We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

In today’s digital landscape, the significance of secure online communication is consistently rising. Businesses prefer to invest in tools that enable safe and hassle-free remote communication and collaboration. Among the plethora of options available, Zoom and Microsoft Teams have emerged as the two leading contenders when it comes to ensuring privacy on the platforms. The Zoom vs Microsoft Teams Security debate has been prevalent for a while. Thus, if you are looking to choose between the two platforms, then it is essential to understand the security measures implemented by them.
The COVID-19 pandemic has improved the adoption of remote work and virtual meetings, making it imperative for organisations and individuals to choose a video conferencing platform that prioritises security. According to Statista, the global market for video conferencing was worth £8.43 billion in 2022 and is expected to double in 2027.
In this blog, we'll compare Zoom and Microsoft Teams Security characteristics, including their user interfaces, security, and other aspects.
Table of Contents
1) Security features of Zoom
2) Security features of Microsoft Teams
3) Zoom vs Microsoft Teams Security: Comparing features
4) Zoom or Microsoft Teams: Which one should you use?
5) Conclusion
Security features of Zoom
Zoom offers effective security measures which aim to protect sensitive data, prevent unauthorised access, and maintain the privacy of individuals using the platform. Here are some of the major security features of Zoom:
1) Encryption
One of the fundamental security features offered by Zoom is encryption. Encryption ensures that the data transmitted during meetings and video conferences are protected from unauthorised access. Zoom employs end-to-end encryption, which means that the encryption of data occurs on the sender's device and can only be decrypted by the intended recipients. This feature of strong encryption protocol in Zoom ensures the confidentiality and integrity of the communication, minimising the risk of eavesdropping or data breaches.
2) Meeting access controls
Zoom provides various meeting access controls to prevent unauthorised individuals from joining your meetings. One of the primary access control features is password protection. With password protection enabled, participants must enter a unique password to join the meeting, adding an additional layer of security. Hosts in Zoom also have the option to generate random meeting IDs, making it more challenging for malicious actors to guess or join meetings uninvited.
3) User authentication
Zoom offers multiple user authentication options to ensure the authenticity of meeting participants. Single Sign-On (SSO) integration allows users to authenticate using their existing organisational credentials, enhancing security in Zoom by eliminating the need for separate login credentials.
Additionally, Zoom supports two-factor authentication, requiring users to provide a secondary verification code along with their password. This feature serves as an extra layer of protection against unauthorised access.
4) Waiting Rooms
Waiting rooms are another valuable security feature offered by Zoom. When enabled, participants are placed in a virtual waiting area before being admitted to the meeting. Hosts can review and admit participants individually, providing an opportunity to verify their identities and ensure that only intended attendees are granted access. Waiting rooms help prevent uninvited guests from joining meetings, protecting the integrity and privacy of the communication.
5) Security and Privacy Settings
Zoom provides a range of customisable security and privacy settings, allowing hosts to tailor their meeting experience to their specific requirements. These settings include options such as screen sharing restrictions, disabling private chat, and controlling participant access. Hosts can limit certain functionalities to mitigate the risk of unauthorised activities during meetings, ensuring a secure and focused environment for collaboration.
Enhance your security expertise with our Microsoft Security Engineer Training Courses today!
Security features of Microsoft Teams
Microsoft Teams offers a range of security features that focus on protecting communication, preventing data loss, and maintaining compliance. Let’s explore some of its security features in detail:
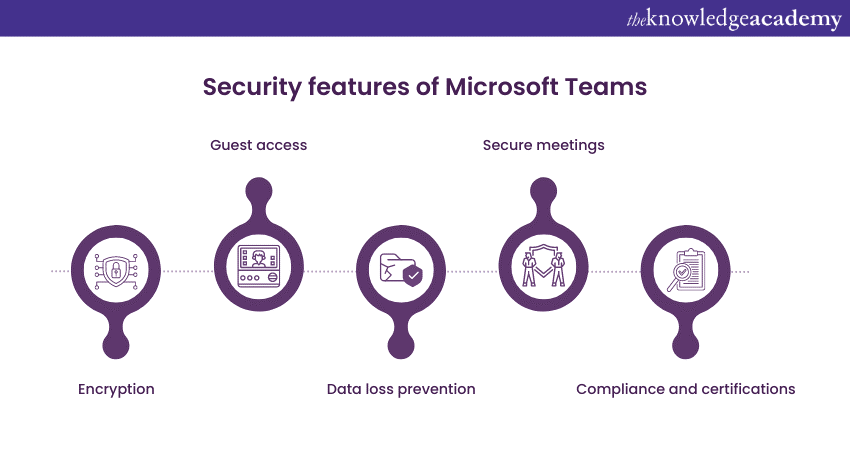
1) Encryption
Microsoft Teams prioritises the security of communication by employing encryption mechanisms. Similar to Zoom, Microsoft Teams utilises end-to-end encryption, which ensures that data transmitted during meetings and chats remains secure and inaccessible to unauthorised individuals to protect sensitive information.
2) Guest access
Teams offers a guest access feature, allowing users to collaborate with external parties securely. Hosts have control over the level of access granted to guests, ensuring that confidential information and internal resources are protected. This feature enables organisations to collaborate seamlessly with clients, partners, or contractors while maintaining a secure environment.
3) Data loss prevention
Teams incorporates Data Loss Prevention (DLP) policies to prevent accidental data leakage. These policies monitor and prevent the sharing of sensitive information, such as confidential documents or Personally Identifiable Information (PII). By implementing DLP measures, Microsoft Teams helps organisations maintain compliance, protect intellectual property, and reduce the risk of data breaches.
4) Secure meetings
Teams prioritises the security of meetings and calls by implementing various features. Secure join enables hosts to control who can join their meetings, ensuring that only authorised participants can access the communication. Meeting lobbies allow hosts to admit participants individually, providing an additional layer of verification before granting access. Furthermore, hosts can manage participant permissions, restrict screen sharing, and control other aspects of the meeting to maintain a secure and controlled environment.
Teams is designed with compliance in mind. It adheres to industry-standard security and privacy frameworks, including ISO 27001, SOC 2, and HIPAA. These certifications demonstrate Microsoft's commitment to maintaining robust security measures and compliance with regulatory requirements. By choosing Microsoft Teams, organisations can be confident in the platform's adherence to security best practices.

Zoom vs Microsoft Teams Security: Comparing features
This table provides a comparison of key security features between Zoom and Microsoft Teams:
|
Security feature |
Zoom |
Microsoft Teams |
|
Encryption |
End-to-end encryption |
End-to-end encryption |
|
Meeting access controls |
Password protection, randomised meeting IDs |
Secure join, meeting lobbies |
|
User authentication |
Single Sign-On (SSO), two-factor authentication |
Single Sign-On (SSO), multi-factor authentication |
|
Waiting rooms |
Available |
Not available |
|
Security and privacy settings |
Customisable settings for screen sharing, private chat, and participant access |
Customisable settings for meeting access and permissions |
|
Guest access |
Limited functionality for external participants |
Collaborate securely with external parties |
|
Data loss prevention |
Not specified |
Data loss prevention policies in place |
|
Compliance and certifications |
Not specified |
ISO 27001, SOC 2, HIPAA compliance |
Both Zoom and Teams prioritise encryption, offering end-to-end encryption to protect communication. In terms of meeting access controls, Zoom provides password protection and randomised meeting IDs, while Teams offers secure join and meeting lobbies for participant verification.
User authentication is supported by both platforms, with Zoom supporting SSO and two-factor authentication and Teams supporting SSO and multi-factor authentication. Zoom offers waiting rooms for additional security, whereas Teams does not have this feature.
Both Zoom and Microsoft Teams provide customisable security and privacy settings, allowing hosts to tailor the meeting experience. Teams allows guest access with limited functionality, while Zoom does not specify guest access capabilities.
Teams emphasises data loss prevention, whereas Zoom does not explicitly mention this feature. Teams holds compliance certifications such as ISO 27001, SOC 2, and HIPAA, while Zoom's compliance certifications are not specified.
Master the skills to design and implement robust security solutions by signing up for our Microsoft Cybersecurity Architect SC100 Course now!
Zoom or Microsoft Teams: Which one should you use?
When deciding between Zoom and Teams by Microsoft for your video conferencing and collaboration needs, it is essential to consider several factors that can influence your decision. Here are some key factors to consider:
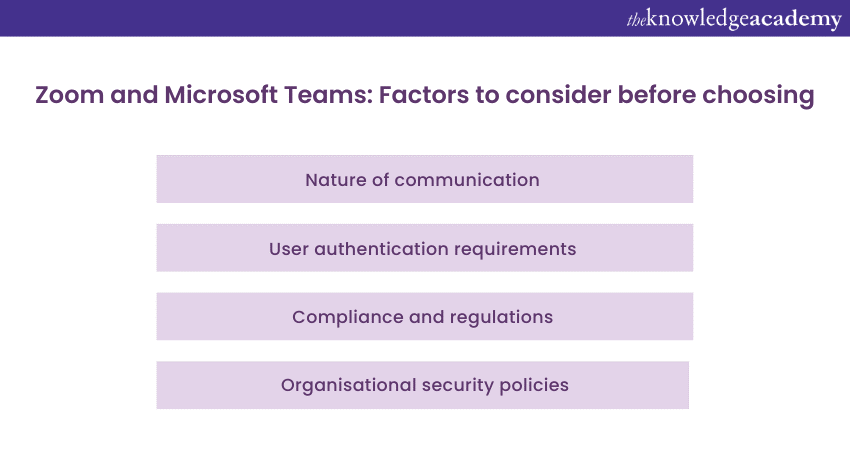
1) Nature of communication
Before choosing a video conferencing platform, you must determine the specific requirements of your communication needs. Do you primarily conduct internal team meetings or frequently collaborate with external clients and partners?
Teams may be more suitable when compared to Zoom, if you require seamless collaboration within your organisation, as it offers integration with other Microsoft tools like Outlook and SharePoint. On the other hand, if you frequently interact with external parties and prioritise ease of use, Zoom's guest access feature and user-friendly interface might be more beneficial.
2) User authentication requirements
Evaluate the level of user authentication required for your meetings and conferences. Both Zoom and Microsoft Teams offer authentication options such as Single Sign-On (SSO) integration and multi-factor authentication (MFA).
Consider the importance of user authentication in your organisation's security policies and compliance requirements. If robust user authentication is a priority, both Zoom and Teams provide suitable options, but it is worth examining the specific authentication methods supported by each.
3) Compliance and regulations
Compliance certifications and adherence to regulations become crucial if your organisation operates in an industry with specific compliance requirements, such as healthcare (HIPAA) or finance (PCI DSS).
Microsoft Teams holds certifications like ISO 27001, SOC 2, and HIPAA compliance, demonstrating its commitment to meeting stringent security and privacy standards. Verify whether the platform aligns with the compliance requirements relevant to your organisation.
4) Organisational security policies
Consider your organisation's security policies and evaluate how well each platform aligns with them. Examine the security features, encryption protocols, access controls, and data protection capabilities offered by Zoom and Microsoft Teams. Determine which platform provides the necessary security measures to safeguard your organisation's sensitive information and ensure secure communication.
Conclusion
In conclusion, when comparing Zoom and Microsoft Teams in terms of security features and considerations, both platforms offer robust security measures to protect communication and data.
Zoom excels in areas such as end-to-end encryption and customisable security settings, while Microsoft Teams integrates seamlessly with other Microsoft tools and provides guest access capabilities. We hope this blog - Zoom vs Microsoft Teams Security: Features Comparison - has aided in improving your knowledge of the security features of two significant platforms.
Learn how to proactively detect and respond to security incidents – Register for our Microsoft Security Operations Analyst SC200 Course now!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Microsoft Cybersecurity Architect SC100
Microsoft Cybersecurity Architect SC100
Mon 13th May 2024
Mon 22nd Jul 2024
Mon 23rd Sep 2024
Mon 25th Nov 2024







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


