We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

ISO 27005 is a part of the ISO 27000 sections of standards, which provides a comprehensive framework for managing Information Security risks. The standard helps protect sensitive data and ensures the integrity and availability of assets, which are critical for maintaining business continuity and trust among stakeholders. Thus, to prevent themselves from all kinds of cyber risks, it is crucial for organisations to learn What ISO 27005.
So, read this blog, to learn everything about What is ISO 27005 methodology and how it can assist you in enhancing your Information Security risk assessment process.
Table of Contents
1) Introduction to What is ISO 27005
2) The framework of ISO 27005
3) Understanding the ISO 27005 Risk Management process
4) Benefits of using ISO 27005 methods
5) Challenges and best practices of implementing ISO 27005
6) Conclusion
Introduction to What is ISO 27005
ISO 27005 is an international standard that provides organisations with guidelines and best practices for managing Information Security risks effectively. It offers a systematic framework to identify and manage risks associated with information assets.
While ISO 27001 provides a broader framework for establishing an ISMS, ISO 27005 focuses explicitly on Risk Management within that framework. Implemnting an Information Security Risk Management System in an organisation is crucial because of the following reasons:
a) Protects sensitive data from unauthorised access or disclosure
b) Safeguards the integrity of data, ensuring it remains accurate and reliable
c) Ensures the availability of information assets, preventing downtime and disruptions
d) Helps maintain compliance with legal and regulatory requirements
e) Enhances trust and confidence among customers, partners, and stakeholders
The framework of ISO 27005
ISO 27005 serves as a comprehensive framework that guides organisations through the intricate process. It forms a critical component of the ISO 27000 family of standards, which collectively address various aspects of Information Security.
ISO 27001 and ISO 27005 are two closely related standards, each with its unique focus and purpose. Understanding their respective roles is essential to grasp their complementary nature in Information Security Management.
ISO 27001 provides organisations with a comprehensive framework for establishing, implementing, and continuously improving an Information Security Management System (ISMS). An ISMS encompasses the entire spectrum of information security, including policies, procedures, and controls. It sets the stage for how an organisation manages its Information Security
ISO 27005 is characterised by its structured framework for Information Security Risk Management. This framework comprises several vital components, each contributing to the Risk Management process. These components include the following:
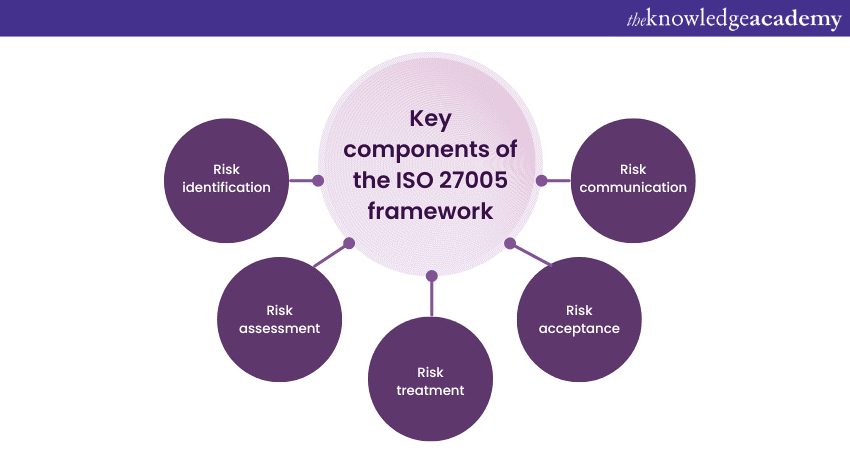
a) Risk identification: This foundational step involves systematically identifying potential risks to an organisation's information assets. It encompasses the recognition of threats, vulnerabilities, and potential impacts. Threats can range from cyberattacks to natural disasters, while vulnerabilities may stem from outdated software or inadequate access controls.
Understanding the potential consequences of a security breach, including financial losses, reputational damage, legal repercussions, and operational disruptions, is vital. This comprehensive risk identification phase sets the stage for effective Risk Management.
b) Risk assessment: Here organisation they evaluate the likelihood and potential consequences of the identified risks. Risk assessment serves as a pivotal decision-making tool, enabling organisations to prioritise their Risk Management efforts effectively. By quantifying and qualifying risks, organisations can allocate resources strategically and focus on addressing the most critical threats.
c) Risk treatment: In the risk treatment phase, organisations develop strategies and measures to manage identified risks effectively. This proactive and strategic process involves selecting appropriate controls, which can include technological solutions, policies, and procedural measures. Clear control objectives are defined to outline what these measures aim to achieve in terms of risk reduction or mitigation.
The implementation of chosen controls requires careful planning, execution, and ongoing monitoring. Risk treatment aligns security efforts with organisational goals and objectives, aiming to minimise the impact and likelihood of risks.
d) Risk acceptance: Some risks may be deemed acceptable within an organisation's risk appetite. In such cases, the risk acceptance takes place at the organisational level. Here. key stakeholders make informed decisions about whether residual risks (those that remain after applying risk treatment measures) are acceptable.
e) Risk communication: Effective communication is a vital component of ISO 27005. It ensures that all relevant stakeholders, including senior management, employees, partners, customers, and regulatory authorities, are informed about identified risks, their potential impacts, and the measures in place to address them.
Understanding the ISO 27005 Risk Management process
ISO 27005 delineates a well-defined Risk Management process tailored to the realm of Information Security. This process comprises the following key steps:
1) Establish the context: In this initial phase, organisations define the scope of their Risk Management efforts. This involves identifying relevant information assets, specifying the boundaries of the risk assessment, and articulating the objectives of the process. A clear understanding of the context is crucial to align Risk Management efforts with organisational goals.
2) Risk assessment: Following the context established, organisations delve into the risk assessment phase. Here, they identify and assess risks by:
a) Recognising potential sources of harm to information assets, which can encompass cyber threats, data breaches, and more.
b) Identifying weaknesses or gaps in the security of information assets, often stemming from factors like outdated software or inadequate access controls.
3) Risk treatment: Once risks have been identified and assessed, organisations embark on the risk treatment phase. Here, they develop strategies and measures to manage these identified risks effectively. Risk treatment involves the following:
a) Choosing security measures and controls that are best suited to mitigate or manage specific risks. These controls can encompass technological solutions, policies, and procedural measures.
b) Setting clear objectives for the selected controls, outlining what they aim to achieve in terms of risk reduction or mitigation.
4) Risk monitoring and review: Even after risk treatment measures are in place, the Risk Management process doesn't conclude. Continuous monitoring and regular reviews are essential to ensuring the ongoing effectiveness of these measures. This dynamic approach allows organisations to adapt to changing circumstances and emerging threats effectively.
Take control of your organisation's cybersecurity with our ISO 27005 Internal Auditor Training – Register for excellence today.
Benefits of using ISO 27005 methods
Now that you know What is ISO 27005 and its key components, it’s time to learn how compliance with this standard can help your organisation protect your Cybersecurity. Utilising ISO 27005 methods for Information Security Risk Management offers a range of significant advantages, including the following:
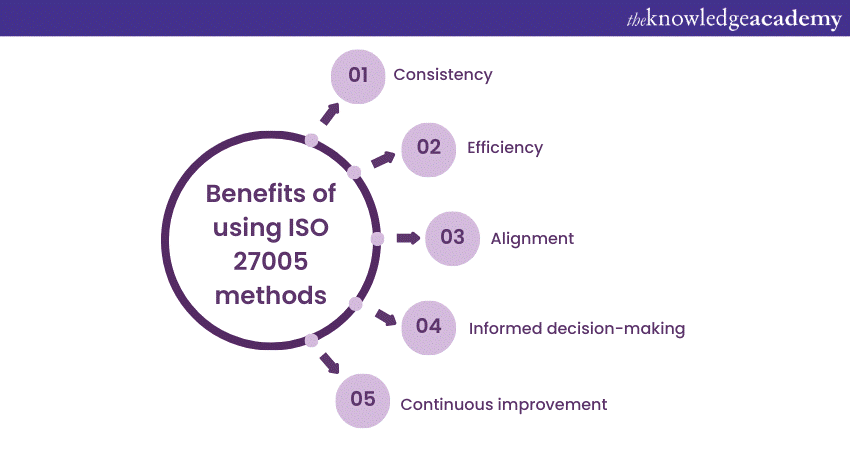
a) Consistency: ISO 27005 provides a standardised approach, ensuring that Risk Management processes are consistent and repeatable. This consistency enhances the reliability and predictability of Risk Management efforts.
b) Efficiency: The structured framework of ISO 27005 streamlines risk assessments and treatment strategies, making the process more efficient. This efficiency translates to saved time and resources.
c) Alignment: ISO 27005 aligns seamlessly with ISO 27001, ensuring that Risk Management efforts are in harmony with broader Information Security Management practices. This alignment enhances the overall effectiveness of an organisation's security posture.
d) Informed decision-making: By systematically evaluating risks, organisations gain valuable insights that inform informed decision-making. This enables them to allocate resources judiciously and prioritise risk mitigation efforts effectively.
e) Continuous improvement: Information Security is an ongoing process. ISO 27005's methods facilitate continuous improvement by regularly assessing and adapting security measures to evolving threats. This iterative approach ensures that an organisation's defences remain robust over time.
Challenges and best practices of implementing ISO 27005
Implementing ISO 27005, an international standard for Information Security Risk Management, comes with a set of challenges. It demands adherence to best practices to ensure its successful integration into an organisation's Cybersecurity framework. Some of the major challenges in implementing the ISO 27005 standard are as follows:
a) Lack of leadership support: One of the most significant challenges is the need for strong leadership support for ISO 27005 implementation. With the commitment of top management, it is easier to allocate necessary resources and create a culture of Information Security awareness.
b) Resource constraints: Many organisations struggle with limited budgets and resources for Risk Management activities.
c) Complexity and incompleteness of risk assessments: Conducting a thorough risk assessment, as per ISO 27005, can be complex.
d) Integration with existing processes: Integrating ISO 27005 with existing business processes and compliance requirements can be challenging.
e) Lack of skilled personnel: Skilled personnel are crucial for successful ISO 27005 implementation.
Best practices to implement ISO 27005
By addressing common challenges and following these best practices, organisations can enhance their Information Security Risk Management efforts and better protect their valuable assets and data. The best practices to implement the ISO 27005 standard are as follows:
a) Top-down approach: Secure strong leadership support for Risk Management initiatives. Engage executives in the process to ensure commitment, resource allocation, and a culture of security awareness.
b) Resource allocation: Adequately allocate resources, both financial and human, for Risk Management activities.
c) Comprehensive risk assessment: Conduct comprehensive risk assessments, considering all relevant factors, including assets, threats, vulnerabilities, and potential impacts.
d) Integration with other frameworks: Align ISO 27005 with existing processes and compliance requirements. Ensure that Risk Management activities complement and support broader security and business objectives.
e) Training and education: Invest in training and education for staff involved in Risk Management. Develop a group of skilled professionals who can effectively carry out risk assessments and manage risks.
Elevate your organisation's security expertise with our ISO 27005 Foundation Training.
Conclusion
The implementation of ISO 27005 is a vital step in securing an organisation's Information Security networks. While it represents a fair share of challenges, from resource constraints to complex risk assessments, the adoption of best practices can significantly mitigate these hurdles. We hope that after reading this blog, you have understood What is ISO 27005 and how to implement it effectively.
Unlock the power of ISO 27005 for robust Cybersecurity – register now for our ISO 27005 Training and protect your digital future.
Frequently Asked Questions

ISO 27005 explicitly guides the process of conducting Information Security risk assessments in compliance with ISO 27001. It provides methodology, techniques, and best practices for identifying, analysing, and evaluating information security risks. On the other hand, other ISO standards cover broader aspects of Information Security Management, such as ISO 27001, which sets out the requirements for establishing and maintaining an ISMS, or ISO 27017, which focuses on security in cloud environments.

Organisations implementing ISO 27005 should consider aligning the Risk Management process with their specific business context. Tailoring the standard to address unique risks, ensuring clear communication throughout the organisation, and regularly reviewing and updating risk assessments are crucial. Additionally, fostering a culture of continuous improvement, compliance with legal and regulatory requirements, and engaging key stakeholders in the process contribute to the effective implementation of ISO 27005 for robust information security Risk Management.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various ISO 27005 Courses, including ISO 27005 Foundation, Lead Auditor and Internal Auditor. These courses cater to different skill levels, providing comprehensive insights into Risk Retention and Risk Acceptance in ISO 27005.
Our IT Security and Data Protection blogs cover a range of topics related to ISO 27005, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT Security and Data Protection skills, The Knowledge Academy's diverse courses and informative blogs have you covered.







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


