We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Diving deep into the Cybersecurity domain, one cannot overlook the significance of the Penetration Testing Phases. These phases form the backbone of any strong security assessment, ensuring vulnerabilities are identified and addressed effectively. By understanding each phase, businesses and security professionals can fortify their digital infrastructures against potential threats.
Yet, many remain unaware or only have a superficial knowledge of these stages. This blog aims to demystify the Penetration Testing Phases, providing you with a clear roadmap for effective security testing. Navigate through to gain essential insights and bolster your defence strategies.
Table of Contents
1) Understanding Penetration Testing
2) Phases of Penetration Testing
3) Tools and technologies
4) Popular Penetration Testing software
6) Conclusion
Understanding Penetration Testing
Penetration Testing, or "pen testing," is a security assessment technique designed to identify system infrastructure vulnerabilities. By simulating real-world attacks, organisations can uncover potential limitations and address them before malicious actors exploit them.
Penetration Testing goes beyond automated vulnerability scans. It involves a systematic and controlled process of simulating cyberattacks to assess the security of an organisation's systems, applications, and networks. By imitating potential attackers' Tactics, Techniques, and Procedures (TTPs), Penetration Testing provides valuable insights into an organisation's security posture.
Penetration Testing serves as a proactive approach to Cybersecurity, offering the following advantages:
1) Identification of hidden vulnerabilities: Vulnerabilities in software, hardware, configurations, and processes are inevitable, but they may not always be apparent through regular security measures. Penetration Testing goes beyond surface-level assessments, revealing vulnerabilities that automated vulnerability scans or routine security checks might have missed.
2) Realistic testing environment: Penetration Testing creates a controlled environment that closely simulates actual cyberattacks. It enables organisations to understand how attackers might exploit vulnerabilities and the impact of those exploits on their systems and data.
3) Enhanced incident response preparedness: A swift and effective incident response is crucial to minimising damage in a real cyberattack. Penetration Testing helps organisations identify weak points in their incident response plans, allowing them to refine and improve these strategies.
4) Compliance and regulation: Many industries are under the purview of regulatory requirements that demand a certain level of Cybersecurity. Penetration Testing assists organisations in meeting these compliance standards by providing evidence of their dedication to identifying and addressing security vulnerabilities.
5) Risk mitigation: By proactively identifying and addressing vulnerabilities before malicious actors can exploit them, Penetration Testing helps organisations reduce their risk of cyberattacks, data breaches, financial losses, and reputational damage.

Phases of Penetration Testing
Penetration Testing is not a singular action but a comprehensive process encompassing several distinct phases. These phases are meticulously designed to provide a systematic approach to identifying vulnerabilities, assessing risks, and improving an organisation's overall Cybersecurity posture. Let's explore each of this phase in detail:
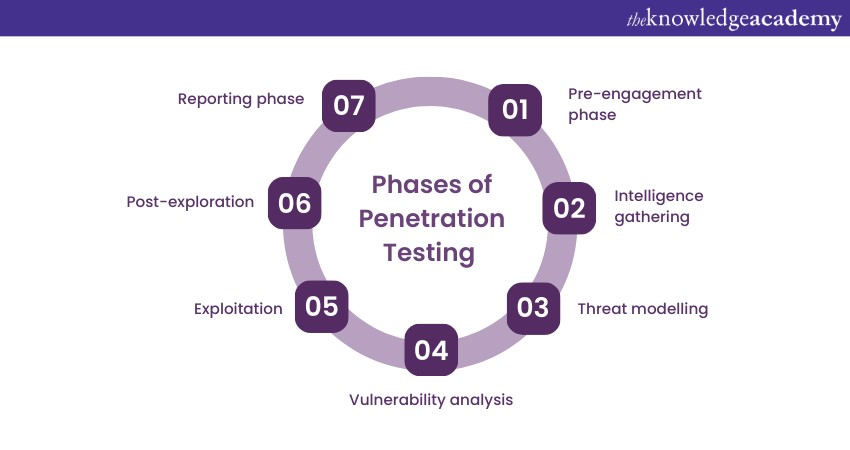
1) Pre-engagement phase: Before diving into the technical aspects of Penetration Testing, it is essential to establish clear communication between the organisation and the testing team. In the pre-engagement phase, the scope and objectives of the test are defined. It involves understanding the organisation's goals, identifying critical systems to be tested, and establishing the rules of engagement.
Defining these parameters ensures that the testing aligns with the organisation's expectations and focuses on the most pertinent areas of concern.
2) Intelligence gathering: The intelligence gathering phase is akin to the reconnaissance phase in actual cyberattacks. Penetration Testers collect information about the target organisation, including its network infrastructure, domains, IP addresses, and potential entry points.
This phase helps testers gain insights into the organisation's digital footprint, the relationships between different systems, and potential vulnerabilities.
3) Threat modelling: With the collected intelligence, Penetration Testers proceed to threat modelling. In this phase, they analyse the gathered data to assess potential threats and attack vectors. By putting themselves in the attackers' shoes, testers can identify the most likely paths malicious actors might take to breach the organisation's defences.
This step is crucial for prioritising vulnerabilities based on their potential impact and exploitation.
4) Vulnerability analysis: The vulnerability analysis phase involves actively identifying vulnerabilities within the target systems. This can be done through a combination of automated tools and manual testing. Automated vulnerability scanners scan systems for known vulnerabilities, while manual testing allows testers to explore more complex attack scenarios that automated tools might miss.
Exposures can range from misconfigurations and weak passwords to software vulnerabilities that can be exploited.
5) Exploitation: Once vulnerabilities have been identified, the Penetration Testers move on to the exploitation phase. Testers exploit the identified vulnerabilities in this stage to achieve unauthorised access to the target systems. This step helps validate the existence and potential impact of vulnerabilities.
It is important to note that Penetration Testers operate within ethical boundaries and ensure that their actions do not cause harm or disruption to the organisation's systems.
6) Post-exploitation: Testers proceed to the post-exploitation phase after successfully gaining access to the target systems. Here, they explore the extent of control they have over the compromised systems. Testers may aim to escalate privileges, move within the network, and gain sensitive data information.
This phase provides valuable insights into the potential consequences of a successful cyberattack, including data theft and unauthorised access.
7) Reporting phase: The insights gathered during the Penetration Testing process culminate in the reporting phase. A comprehensive and well-structured report is created detailing the test findings, including vulnerabilities discovered, their potential impact, and recommendations for mitigation.
The report is designed to be both technical, providing detailed information for IT and security teams to address the issues, and non-technical, offering executives a clear understanding of the risks and necessary actions.
Tools and technologies
Penetration Testers rely on diverse tools and technologies to effectively identify vulnerabilities, simulate attacks, and assess the resilience of an organisation's digital defences. These tools play a pivotal role in executing each phase of the Penetration Testing process, from surveillance to exploitation, ensuring a comprehensive evaluation of the target systems. Here's a comprehensive look at these tools:
1) Reconnaissance tools: Reconnaissance tools are the first step in the Penetration Testing process, aiding testers in gathering essential information about the target organisation. These tools help discover domain names, IP addresses, subdomains, and network infrastructure details, creating a foundation for subsequent testing phases.
Maltego and the Harvester are examples of reconnaissance tools that assist in building a comprehensive picture of the organisation's digital footprint.
2) Vulnerability scanners: Automated vulnerability scanners are crucial for identifying potential weaknesses within target systems. These tools scan networks and applications for known vulnerabilities, misconfigurations, and common security issues.
Popular vulnerability scanners include Nessus, OpenVAS, and Nexpose. However, it is important to note that while these scanners are powerful aids, manual testing is essential to uncover more intricate vulnerabilities.
3) Exploitation frameworks: Exploitation frameworks provide Penetration Testers with various tools and exploits to simulate attacks on vulnerable systems. These frameworks offer a streamlined approach to executing attacks and verifying the existence of vulnerabilities. Metasploit is one of the most widely used exploitation frameworks, offering many exploits, payloads, and post-exploitation modules.
4) Password cracking tools: Weak or default passwords are a common entry point for cyberattacks. Password cracking tools are designed to test the strength of passwords and identify those susceptible to brute-force attacks. Tools like John the Ripper and Hashcat are employed to crack password hashes, aiding testers in evaluating the organisation's password security measures.
5) Network sniffers and analysers: Network sniffers and analysers are essential for capturing and analysing network traffic. These tools help testers identify potential vulnerabilities in network communications, including sensitive data being transmitted in plaintext.
Wireshark is a famous network sniffer that allows testers to analyse packets and gain insights into the traffic patterns within a network.
Elevate your Cybersecurity prowess with our Ethical Hacking and Penetration Testing Training and delve into the world of ethical hacking and Penetration Testing
Popular Penetration Testing tools
Some of the most widely used tools for Penetration Testing are as follows:
a) Nmap: This tool can scan networks for open ports and services and detect vulnerable applications.
b) Metasploit: This tool can exploit vulnerabilities in various programs and systems and guide penetration testers in using the available exploits.
c) Wireshark: This tool can capture and analyse network traffic, and also reveal any malicious or sensitive data being sent over the network.
d) Burp Suite: This tool can test web applications for security flaws, and also modify and intercept the communication between the client and server.
Conclusion
Through Penetration Testing Phases, organisations are empowered to identify risks, respond effectively, and secure digital assets against the ever-evolving landscape of cyber threats. They can uncover vulnerabilities, fortify their defences, and enhance their digital resilience.
Explore our Ethical Hacker Training and gain the expertise to proactively identify vulnerabilities, secure systems, and contribute to a safer digital world.
Frequently Asked Questions

The four primary phases of a Penetration Test, in order, are reconnaissance, scanning, exploitation, and post-exploitation. During reconnaissance, information about the target is gathered. Scanning involves identifying live hosts and open ports. Exploitation entails actively probing for vulnerabilities and attempting to gain unauthorised access. Post-exploitation involves assessing the impact of successful exploits and documenting findings.

The right sequence for Penetration Testing involves:
1) Planning and reconnaissance
2) Scanning
3) Gaining access
4) Maintaining access
5) Analysis
This systematic approach helps identify and address vulnerabilities in a controlled manner, ensuring a thorough examination of a system's security. Regular testing is crucial for maintaining a robust defense against potential cyber threats.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Automation & Penetration Testing Courses, including Tools and Techniques for Penetrating Testing, Fundamentals of Test Automation etc. These courses cater to different skill levels, providing comprehensive insights into Cyber Security Skills.
Our IT Security & Data Protection Blogs covers a range of topics related to Fundamentals of Test Automation, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Fundamentals of Test Automation
Fundamentals of Test Automation
Fri 26th Jul 2024
Fri 22nd Nov 2024
Fri 17th Jan 2025
Fri 4th Apr 2025
Fri 3rd Oct 2025
Fri 12th Dec 2025







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


