involving various stakeholders, understanding the Kill Chain ensures effective coordination between different entities, leading to a faster and more effective response.
o) Business continuity: By disrupting the Kill Chain, businesses ensure continuous operations. Preventing successful attacks means avoiding downtime, financial losses, and reputational damage.
p) Innovation in security solutions: Cybersecurity companies leverage the Kill Chain model to innovate and develop advanced security solutions. This continuous innovation leads to the creation of more robust tools to counter evolving threats.
q) Global collaboration: The understanding of the Cyber Kill Chain is universal. It forms a common language for global collaboration and information sharing, enabling the cybersecurity community to unite against cyber threats collectively.
r) Protection of intellectual property: For research-intensive industries, understanding and disrupting the Kill Chain is crucial. It prevents industrial espionage and safeguards valuable intellectual property from falling into the wrong hands.
Equip your team with essential knowledge – Sign up now for our Cyber Security Awareness Training!
Real-life example of Cyber Kill Chain
The WannaCry ransomware attack of May 2017 stands as a real-life example of the Cyber Kill Chain in action, highlighting the devastating impact of a well-executed cyberattack. This incident demonstrated how cybercriminals systematically progressed through the stages of the Kill Chain, causing widespread disruption and financial losses.
1) Reconnaissance: The attackers behind WannaCry exploited a vulnerability in Microsoft Windows operating systems, primarily targeting unpatched systems. They likely scanned the internet for systems lacking critical security updates.
2) Weaponisation: The attackers weaponised the EternalBlue exploit, a hacking tool allegedly developed by the National Security Agency (NSA). This exploit allowed the ransomware to propagate across vulnerable systems, turning them into victims rapidly.
3) Delivery: WannaCry was delivered primarily through phishing emails containing malicious attachments. Once opened, these attachments executed the ransomware on the user’s system, initiating the encryption process.
4) Exploitation: Upon execution, WannaCry exploited the EternalBlue vulnerability, enabling it to spread laterally within networks. This exploitation tactic allowed the ransomware to infect connected devices, including computers and servers, amplifying the scale of the attack.
5) Installation: After exploiting the vulnerability, WannaCry installed itself on the compromised systems, encrypting files and rendering them inaccessible to users. Victims were then presented with ransom notes, demanding payment in Bitcoin in exchange for decryption keys.
6) Command and control: While WannaCry didn’t have a traditional command and control infrastructure, it utilised hardcoded domains to establish communication with the attackers. This connection allowed the ransomware to confirm successful infections and manage the ransom payments.
7) Actions on objectives: The attackers’ objective was financial gain through ransom payments. Victims, including large organisations and governmental institutions, were coerced into paying ransoms to regain access to their critical files and systems.
The WannaCry attack serves as a stark reminder of the Cyber Kill Chain's relevance. By understanding and disrupting any stage of the Kill Chain, organisations can prevent similar large-scale attacks. It also helps to emphasise the critical importance of proactive cybersecurity measures in today’s interconnected digital world.

Conclusion
Understanding the Cyber Kill Chain provides a strategic advantage. By understanding the stages of an attack, businesses can bolster their defences, ensuring a robust security infrastructure. As technology continues to advance, staying one step ahead of cybercriminals is not just a choice; it’s a necessity.
Build a foundation for a secure digital future – Sign up now for our course on Introduction to System and Network Security.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 9th Aug 2024
Fri 6th Dec 2024
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


