We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Unlock the gateway to enhance app security and an impeccable user experience with the ingenious solution known as Firebase Authentication. This blog sets forth an enlightening voyage, aiming to demystify the complexities of Firebase's authentication services for developers everywhere.
By delving into the intricacies of Firebase Authentication, we transform the often-tedious user authentication process into an opportunity for innovation and exceptional user engagement. Keep reading to gain a better understanding of the processes involved in the working of Firebase Authentication.
Table of Contents:
1) What is Firebase Authentication?
2) Working of authentication
3) Users
4) Lifecycle of a user
5) Features of Firebase Authentication
6) Conclusion
What is Firebase Authentication?
At its core, Firebase Authentication serves as a comprehensive backend service, complete with user-friendly SDKs and pre-made UI libraries, designed to facilitate user authentication within an application. It boasts support for an array of authentication methods, including email and password, phone numbers, and various federated identity providers like Google, Facebook, and Twitter.
This broad spectrum of supported authentication mechanisms positions Firebase Authentication as a versatile choice for developers aiming to bolster their application's security while maintaining a smooth user experience.
Working of authentication
The essence of Firebase Authentication lies in its ability to effectively verify a user's identity. This verification process involves confirming the legitimacy of a user's credentials, be it through email and password combinations or tokens obtained from federated identity providers, against Firebase's secure and robust backend system.
Successful authentication grants users access to specific areas of an application or its services, ensuring that access is reserved exclusively for authorised individuals, thereby upholding the application's security and integrity.
Want to design your own website? Sign up for our Website Design Course - Register now!
Users
In the domain of Firebase Authentication, 'users' are defined as entities associated with a Unique Identifier Detail, or UID, which Firebase generates upon successful authentication. This UID plays a pivotal role in managing user-specific data and interactions within an application, enabling each user's tailored and secure experience. By leveraging UIDs, developers can facilitate personalised user interactions and ensure the safe handling of user data.
Lifecycle of a user
The user's journey within Firebase Authentication encompasses everything from account creation to eventual deletion. This journey includes critical steps such as registration, email verification, password resets, account modifications, and finally, account termination.
Firebase meticulously secures each stage of this lifecycle with robust security protocols, ensuring a seamless transition from one stage to the next and the utmost protection of user data throughout their journey.
Be the next Digital Genius that builds a revolutionary app! Start your journey with our Mobile App Development Training Using Flutter Course - Register now!
Features of Firebase Authentication
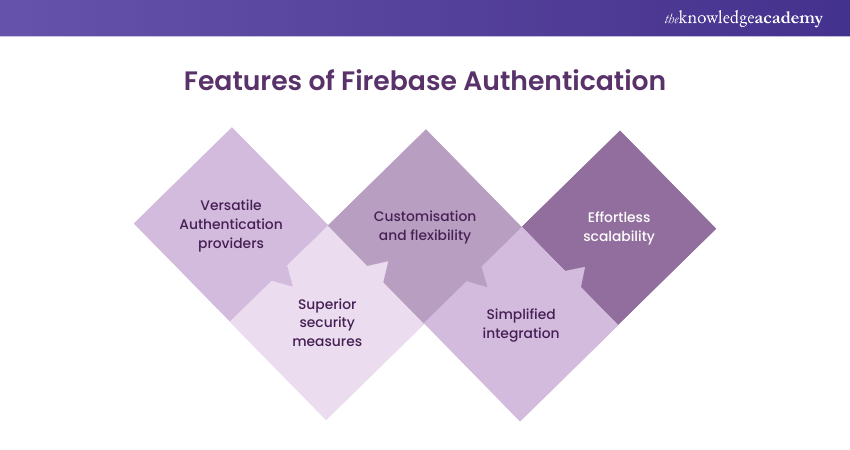
Firebase Authentication distinguishes itself through a wide range of compelling features:
a) Versatile Authentication providers: It supports a multitude of authentication methods, including, but not limited to, email/password combinations, phone numbers, and various social media platforms, offering unparalleled flexibility.
b) Superior security measures: Firebase Authentication implements advanced security measures to safeguard user data, incorporating secure token management and data encryption.
c) Customisation and flexibility: It offers customisable UI components and the flexibility to seamlessly integrate with other Firebase services or external APIs, catering to various development needs.
d) Simplified integration: With straightforward Software Development Kits (SDK) available for web, Android, and iOS platforms, Firebase Authentication simplifies integrating authentication services into your application.
e) Effortless scalability: Engineered to scale with your growing user base, Firebase Authentication can effortlessly support millions of users, making it an ideal choice for applications of any size.
Conclusion
This blog has unveiled the critical aspects of secure and efficient user authentication practices by navigating through the intricacies of Firebase Authentication. Firebase Authentication emerges not only as a shield for enhancing application security but also as a cornerstone for cultivating refined, user-centric experiences. App development now blends security with seamless user engagement for unforgettable digital experiences.
Learn to build websites with ease. Sign up for our Elm Web Development Training Course - Register now!
Frequently Asked Questions

Firebase Authentication necessitates online connectivity for initial logins and the authentication process. However, the Firebase Auth SDK is designed to cache the user's authentication state post-login, enabling certain operations to continue under limited offline conditions and offering some operational flexibility even without a constant internet connection.

Firebase Authentication offers its core services, including email/password authentication, anonymous sign-in, and authentication through most federated identity providers, at no cost. Nevertheless, phone authentication comes with a limited number of free verifications, after which fees are incurred based on the volume of usage. Thus, developers must consider the potential costs for high-volume applications utilising phone number verification.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Programming & DevOps, including Analysis & Design Using UML, AngularJS Developer and BlueGriffon Training. These courses cater to different skill levels, providing comprehensive insights into What is Firebase?.
Our Programming & DevOps Blogs cover a range of topics related to Leadership, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Project Management skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming Programming & DevOps Resources Batches & Dates
Date
 Mobile App Development Course
Mobile App Development Course
Fri 26th Jul 2024
Fri 25th Oct 2024







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


