We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

The discontinuation of the Microsoft Baseline Security Analyzer (MBSA) marks a significant turn in cybersecurity tools. Known for its robust assessment of Windows security, MBSA's absence has sparked a demand for alternatives. This need underlines the ever-changing landscape of digital threats and IT complexities. As a result, the search for a Microsoft Baseline Security Analyzer alternative is not just necessary but critical in modern cybersecurity strategies.
Turning to an alternative to the Microsoft Baseline Security Analyzer is more than finding a substitute. It's about advancing security practices in a digital era rife with evolving threats. This blog explores the top Microsoft Baseline Security Analyzer Alternatives, highlighting their features and benefits. Our focus is on aligning with the current cybersecurity needs, offering a comprehensive view of how these tools safeguard digital assets in a post-MBSA world.
Table of Contents
1) The evolution of Security Analyzers post-MBSA
2) Criteria for evaluating modern Security Analyzers
3) Alternative 1 – SolarWinds Network Automation Manager
4) Alternative 2 – ManageEngine Vulnerability Manager Plus
5) Alternative 3 – Paessler PRTG Network Monitor
6) Alternative 4 – OpenVAS
7) Alternative 5 – Nessus
8) Alternative 6 – Nexpose
9) Alternative 7 – Intruder
10) Conclusion
The evolution of Security Analyzers post-MBSA
The Microsoft Baseline Security Analyzer (MBSA) once stood as a foundational tool in the cybersecurity arsenal, particularly for Windows-based systems. It was lauded for its ability to scan for missing updates and less secure settings, a critical function in maintaining system integrity. However, as the digital landscape evolved, so too did the nature of cyber threats, rendering tools like MBSA less effective against modern challenges. The discontinuation of MBSA, thus, marked a pivotal moment, prompting the need for more advanced Security Analyzers.
Adapting to modern threats
In the post-MBSA era, Security Analyzers have had to adapt rapidly. Modern cybersecurity tools now face a broader spectrum of threats, from sophisticated malware to intricate network breaches. This evolution has driven the development of analyzers that are not only more comprehensive in their scanning capabilities but also more proactive in their approach to threat detection and prevention. Today's tools are designed to anticipate and counteract a diverse range of vulnerabilities, ensuring robust defence mechanisms for IT infrastructures.
The transition to newer Security Analyzers also reflects a shift in IT environments themselves. With the advent of cloud computing, mobile technology, and the Internet of Things (IoT), the perimeter of what needs to be secured has expanded exponentially. Modern alternatives to MBSA are built to navigate this complex terrain, offering features like cloud security assessments, IoT device scanning, and mobile application analysis. They provide a holistic view of an organisation's security posture, a necessity in a world where digital assets are increasingly dispersed and interconnected.
The evolution of Security Analyzers in the wake of MBSA's discontinuation is a response to a more dynamic and sophisticated digital world. These tools have grown not only in their technical capabilities but also in their strategic importance. As the frontline in the battle against cyber threats, modern Security Analyzers are indispensable in safeguarding information and maintaining the integrity of IT systems in a rapidly changing digital environment.
Criteria for evaluating modern Security Analyzers
Selecting the right Security Analyzer in today's complex digital environment is critical. It requires a thorough understanding of various factors that contribute to the effectiveness and efficiency of the tool.
Understanding the core features
a) Comprehensive scanning abilities: Modern Security Analyzers must offer in-depth scanning capabilities that go beyond basic vulnerability checks. They should effectively identify a wide range of threats, from traditional malware to sophisticated cyber-attacks.
b) Real-time monitoring and response: The ability to monitor networks and systems in real-time is crucial. This feature enables immediate detection and response to threats, minimising potential damage.
c) Compatibility and integration: Tools should seamlessly integrate with various operating systems and IT environments. Compatibility with the latest technologies, including cloud services and IoT devices, is essential.
Assessing user experience and management
a) Ease of use and accessibility: An intuitive user interface and straightforward management are key for efficient operation. Tools that require minimal training are preferable, especially in diverse IT teams.
b) Customisation and scalability: The capability to tailor security settings and scale according to organisational needs is vital. This flexibility ensures that the tool remains effective as the company grows and evolves.
Evaluating additional considerations
a) Cost-effectiveness: Analyzers should offer a good balance between features and cost. Budget-friendly options are important for small to medium-sized businesses.
b) Compliance and reporting: The tool should aid in maintaining compliance with various regulatory standards. Detailed reporting capabilities are necessary for auditing and assessing security posture.
c) Community and vendor support: Strong support from the vendor, along with an active user community, can be invaluable. This support ensures timely updates and assistance in addressing security concerns.
Evaluating modern Security Analyzers involves a comprehensive look at their features, user experience, and additional factors that impact their effectiveness. By considering these criteria, organisations can select a tool that not only replaces MBSA but also enhances their overall cybersecurity strategy in the current digital landscape.
Elevate your cybersecurity expertise with the Microsoft Cybersecurity Architect SC100 Course.
Alternative 1 – SolarWinds Network Automation Manager
SolarWinds Network Automation Manager stands out as a prominent Microsoft Baseline Security Analyzer alternative, especially for Windows Server environments. Designed to cater to the needs of network administrators and IT professionals, this toolset offers a blend of advanced features that align well with the demands of modern network security.
Key features and advantages
a) Comprehensive protection and monitoring: One of the core strengths of SolarWinds Network Automation Manager is its robust protection capabilities. It provides extensive monitoring of devices and networks, ensuring that any potential threats are identified and addressed promptly.
b) Automated activity tracking: A significant feature of this tool is its ability to automate activity tracking. This functionality is crucial for identifying unusual patterns or potential security breaches, enabling a proactive approach to network security.
c) User-friendly interface: Despite its comprehensive capabilities, the tool boasts a user-friendly interface. This design makes it accessible for IT teams of various skill levels, reducing the learning curve and enhancing efficiency in managing network security.
Secure your career with the Microsoft Security Engineer Training. Register now and become a certified Security Operations Analyst!
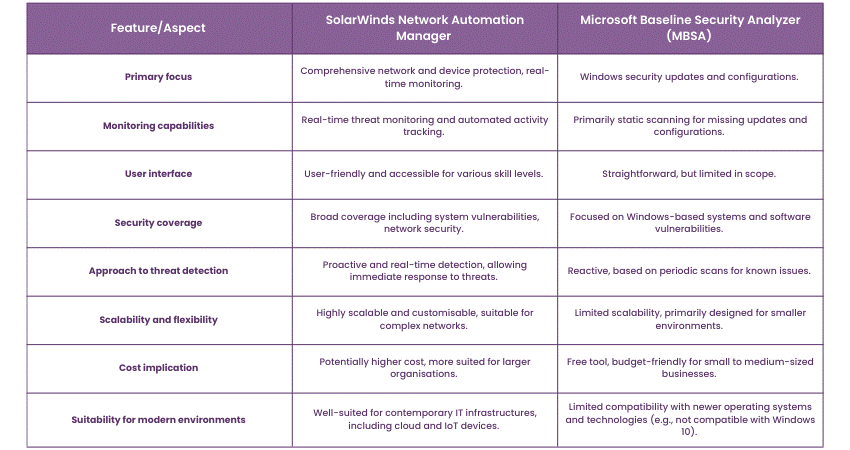
SolarWinds Network Automation Manager vs MBSA
Here's a table comparing SolarWinds Network Automation Manager with the Microsoft Baseline Security Analyzer (MBSA):
Limitations and considerations
1) While SolarWinds Network Automation Manager offers a comprehensive suite of tools, it may be more complex and resource-intensive than some smaller organisations require.
2) The cost factor also plays a role, as this solution might be on the higher end of the spectrum, potentially making it less accessible for smaller businesses with limited budgets.
SolarWinds Network Automation Manager emerges as a robust and versatile alternative to MBSA, especially suited for larger organisations or those with complex network infrastructures. Its emphasis on real-time monitoring, automation, and a user-friendly interface makes it a strong contender for those looking to upgrade their cybersecurity toolkit in a post-MBSA world.
Discover advanced cybersecurity techniques with the Microsoft Security Operations Analyst SC-200 course – start your journey today!
Alternative 2 – ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus emerges as a formidable alternative to the Microsoft Baseline Security Analyzer, especially for organisations seeking a comprehensive solution for vulnerability scanning and patch management. It is designed to address a wide range of security challenges, making it suitable for modern, complex IT environments.
Key features and advantages
a) Integrated vulnerability scanning and patch management: This tool excels in providing an integrated approach to vulnerability scanning, coupled with efficient patch management. This integration streamlines the process of not only identifying vulnerabilities but also promptly addressing them.
b) System hardening and compliance: Apart from vulnerability management, it offers system hardening guides, which are essential for strengthening the overall security posture. The tool also aids in ensuring compliance with various cybersecurity standards, a critical aspect for many organisations.
c) User-friendly and scalable: ManageEngine Vulnerability Manager Plus is known for its user-friendly interface, simplifying complex processes and making them accessible to a wider range of users. Its scalability ensures it can adapt to the growing needs of an organisation, regardless of its size.
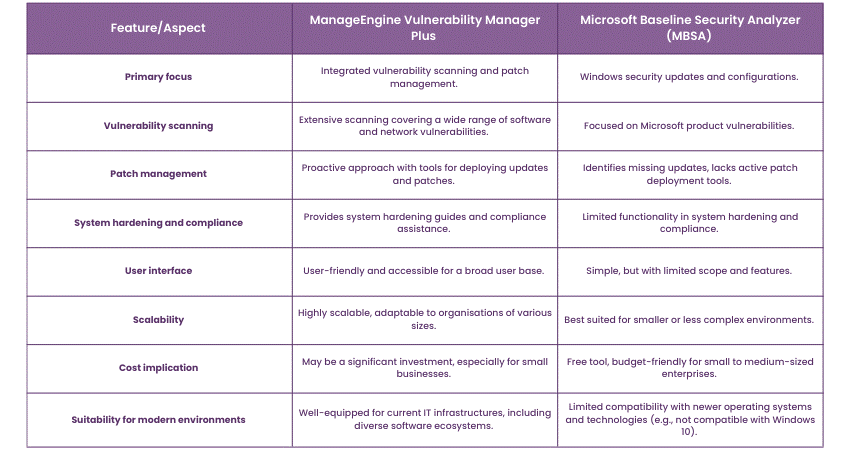
ManageEngine Vulnerability Manager Plus vs MBSA
Here's a comparative table highlighting the key differences between ManageEngine Vulnerability Manager Plus and the Microsoft Baseline Security Analyzer (MBSA):
Limitations and considerations
1) Resource requirements: For smaller organisations, the comprehensive nature of ManageEngine Vulnerability Manager Plus might translate to a need for more resources in terms of implementation and management.
2) Cost considerations: As a more feature-rich solution, it may come with a higher price tag compared to more basic tools, making it a significant investment, particularly for smaller businesses.
ManageEngine Vulnerability Manager Plus stands out as a robust Microsoft Baseline Security Analyzer alternative, offering an integrated, comprehensive approach to vulnerability management. Its blend of user-friendliness, scalability, and extensive security features makes it an attractive option for organisations seeking to enhance their cybersecurity infrastructure in a post-MBSA world.
Boost your expertise in identity and access management with the Microsoft Identity and Access Administrator SC-300 course – begin your learning path now!
Alternative 3 – Paessler PRTG Network Monitor
Paessler PRTG Network Monitor is another notable Microsoft Baseline Security Analyzer alternative, catering to a diverse range of monitoring needs. It stands out for its comprehensive network, server, and application monitoring tools, which include features for system security scanning. This versatility makes it a valuable asset for organisations looking to maintain a strong security posture.
Key features and advantages
1) Versatile monitoring capabilities: PRTG excels in its ability to monitor various aspects of IT infrastructure, including network traffic, server performance, and application status. This wide-ranging monitoring is crucial for identifying potential security issues.
2) Real-time system scanning: A significant advantage of PRTG is its real-time system scanning functionality. It can detect intruders and vulnerabilities as they occur, providing an immediate response mechanism.
3) Customisable sensor-based system: The tool employs a sensor-based system that allows users to customise what they monitor, depending on their specific needs. This flexibility ensures that resources are efficiently utilised, focusing on the most critical aspects of the network.
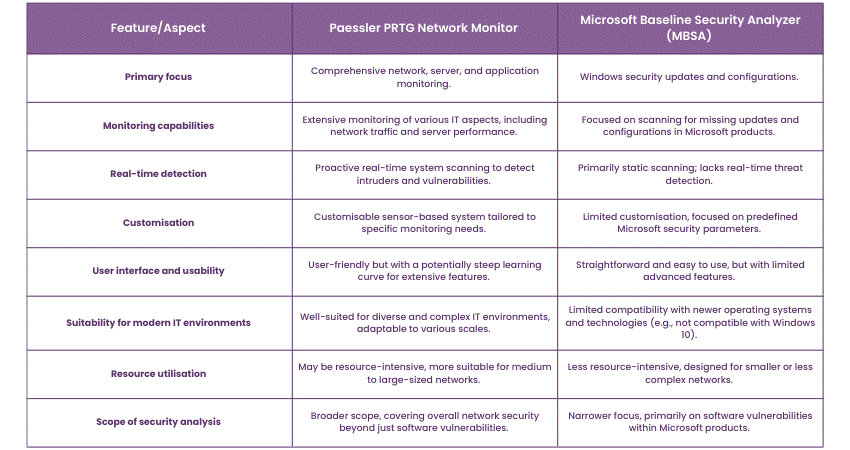
Paessler PRTG Network Monitor vs MBSA
Here's a comparative table for Paessler PRTG Network Monitor and the Microsoft Baseline Security Analyzer (MBSA):
Limitations and considerations
1) Learning curve: The extensive features of PRTG may present a steeper learning curve, especially for users not familiar with comprehensive monitoring tools.
2) Resource intensiveness: For smaller networks or organisations with limited IT resources, PRTG’s extensive monitoring capabilities might be more than necessary, potentially leading to underutilisation of the tool.
Paessler PRTG Network Monitor offers a multifaceted approach to network monitoring and security, making it a strong contender as an alternative to the Microsoft Baseline Security Analyzer. Its ability to provide real-time scanning and a customisable monitoring experience positions it as a versatile tool suitable for a wide range of organisational needs in a modern cybersecurity environment.
Dive into the world of information protection with the Microsoft Information Protection Administrator SC-400 course – take the first step in mastering data security today!
Alternative 4 – OpenVAS
OpenVAS stands out as a powerful open-source Microsoft Baseline Security Analyzer alternative. It's particularly renowned for its comprehensive vulnerability scanning capabilities. As a free tool, OpenVAS offers an accessible solution for organisations of all sizes, making it a popular choice in the cybersecurity community.
Key features and advantages
1) Extensive vulnerability scanning: OpenVAS excels in its wide-ranging vulnerability scanning abilities. It effectively identifies a broad spectrum of security threats and weaknesses across various systems and networks.
2) Open-source community support: Being open-source, OpenVAS benefits from a large, active community. This ensures continuous updates and improvements to the tool, driven by collective expertise and real-world feedback.
3) Customisable scanning options: Users can customise scans according to specific requirements. This flexibility allows for targeted security assessments, ensuring resources are focused on the most relevant areas.
OpenVAS vs MBSA
Here's a comparative table for OpenVAS and the Microsoft Baseline Security Analyzer (MBSA):
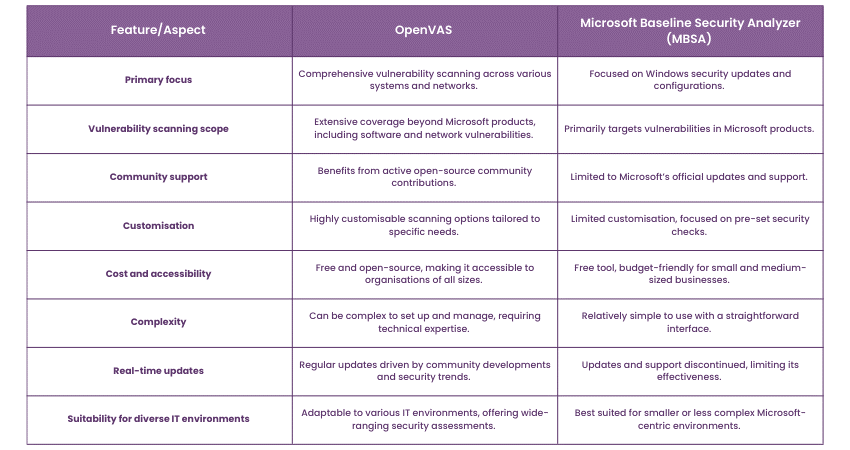
Limitations and considerations
1) Complexity and resource requirements: Due to its extensive capabilities, OpenVAS can be complex to set up and manage, requiring a certain level of expertise.
2) Dependency on community support: While community support ensures updates, the absence of dedicated commercial support might be a drawback for some organisations.
OpenVAS represents a robust and comprehensive alternative to the Microsoft Baseline Security Analyzer, especially for organisations looking for a cost-effective yet powerful vulnerability scanning solution. Its wide-ranging capabilities, supported by a vibrant open-source community, make it a valuable tool in the arsenal of modern cybersecurity strategies.
Alternative 5 – Nessus
Nessus, developed by Tenable Network Security, is a highly regarded alternative to the Microsoft Baseline Security Analyzer (MBSA). It is known for its robustness and extensive capabilities in vulnerability assessment, making it a popular choice among cybersecurity professionals.
Key features and advantages
1) In-depth vulnerability assessment: Nessus excels in conducting thorough vulnerability assessments, offering a comprehensive view of potential security weaknesses across networks and systems.
2) Regularly updated threat database: One of Nessus's strengths is its constantly updated threat database, which ensures the tool can detect the latest vulnerabilities and security threats.
3) Flexible and scalable: Nessus is highly adaptable, capable of serving both small businesses and large enterprises. Its scalability makes it a versatile tool in various IT environments.
Nessus vs MBSA
Here's a comparative table for Nessus and the Microsoft Baseline Security Analyzer (MBSA):
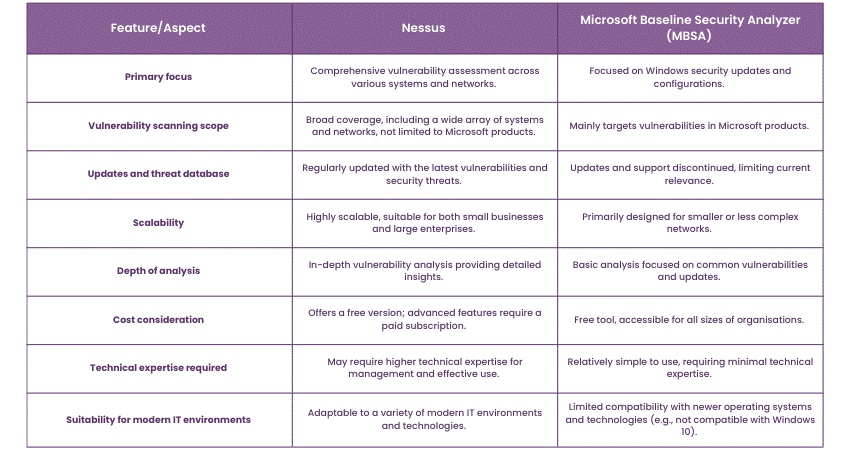
Limitations and considerations
1) Cost factor: While Nessus offers a free version, the more advanced features require a paid subscription, which might be a consideration for budget-conscious organisations.
2) Technical expertise required: The comprehensive nature of Nessus might require a certain level of technical expertise for effective utilisation and management.
Nessus stands out as a comprehensive and constantly evolving security tool, offering significant advancements over the capabilities of MBSA. Its depth of vulnerability assessment, combined with regular updates and scalability, makes it an excellent choice for organisations seeking a robust and future-proof cybersecurity solution.
Alternative 6 – Nexpose
Nexpose, developed by Rapid7, is a dynamic alternative to the Microsoft Baseline Security Analyzer, particularly notable for its comprehensive vulnerability management. Designed to adapt to the ever-changing cybersecurity landscape, Nexpose offers real-time risk assessments, making it a valuable tool for proactive security management.
Key features and advantages
1) Real-time risk assessment: Nexpose sets itself apart with its ability to conduct real-time risk assessments. This feature allows for the immediate identification and mitigation of potential security vulnerabilities.
2) Integration with Metasploit: A unique aspect of Nexpose is its integration with the Metasploit Framework, enhancing its capabilities in vulnerability analysis and exploitation testing.
3) Adaptive security: The tool continuously adapts to the latest threats and security trends, ensuring that vulnerability assessments are always current and relevant.
Nexpose vs MBSA
Here's a comparative table for Nexpose and the Microsoft Baseline Security Analyzer (MBSA):
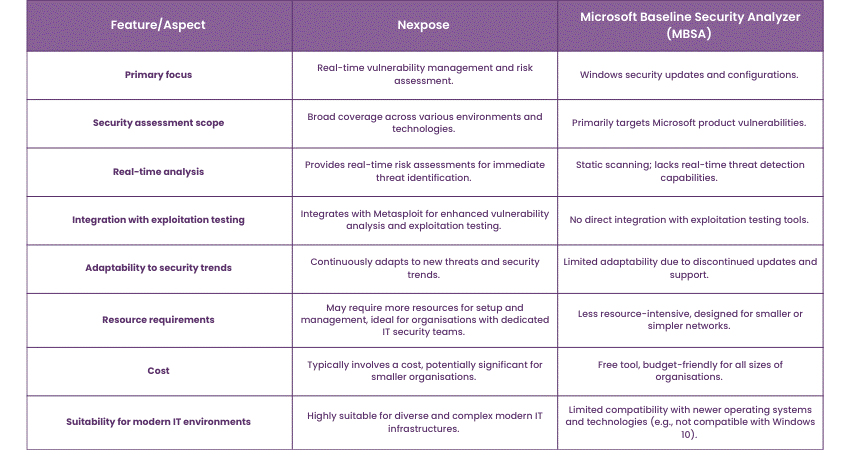
Limitations and considerations
1) Complexity and resource intensiveness: Nexpose’s comprehensive features may demand more resources in terms of setup and ongoing management, making it more suitable for organisations with dedicated IT security teams.
2) Cost factor: As a sophisticated tool, Nexpose comes with a cost that might be a significant factor for smaller organisations or those with limited budgets.
Nexpose emerges as a powerful Microsoft Baseline Security Analyzer alternative, offering advanced features for real-time risk assessment and vulnerability management. Its integration with Metasploit and adaptive security approach make it a strong candidate for organisations seeking an in-depth and proactive cybersecurity solution.
Master PowerShell security best practices with our Implementing PowerShell Security Best Practices (40555A) training – elevate your skills for a secure IT environment!
Alternative 7 – Intruder
Intruder emerges as a cloud-based security scanner and a contemporary alternative to the Microsoft Baseline Security Analyzer. It's tailored for businesses seeking a simple, yet effective solution for their cybersecurity needs. This tool stands out for its user-friendly approach to network security, aiming to simplify the often complex task of vulnerability management.
Key features and advantages
1) Ease of use and cloud-based operation: Intruder is designed with a focus on simplicity and ease of use, making it accessible to businesses without extensive IT resources. Its cloud-based nature means it's always up-to-date and requires minimal maintenance.
2) Comprehensive security scanning: Despite its simplicity, Intruder offers comprehensive scanning capabilities. It effectively identifies vulnerabilities across a wide range of systems, ensuring thorough security coverage.
3) Automated and regular scanning: Intruder automates the scanning process, regularly checking for new vulnerabilities and ensuring that security is maintained continuously.
Intruder vs MBSA
Here's a comparative table for Intruder and the Microsoft Baseline Security Analyzer (MBSA):
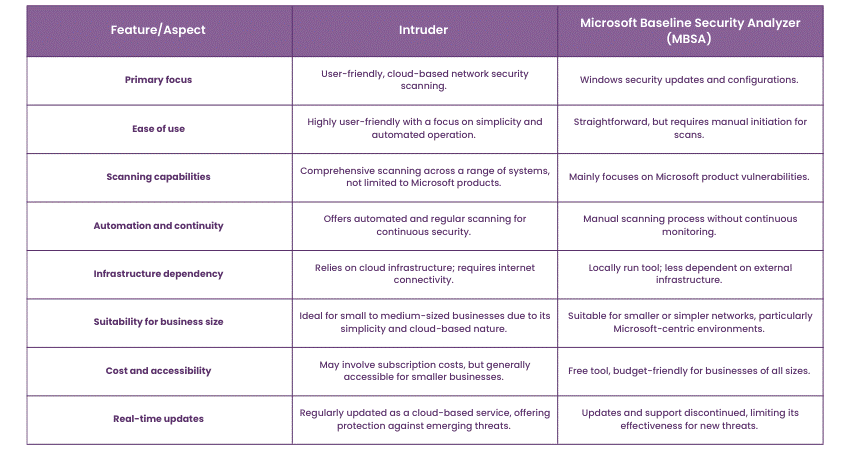
Limitations and considerations
1) Dependence on cloud infrastructure: Being entirely cloud-based, Intruder’s performance and availability are dependent on internet connectivity and cloud infrastructure.
2) Targeted towards smaller businesses: While beneficial for small to medium-sized businesses, Intruder might lack the depth required for larger organisations with complex IT infrastructures.
Intruder serves as an excellent alternative to MBSA for businesses looking for a straightforward, effective, and automated security solution. Its cloud-based operation, ease of use, and comprehensive scanning capabilities make it a practical choice for small to medium-sized businesses seeking to enhance their cybersecurity posture in a user-friendly manner.
Enhance your skills to use the threat protection capabilities of Microsoft 365 with our Microsoft Security, Compliance, And Identity Fundamentals SC900 Course now!
Conclusion
In conclusion, exploring alternatives to the Microsoft Baseline Security Analyzer has revealed a diverse range of modern solutions, each equipped to meet the evolving demands of cybersecurity. From the comprehensive monitoring of SolarWinds Network Automation Manager to the streamlined cloud-based approach of Intruder, these Microsoft Baseline Security Analyzer alternatives extend beyond MBSA's original scope. They offer enhanced capabilities such as real-time monitoring, expansive vulnerability assessments, and automated operations. The choice of an alternative should align with specific organisational needs, ensuring that the chosen tool effectively fortifies digital defences in today's rapidly changing cyber landscape.
Check out our Microsoft Information Protection Administrator SC400 Course now!
Frequently Asked Questions
Upcoming Microsoft Technical Resources Batches & Dates
Date
 Microsoft Cybersecurity Architect SC100
Microsoft Cybersecurity Architect SC100
Mon 22nd Jul 2024
Mon 23rd Sep 2024
Mon 25th Nov 2024







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


