Get a custom course package
We may not have any package deals available including this course. If you enquire or give us a call on 01344203999 and speak to our training experts, we should be able to help you with your requirements.
Module 1: Introduction to ISO 27701
Module 2: General
Module 3: PIMS-Specific Requirements Related to ISO/IEC 27001
Module 4: PIMS – Specific Guidance Related to ISO/IEC 27002
Module 5: Additional ISO/IEC 27002 Guidance for PII Controllers
Module 6: Additional ISO/IEC 27002 Guidance for PII Processors


The ISO 27701 Privacy Information Management System Course is tailored for professionals and managers involved in managing privacy and data protection aspects within organisations. This course is beneficial for various professionals including:
There are no formal prerequisites for attending this ISO 27701 Privacy Information Management System Course.
In today's digital age, privacy and data protection are more critical than ever. An ISO 27701 PIMS Certification helps you understand the framework for organisations to manage personal data effectively and comply with global privacy regulations. This standard extends ISO 27001, offering a comprehensive approach to managing privacy information, which is vital for building trust and ensuring data security.
Understanding and mastering ISO 27701 is essential for professionals involved in data protection and privacy management. With increasing data breaches and stringent regulations, acquiring an ISO 27701 PIMS Certification is invaluable for IT Managers, Compliance Officers, and Data Protection Officers. It ensures they can implement robust privacy information management systems that meet international standards and legal requirements.
This 1-day ISO 27701 Certification Training by The Knowledge Academy equips delegates with the knowledge and skills to implement and manage a Privacy Information Management System (PIMS). Through expert instruction and practical exercises, delegates will gain a thorough understanding of ISO 27701 standards, enabling them to enhance their organisation's data privacy protocols effectively and efficiently.
Course Objectives
Upon completion of this ISO 27701 Certification Training, delegates will be proficient in establishing, implementing, and maintaining a Privacy Information Management System. They will be equipped to ensure their organisation's compliance with ISO 27701 standards, effectively safeguarding personal data and maintaining privacy integrity.




To achieve the ISO 27701 Privacy Information Management System Training, candidates will need to sit for an examination. The exam format is as follows:


Why choose us
Experience live, interactive learning from home with The Knowledge Academy's Online Instructor-led ISO 27701 Privacy Information Management System. Engage directly with expert instructors, mirroring the classroom schedule for a comprehensive learning journey. Enjoy the convenience of virtual learning without compromising on the quality of interaction.
Unlock your potential with The Knowledge Academy's ISO 27701 Privacy Information Management System, accessible anytime, anywhere on any device. Enjoy 90 days of online course access, extendable upon request, and benefit from the support of our expert trainers. Elevate your skills at your own pace with our Online Self-paced sessions.
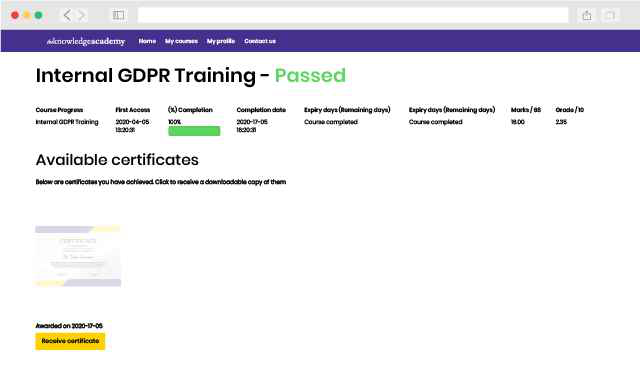
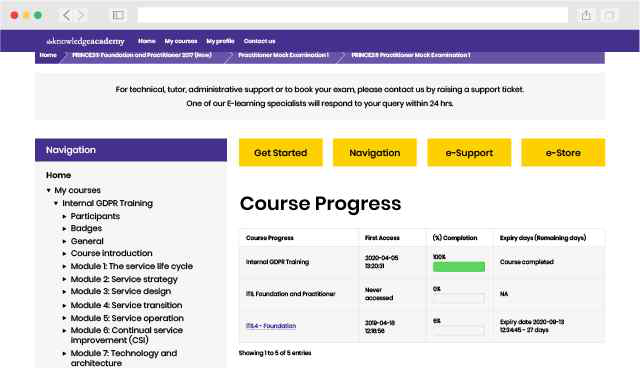
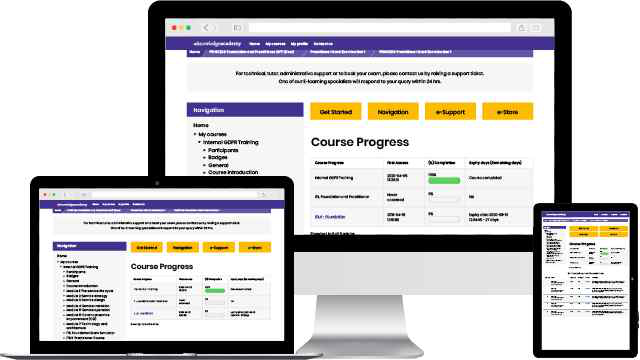
Experience the most sought-after learning style with The Knowledge Academy's ISO 27701 Privacy Information Management System. Available in 490+ locations across 190+ countries, our hand-picked Classroom venues offer an invaluable human touch. Immerse yourself in a comprehensive, interactive experience with our expert-led ISO 27701 Privacy Information Management System sessions.

Boost your skills with our expert trainers, boasting 10+ years of real-world experience, ensuring an engaging and informative training experience

We only use the highest standard of learning facilities to make sure your experience is as comfortable and distraction-free as possible

Our Classroom courses with limited class sizes foster discussions and provide a personalised, interactive learning environment

Achieve certification without breaking the bank. Find a lower price elsewhere? We'll match it to guarantee you the best value
Streamline large-scale training requirements with The Knowledge Academy’s In-house/Onsite ISO 27701 Privacy Information Management System at your business premises. Experience expert-led classroom learning from the comfort of your workplace and engage professional development.

Leverage benefits offered from a certification that fits your unique business or project needs

Cut unnecessary costs and focus your entire budget on what really matters, the training.

Our ISO 27701 Privacy Information Management System offers a unique chance for your team to bond and engage in discussions, enriching the learning experience beyond traditional classroom settings

The course know-how will help you track and evaluate your employees' progression and performance with relative ease


You won't find better value in the marketplace. If you do find a lower price, we will beat it.

Flexible delivery methods are available depending on your learning style.

Resources are included for a comprehensive learning experience.




"Really good course and well organised. Trainer was great with a sense of humour - his experience allowed a free flowing course, structured to help you gain as much information & relevant experience whilst helping prepare you for the exam"
Joshua Davies, Thames Water



 London
London Birmingham
Birmingham Bristol
Bristol Milton Keynes
Milton Keynes Manchester
Manchester Reading
Reading Glasgow
Glasgow Edinburgh
Edinburgh Southampton
Southampton Virtual
Virtual Bath
Bath Liverpool
Liverpool Nottingham
Nottingham Bedford
Bedford Bolton
Bolton Newcastle
Newcastle Brighton
Brighton Bournemouth
Bournemouth Bracknell
Bracknell Cardiff
Cardiff Bromley
Bromley Cambridge
Cambridge Burton Upon Trent
Burton Upon Trent Norwich
Norwich Buxton
Buxton Sheffield
Sheffield Belfast
Belfast Dublin
Dublin Canterbury
Canterbury Aberdeen
Aberdeen Maidstone
Maidstone Carlisle
Carlisle Chatham
Chatham Chelmsford
Chelmsford Chester
Chester Chichester
Chichester Chorley
Chorley Cirencester
Cirencester Colchester
Colchester Corby
Corby Coventry
Coventry Crewe
Crewe Darlington
Darlington Derby
Derby Doncaster
Doncaster Dundee
Dundee Dunfermline
Dunfermline Exeter
Exeter Fleet
Fleet Gatwick
Gatwick Gloucester
Gloucester Guildford
Guildford Harrogate
Harrogate Heathrow
Heathrow High Wycombe
High Wycombe Hinckley
Hinckley Inverness
Inverness Ipswich
Ipswich Kingston upon Hull
Kingston upon Hull Lincoln
Lincoln Leicester
Leicester Luton
Luton Middlesbrough
Middlesbrough Northampton
Northampton Oxford
Oxford Peterborough
Peterborough Plymouth
Plymouth Poole
Poole Portsmouth
Portsmouth Preston
Preston Slough
Slough Solihull
Solihull Stoke-on-Trent
Stoke-on-Trent Sunderland
Sunderland Swansea
Swansea Swindon
Swindon Teesside
Teesside Tonbridge
Tonbridge Wakefield
Wakefield Warrington
Warrington Warwick
Warwick Watford
Watford Windsor Town
Windsor Town Wokingham
Wokingham Wolverhampton
Wolverhampton Worcester
Worcester Wrexham
Wrexham York
York
 Back to course information
Back to course information
We may not have any package deals available including this course. If you enquire or give us a call on 01344203999 and speak to our training experts, we should be able to help you with your requirements.
 If you miss out, enquire to get yourself on the waiting list for the next day!
If you miss out, enquire to get yourself on the waiting list for the next day!

close


Press esc to close

close
Fill out your contact details below and our training experts will be in touch.



Back to Course Information