We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

The Cyber Security industry was valued at about £8 billion in 2021, with a CAGR of nearly 40% over the previous two years. Growing digital usage is leading to more online threats and the industry is expected to gain more than £11 billion by 2023.
Cyber threats are rising significantly, so cybersecurity awareness is essential for keeping your workforce and organisation secure online.
Cyber Security threats are common and need to be addressed, ranging from ransomware and phishing to identity fraud and data breaches. Furthermore, as humans are the weakest link in information security, firms need to establish a data protection culture. As, it will ensure that workers understand the types of risks that are frequent and the impact they may have on the organisation as a whole. This is where security awareness consulting can help by educating employees about potential dangers, implementing adequate cybersecurity practices, and training staff on what to do (and who to notify) in the case of a security threat.
Table of Contents
1) What is Cyber Security Awareness definition?
2) Why is Cyber Security Awareness Important?
3) List of some Common Cyber Attacks
4) What are the best practices for Cyber Security?
5) Conclusion
Learn the fundamentals of Cyber Security. Sign up for our cybersecurity awareness course now!
What is Cyber Security Awareness definition?
Cyber Security Awareness is the combination of understanding and taking action to protect a company's information assets. When an enterprise's employees are aware of Cyber Security, it implies they understand what cyber threats are, the possible impact a cyber-attack will have on their firm, and the actions needed to decrease risk and prevent cybercrime from penetrating their online workplace.
Creating a culture in the workplace does not mean that the risk of data theft or cybercrime to the firm is fully eliminated. Malware has evolved, becoming more complex with each new strand developed, and we expect that cyber threats and malware will continue to evolve and spread.
Every day in 2010, 123 new malware strains were discovered. Ten thousand of those threats were new strains of malware throughout that year. Eleven years later, research revealed that per second, four new strains of malicious malware were detected in Q3 of 2021. It's important to note that these were the strains discovered and identified by Cyber Security organisations.
As new types of malwares emerge, companies need to ensure that they are installing adequate security measures, training their employees, and eradicating any vulnerabilities that make them vulnerable to an attack. Human mistake is an exploit that can result in heavy penalties and severe business damage.
Learn the fundamentals of Cyber Security. Sign up for our Cyber Security professional course now!
Why is Cyber Security Awareness Important?
Despite having best-in-class protection systems and policies, many firms still endure security breaches. Unfortunately, many data breaches have been caused by human mistakes. According to Verizon's 2022 Data Breach Investigations Report, more than 80% of breaches featured the human element, including social engineering assaults, errors, and the misuse of stolen credentials. Threat actors seek to exploit this gap in order to get access to an organisation's networks and systems. This is where cybersecurity awareness comes into play.
Cyber Security Awareness educates your employees about the malicious tactics employed by cybercriminals, how they can be easy targets, how to identify possible threats, and what they can do to prevent being victims of these devious attacks. It provides your employees with the information and resources they need to detect and flag possible hazards before they cause any damage.
List of some Common Cyber Attacks
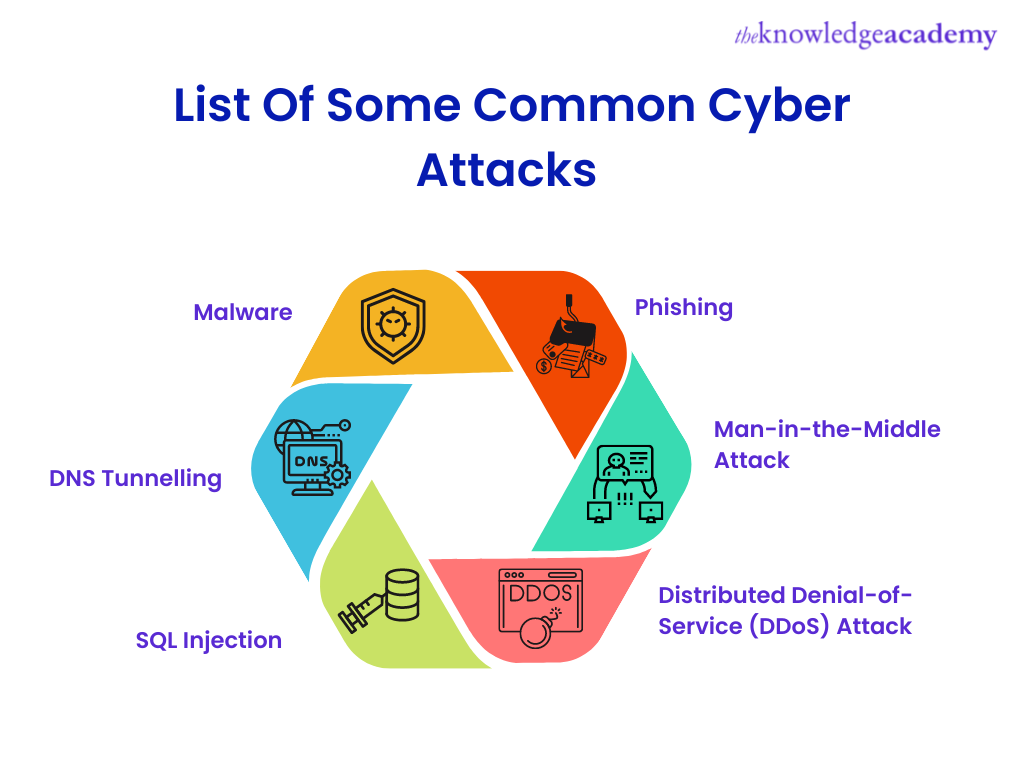
While an attacker can access an IT system in various ways, most cyber-attacks use quite similar approaches. Some of the most popular types of cyber-attacks are as follows:
Malware
Malware is a type of programme that can perform several destructive functions. Some malware strains are meant to get persistent network access, while some are designed to spy on the user in order to steal passwords or other important data. Ransomware is the most well-known type of malware. The software encrypts the victim's files and then demands a ransom payment to obtain the decryption key.
How to prevent a Malware attack?
Preventing malware attack is a difficult endeavour that requires a multi-pronged strategy. At least, you must:
a) Ensure that you have the latest anti-malware protection software installed
b) Ensure that employees are trained to identify fraudulent emails and websites
c) Use a strong password policy with multi-factor authentication
d) Keep all software up-to-date
e) Control access to systems and closely adhere to the least-privilege concept
Phishing
A phishing attack occurs when an attacker tries to mislead an unsuspecting target into revealing sensitive information such as passwords, credit card information, intellectual property, etc. Phishing attacks are frequently sent in the form of an email pretending to be from a legitimate institution, such as your bank, the tax department, or another reliable source. Phishing is the most common type of cyber-attack due to its ease of execution and unexpected efficiency.
How to prevent a Phishing attack?
The techniques used to avoid phishing attacks are quite similar to preventing malware attacks. However, phishing attempts are mostly the result of a lack of attention. Security awareness training is the most effective strategy to avoid them. Employees should be adequately trained to recognise suspicious emails, links, and websites and refuse to enter information or download files from sites they do not trust. It is also a good idea to install any add-ons that can assist you in identifying malicious websites.
Man-in-the-Middle attack (MITM)
A Man-in-the-Middle (MITM) attack occurs when an attacker intercepts communication between parties in order to spy on the victims, steal personal information or passwords, or alter the conversation. MITM attacks are less prevalent since most email and chat services utilise end-to-end encryption, prohibiting third-parties from manipulating data carried across a network.
How to prevent a Man-in-the-Middle attack?
If the communication protocols you employ do not support end-to-end encryption, consider connecting to your network over a VPN (Virtual Private Network), especially if you are accessing from a public Wi-Fi hotspot. Be careful of fraudulent websites, obtrusive pop-ups, outdated certificates, and search for "HTTPS" at the beginning of each URL.
Distributed Denial-of-Service (DDoS) attack
A DDoS attack occurs when an attacker floods a target server with traffic to disrupt and, perhaps, bring down the target. However, unlike typical Denial-of-Service attacks, which most competent firewalls can easily detect and respond to, a DDoS attack can use numerous hacked devices to flood the target with traffic.
How to prevent a DDoS attack?
DDoS attacks are difficult to prevent because there are few warning indications to look for and few ways to halt the attack once it has begun. However, employing a next-generation Firewall or Intrusion Prevention System (IPS) provide you with real-time insight into any traffic abnormalities, network performance difficulties, intermittent web failures, etc.
It's also a good idea to put your servers in separate data centres so that you can move to another server if the current one fails. The best way to defend your network against DDoS attacks is to have a proven and established response strategy. As it will allow you to bring your systems back online soon and maintain business operations.
SQL Injection
SQL injection is a type of SQL database attack. SQL databases query data using SQL statements, commonly executed via an HTML form on a webpage. If the database permissions are not correctly specified, the attacker can use the HTML form to perform queries that create, read, edit, or remove data from the database.
How to prevent a SQL Injection attack?
The only way to avoid SQL injection attacks is to ensure that the web developers have properly sanitised all inputs. In other words, data cannot be stored directly in a database from an input box, such as a password field. The entered password must be checked to ensure that it meets predefined requirements.
DNS Tunnelling
DNS tunnelling is a complex attack vector that allows attackers to access a specific target permanently. Attackers can introduce or "tunnel" malware into DNS queries since many businesses fail to monitor DNS traffic for malicious activities (DNS requests sent from the client to the server). The malware is used to establish a persistent communication channel that is undetectable by most firewalls.
How to prevent a DNS Tunnelling attack?
As traditional firewalls and antivirus software cannot identify DNS tunnelling, you will likely need to invest in specialised tools such as TunnelGuard, Zscaler, and DNSFilter. You should ensure that the technologies you employ can automatically prevent the execution of malware contained in malicious DNS requests. It should ban known data exfiltration locations and perform real-time analysis of all DNS requests for suspicious patterns.
Learn the fundamentals of Cyber Security. Sign up for our Cyber Security Training now!
What are the best practices for Cyber Security?

Here are some easy steps you can take to boost security and reduce the risk of cybercrime at your organisation:
Educate staff
In 2019, 90% of data breaches were caused by human error. However, this troubling figure offers a silver lining. The majority of data breach instances could be avoided if employees were educated on how to recognise and respond to cyber threats. Such educational initiatives could also increase the value of all cyber security solution investments by preventing employees from unknowingly bypassing expensive security safeguards to facilitate cybercrime.
Protect your sensitive data
Invest in tools that prevent information loss, monitor third-party and fourth-party vendor risk, and scan for data exposure and leaked credentials on a regular basis. If left untreated, data leaks can assist attackers in gaining access to corporate networks and breaching key resources. It is essential to develop a data leak detection solution that can also monitor leaks throughout the third-party network.
Almost 60% of data breaches are caused by compromised third-party suppliers; therefore, the vast majority of data breach instances can be averted by preventing vendor data leaks.
Implement a Third-Party Risk Management
Use technology to decrease expenses, such as automatically sending vendor evaluation questionnaires.
Companies should no longer question why cybersecurity is necessary but should ensure that organisations' cybersecurity procedures are enough to comply with GDPR and other legislation and safeguard firms from sophisticated cyber assaults.
Learn the fundamentals of Cyber Security. Sign up for our Cyber Security Risk Management now!
Conclusion
In this era, the use of the internet and reliance on digital technology will skyrocket. Thus, being aware of various cyber threats and their avoidance is the best way to protect yourself from hackers' malicious activities.
Every year, cyber security month is celebrated to raise public awareness about various sorts of attacks and the strategies people can employ to avoid becoming victims of such attacks.
Cyber Security programmes educate people on various types of risks and how they can protect themselves from such attacks.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Cyber Security Awareness
Cyber Security Awareness
Fri 16th Aug 2024
Fri 29th Nov 2024







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


