We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Ethical hacking is a useful tool that helps to improve network security by identifying and solving system vulnerabilities. This industry requires a thorough understanding of intricate security systems and the skill to think like an attacker. As a result, the Ethical Hacker Interview process is sometimes seen as an insurmountable hurdle.
The fear of the questions that you might face can be very daunting, and the pressure of tackling complex queries unprepared might cost you valuable opportunities. Hence, we have curated this blog to help you through your journey. In this, we have discussed the top 20 Ethical Hacker Interview questions and answers. It will help you walk into your next interview with confidence and secure your dream job in Cybersecurity.
Table of Contents
1) Knowing what Ethical Hacking is
2) Essential skills and qualifications
3) Common Ethical Hacking Interview Questions
4) Behavioural and scenario-based questions
5) Technical questions and practical demonstrations
6) Conclusion
Knowing what Ethical Hacking is
Ethical Hacking, popularly known as white hat hacking or penetration testing, systematically identifies vulnerabilities and weaknesses in computer systems, networks, and applications. Ethical Hackers, authorised professionals with advanced technical skills, use their knowledge to simulate real-world cyber-attacks to assess an organisation's security posture. They employ various techniques and tools to uncover vulnerabilities and provide recommendations for remediation.
Role of Ethical Hackers
Ethical Hackers are vital in the field of cybersecurity. Their primary responsibility is proactively identifying potential security risks and vulnerabilities that malicious hackers could exploit. They provide valuable insights into the vulnerabilities and potential attack vectors that cybercriminals can use. This information allows organisations to patch or fix these vulnerabilities before they can be exploited, thereby minimising the risk of data breaches and unauthorised access.
Importance of Ethical Hacking in Cybersecurity
Ethical Hacking is paramount in ensuring organisations' and digital assets' overall security. Organisations can identify and address vulnerabilities by employing White hat hackers before malicious actors exploit them. This proactive approach helps in reducing the likelihood and impact of successful cyber-attacks. Ethical Hacking also enables organisations to assess security measures and ensure compliance with industry regulations and standards.
Try our Ethical Hacking Training and learn to legally bypass the security of systems!
Essential skills and qualifications
This segment will let you dive into the technical aspects of cybersecurity. Evaluating a candidate's knowledge of network protocols, vulnerability assessments, and practical demonstrations provides insights into their technical proficiency and ability to tackle real-world challenges.
Exploring these areas will allow you to identify individuals who possess the necessary skills to defend against cyber threats against their systems. Let's dive into the technical interview questions and practical demonstrations to gauge the candidate's expertise in Ethical Hacking.
Technical skills required for Ethical Hacking
Ethical Hackers require a range of technical skills to effectively identify vulnerabilities and secure computer systems. Some essential technical skills for Ethical Hacking include:
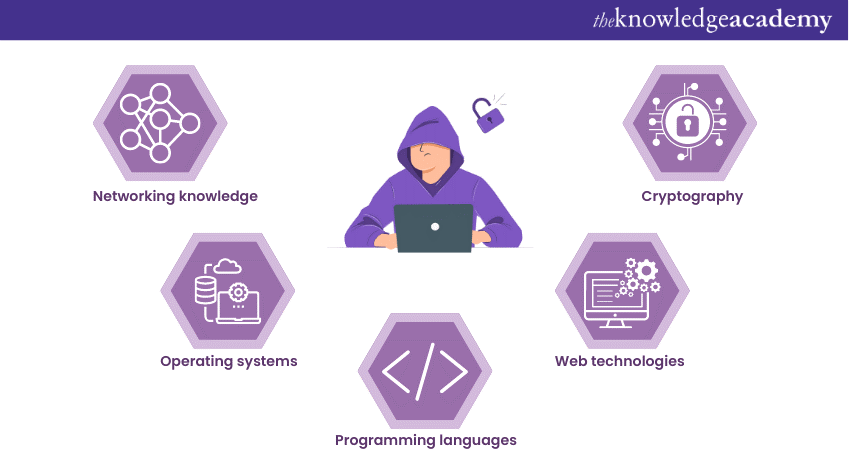
a) Networking knowledge: Understanding network protocols, TCP/IP, subnetting, routing, and firewall technologies is crucial. White hat hackers should be familiar with network architectures and be able to analyse network traffic for potential vulnerabilities.
b) Operating systems: Proficiency in various operating systems such as Windows, Linux, and macOS is necessary. Knowledge of their security features, file systems, and command-line interfaces allows white hat hackers to identify system weaknesses and exploit potential vulnerabilities.
c) Programming languages: Competence in programming languages like Python, C/C++, Java, or scripting languages such as PowerShell and Bash are beneficial. White hat hackers often need to write custom scripts to automate tasks, develop exploits, or analyse code for vulnerabilities.
d) Web technologies: Understanding web technologies like HTML, CSS, JavaScript, PHP, and SQL is vital for assessing web application security. White hat hackers should be capable of identifying common vulnerabilities on the web, such as Cross-Site Scripting (XSS), SQL injection, and insecure direct object references.
e) Cryptography: Knowledge of encryption algorithms, digital signatures, cryptographic protocols, and secure key management is essential for Ethical Hacking. Understanding cryptography allows them to assess the security of systems that rely on encryption to protect sensitive data.
Certifications for Ethical Hackers
Certifications play a significant role in validating the skills and knowledge of Ethical Hacking during an interview. Obtaining certifications demonstrates a commitment to professional development and provides credibility to white hat hackers. Some widely recognised certifications in the field include:
a) Certified Information Systems Security Professional (CISSP): Offered by (ISC)², the CISSP certification covers a broad range of cybersecurity domains, including Ethical Hacking. It validates expertise in areas such as access control, cryptography, network security, and security assessment.
b) Certified Information Security Manager (CISM): Offered by ISACA, the CISM certification is designed for professionals responsible for managing and overseeing information security systems. It covers topics like incident response, risk management, and ethical considerations in cybersecurity.
c) CompTIA Security+: This entry-level certification covers foundational knowledge in cybersecurity, including Ethical Hacking concepts. It validates skills in areas such as network security, threat management, and risk assessment.
Learn the basics of Ethical Hacking with Ethical Hacking Professional Course!
Common Ethical Hacking interview questions
As the demand for robust cybersecurity grows, organisations increasingly rely on Ethical Hacking to protect their digital assets from malicious attacks. White hat hackers play a crucial role in identifying vulnerabilities, fortifying defences, and ensuring the integrity of systems and networks. Interviews often include a series of common Ethical Hacking Interview questions to assess the competence and suitability of candidates in this field.
Diving into these essential topics will allow you to gain valuable insights into the candidate's suitability for the role of an Ethical Hacker. So, let's dive into the world of Ethical Hacking and explore the Common Interview Questions that will help you identify top talent in this critical field of Cybersecurity.
Question 1: What is the difference between white, black and grey hat hackers?
White hat hackers are often considered helpful and ethical in nature, also referred to as Ethical Hackers who identify vulnerabilities and secure systems, networks, and applications. They work with the system owner's permission to ensure the target's safety and integrity.
On the other hand, black hat hackers engage in unauthorised activities to exploit vulnerabilities for personal gain or malicious intent. Grey hat hackers fall somewhere in between, as they may breach systems without permission but do not have malicious intentions and may report the vulnerabilities they discover.
Question 2: Explain the steps involved in an Ethical Hacking process
The Ethical Hacking process typically involves the following steps:
a) Reconnaissance: Gathering information about the target system, such as IP addresses, domain names, and network infrastructure.
b) Scanning: Conducting network scans to identify open ports, services, and potential vulnerabilities.
c) Enumeration: Collecting more detailed information about the target, such as user accounts, shares, and system configurations.
d) Vulnerability Assessment: Identifying vulnerabilities and weaknesses in the target system using tools and manual techniques.
e) Exploitation: Attempting to exploit identified vulnerabilities to gain unauthorised access and control over the system.
f) Post-exploitation: Maintaining access, escalating privileges, and exploring the compromised system.
g) Reporting: Documenting findings, including vulnerabilities discovered, the impact they could have, and recommendations for mitigation.
Try our CompTIA Security+ Certification Training Course to counter Cybercrimes!
Question 3: How do you stay updated with the latest hacking techniques and security trends?
Staying updated with the latest hacking techniques and security trends is essential for an Ethical Hacker. I actively participate in online forums, security communities, and social media groups where professionals share insights and discuss emerging trends. I regularly read industry publications, research papers, and blogs from reputable sources. Attending security conferences, webinars, and training programs also allows me to enhance my knowledge and stay informed about the evolving threat landscape.
Question 4: What are some common types of cyber-attacks, and how would you defend against them?
Common cyber-attacks include phishing, malware attacks, DDoS (Distributed Denial of Service) attacks, SQL injection, and social engineering. Defending against these attacks requires a multi-layered approach. Implementing robust network and host-based security measures, such as firewalls, intrusion detection/prevention systems, and antivirus software, helps prevent and detect various attacks.
Regular security patching, strong access controls, and user awareness training are also crucial. Additionally, regular vulnerability assessments, penetration testing, and security audits allow organisations to proactively identify and mitigate potential weaknesses.
Question 5: Describe the concept of social engineering and how it can be used to exploit vulnerabilities
Social engineering is a technique that manipulates human psychology to deceive individuals into revealing sensitive information or performing actions that compromise security. Attackers may use impersonation, pretexting, or baiting tactics to exploit human trust and bypass technical security controls.
For example, a social engineer might pose as a trusted colleague or an IT support technician to trick individuals into sharing passwords or granting unauthorised access. Mitigating social engineering requires comprehensive user awareness training, strong authentication mechanisms, and strict adherence to security policies.
Question 6: What are the key components of a penetration testing report?
A penetration testing report typically includes the following key components:
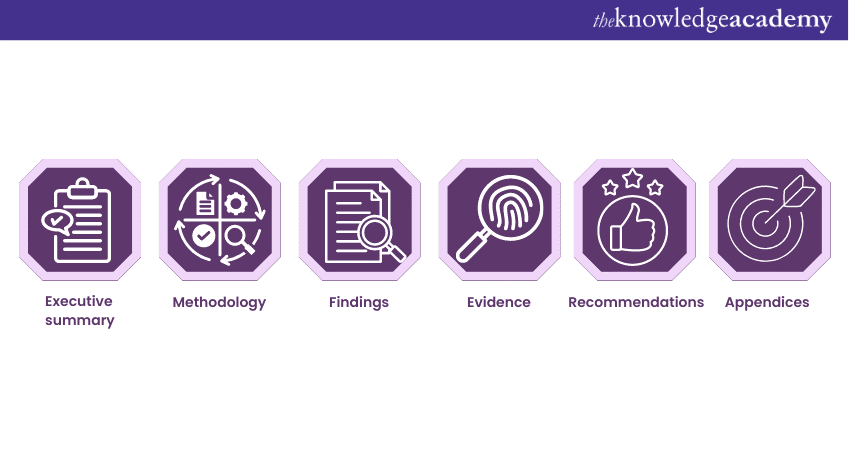
a) Executive summary: A high-level overview of the discoveries which highlight critical weaknesses and potential impact.
b) Methodology: Description of the approach, tools, and techniques used during the penetration testing process.
c) Findings: Detailed documentation of identified vulnerabilities, including their severity, impact, and recommendations for remediation.
d) Evidence: Supporting evidence, such as screenshots or logs, to validate the findings.
e) Recommendations: Clear and actionable suggestions for addressing the identified vulnerabilities and improving security.
f) Appendices: Additional information, such as network diagrams, test configurations, and technical details, to provide context and support the findings.
Question 7: How would you handle a situation where you discover a critical vulnerability in a client's system?
When encountering a critical vulnerability, handling the situation with care and following ethical guidelines is essential. Firstly, I would document the vulnerability and its potential impact. Then, I would promptly notify the client or the designated point of contact, providing a clear and detailed report of the vulnerability, including any necessary technical information.
I would offer recommendations and work closely with the client to develop an appropriate remediation plan. Maintaining open communication, professionalism, and confidentiality is crucial throughout the process.
Question 8: Discuss the importance of password security and suggest best practices.
Password security is crucial for protecting sensitive information and preventing unauthorised access. It is vital, as weak or compromised passwords can lead to unauthorised access and data breaches. Best practices include using complex passwords with uppercase and lowercase letters, numbers, and special characters.
Passwords should be unique for each account and regularly changed. Implementing multi-factor authentication provides an additional layer of security. Educating users about password hygiene, avoiding common password pitfalls, and using password management tools can significantly enhance password security.
Question 9: What are some encryption algorithms commonly used in securing data?
Several encryption algorithms are commonly employed to secure data. The Advanced Encryption Standard (AES) is widely adopted for symmetric encryption due to its robustness and efficiency. The RSA algorithm, an asymmetric encryption scheme, is commonly used for secure key exchange and digital signatures.
Triple Data Encryption Standard (3DES) applies the Data Encryption Standard (DES) cypher three times, enhancing security. Blowfish, a symmetric encryption algorithm, is known for its flexibility and effectiveness. Elliptic Curve Cryptography (ECC), an asymmetric encryption algorithm, offers strong security with shorter key lengths, making it suitable for resource-constrained environments like mobile devices.
Question 10: How would you conduct a wireless network security assessment?
The following steps can be followed in order to conduct a wireless network security assessment:
Conducting a wireless network security assessment involves a systematic approach to identify and mitigate potential vulnerabilities. It includes identifying wireless networks and their associated access points (APs), performing reconnaissance to gather information about the networks, and analysing encryption protocols.
It also includes conducting penetration testing to exploit vulnerabilities, detecting rogue APs, analysing wireless traffic for suspicious activities, deploying a wireless Intrusion Detection System (IDS) for continuous monitoring, and documenting the assessment findings and recommendations in a comprehensive report.
Try our Mastering Metasploit Framework Course and use Metasploit in penetration testing!
Behavioural and scenario-based questions
This segment dives into behavioural and scenario-based questions commonly asked during Ethical Hacking Interviews. These questions go beyond technical knowledge and provide insight into the candidate's decision-making processes, communication skills, and adaptability in real-world scenarios.
These interview questions allow recruiters to explore your experiences, problem-solving approaches, and ethical judgment, and interviewers can gauge the candidate's suitability for the demanding and dynamic field of Ethical Hacking.
Question 11: Describe a challenging Ethical Hacking project you have worked on
In a recent Ethical Hacking project, I assessed the security of a financial institution's online banking system. The challenge was to identify vulnerabilities that could compromise customer data. I discovered a critical vulnerability in the login mechanism through thorough analysis and penetration testing. I reported my findings and provided detailed recommendations for remediation.
Question 12: How do you handle disagreements or conflicts with team members during an assignment?
I believe in open communication and collaboration to resolve conflicts. I actively listen to team members, express my thoughts, and seek common ground or alternative solutions. Maintaining professionalism and respect are crucial during discussions to reach a resolution and focus on project objectives.
Question 13: Explain how you would respond to a suspected security breach
When faced with a suspected security breach, immediate and well-coordinated action is vital. Upon detecting a suspected breach, I would isolate the affected system, investigate the breach's scope and entry point, and collaborate with the incident response team. Mitigation measures such as patching vulnerabilities, changing access credentials, and enhancing security controls would be implemented. Transparent communication with stakeholders and long-term preventive measures are also essential.
Question 14: Share an example of when you had to prioritise multiple tasks with tight deadlines
I managed multiple tasks during a data encryption project by assessing the urgency of data to be protected. I achieved this by creating a detailed schedule and delegating responsibilities to cybersecurity architects to ensure efficient workload distribution. Adaptability and flexibility were crucial to adjust priorities based on new information or challenges regarding the encryption project, ultimately meeting the deadlines successfully.
Question 15: How do you maintain ethical standards while performing hacking activities?
I operate within legal frameworks with proper authorisation and consent to maintain ethical standards. I define the scope of hacking engagements and handle sensitive information confidentially. Responsible disclosure practices are followed, promptly reporting vulnerabilities and refraining from exploiting them for personal gain. Continuous learning and professional development keep me updated with Ethical Hacking techniques and requirements, aligning my skills with industry best practices.
Technical questions and practical demonstrations
In Ethical Hacking, technical knowledge and practical skills are fundamental for success. Ethical Hackers are expected to understand various hacking techniques, vulnerabilities, and defensive strategies. Interviews often include a segment dedicated to technical questions and practical demonstrations to assess a candidate's proficiency in these areas.
This segment evaluates candidates' ability to apply their knowledge in real-world scenarios and demonstrate their practical problem-solving skills. It provides an opportunity for you to showcase your expertise in conducting vulnerability assessments, understanding network protocols, performing security attacks, and assessing wireless network security, among other technical aspects, during the interview.
Question 16: Walk us through the process of conducting a vulnerability assessment
The process of conducting a vulnerability assessment involves several steps. Firstly, I would gather information about the target system or network, such as IP addresses, domain names, and network infrastructure. Next, I would perform a vulnerability scan using automated tools to identify common vulnerabilities, misconfigurations, and weaknesses.
Once vulnerabilities are identified, I would prioritise them based on severity and potential impact. Afterwards, I would conduct manual testing to validate and verify the vulnerabilities. Finally, I would document the findings, provide recommendations for remediation, and assist in implementing security measures to address the identified vulnerabilities.
Question 17: Demonstrate your knowledge of network protocols and their vulnerabilities
Network protocols form the backbone of communication between devices. Some common protocols, such as TCP/IP, HTTP, FTP, and DNS, have known vulnerabilities. For example, TCP/IP is vulnerable to IP spoofing and SYN flood attacks. HTTP can be exploited through injection attacks, while FTP can be susceptible to brute-force attacks.
DNS can be vulnerable to DNS spoofing or cache poisoning. It is crucial to understand these vulnerabilities to assess and secure network infrastructure effectively. The risks associated with these vulnerabilities can be mitigated by applying appropriate security controls, such as encryption, access control, and regular patching.
Learn about information security with CISM Certified Information Security Manager Course!
Question 18: Perform a basic SQL injection attack on a test environment
It is recommended to address this interview question by stating the illegal nature of SQL injection. SQL injection is a web application vulnerability where an attacker manipulates user-supplied input to execute malicious SQL queries. This can lead to unauthorised access, data leakage, or database manipulation. Attackers can exploit poorly designed or unvalidated input fields to inject SQL commands.
To mitigate SQL injection, input validation and parameterised queries should be implemented. Input validation ensures that user input is sanitised and adheres to expected formats. Parameterised queries separate user input from the SQL query itself, preventing the execution of malicious code.
Question 19: Explain the concept of Cross-Site Scripting (XSS) and how it can be mitigated
XSS is a type of vulnerability in web applications where attackers inject malicious scripts into web pages viewed by other users. This occurs when user input is not properly validated or sanitised and is rendered on the web page without appropriate encoding. XSS attacks can lead to session hijacking, cookie theft, defacement, or malware distribution.
To mitigate XSS, input validation and output encoding should be implemented. Input validation ensures that user-supplied data is free from malicious scripts. Output encoding ensures that data rendered on web pages are properly encoded, preventing the execution of injected scripts.
Question 20: Conduct a wireless network sniffing demonstration
It is recommended to address this interview question by stating the illegal nature of network sniffing. Wireless network sniffing involves capturing and analysing data packets transmitted over a wireless network. This technique allows attackers to intercept and inspect network traffic, potentially revealing sensitive information such as passwords, emails, or financial data. Sniffing can be performed using tools like Wireshark or tcpdump, which capture packets in promiscuous mode.
Encryption protocols like WPA2 or WPA3 should be implemented to mitigate wireless sniffing attacks, ensuring that network traffic is encrypted and not easily readable by attackers. MAC address filtering and disabling unnecessary wireless protocols are strong access control measures that can help enhance network security.

Conclusion
In conclusion, conducting an Ethical Hacker Interview allows organisations to evaluate candidates' cybersecurity skills, knowledge, and ethical standards. Employers can assess a candidate's problem-solving abilities, teamwork skills, and understanding of vulnerabilities and mitigation techniques through behavioural and technical questions. Hiring qualified, Ethical Hackers is crucial for maintaining robust cybersecurity defences in today's digital landscape.
Become certified in cyber security with our CISSP Certification Course today!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Ethical Hacking Professional
Ethical Hacking Professional
Thu 6th Jun 2024
Thu 26th Sep 2024
Thu 19th Dec 2024
Thu 2nd Jan 2025
Thu 1st May 2025
Thu 4th Sep 2025
Thu 20th Nov 2025







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


