We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Enterprises around us have become readily digitised, having opted for online services and computer networks integrated into their business practices over the years. This has made them more accessible to the general population. However, with the benefits of the digital age, modern threats have also evolved that present huge risks for enterprises and individuals alike. This led to a huge growth in countermeasures against cyber-crimes and the establishment of Cyber Security Architecture.
According to a report from the FBI in 2021, nearly 22% of all data breaches were executed by phishing. Thus, making it one of the most prevalent cybercrimes today. Cybersecurity Standards became a strong defence mechanism against such attacks. They are collectively known as Security Architecture. Learn what Cyber Security Architecture is and why it is essential. Understand the architecture to protect your business from threats.
Table of Contents
1) Understanding Cyber Security Architecture
2) Elements of Security Architecture
3) Importance of Security Architecture
4) Cyber Security as a profession
5) Conclusion
Understanding Cyber Security Architecture
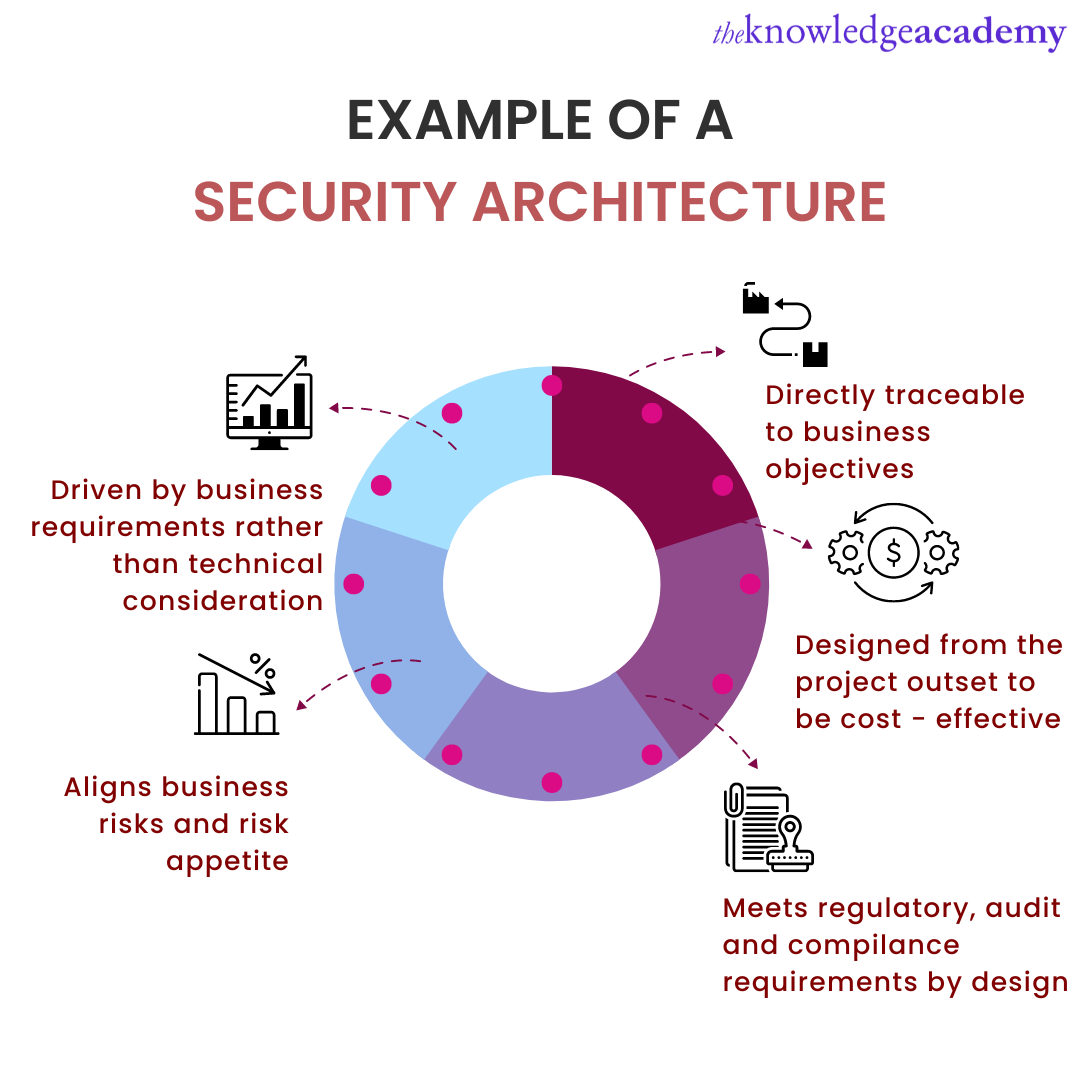
Before we discuss Cyber Security and its architecture, let's understand a little about Cyber Security for Business. It refers to all actions and measures which people and enterprises use to ensure the safety and privacy of the computer network, its systems, data and the people using it.
Cyber Security ensures that any form of virtually stored data is defended from malicious intent. It prevents your data and other online resources from being altered or used without your permission.
The principles and framework that determine the nature of Cyber Security within an organisation are essentially referred to as Cyber Security Architecture or Security Architecture. Such a framework defines the design and behaviour of computer networks, including the safety measures taken to prevent cyber-attacks.
Wish to master the art of preventing Cyber-attacks? Then register for the CCNA Cybersecurity Operation Training today!
Elements of Security Architecture
Cyber Security Architecture constitutes many small components, each reinforces the secure nature of a computer network. Even the people who utilise the benefits of the vast computer network daily are categorised as a component of Security Architecture.
The people in Cyber Security
The people who work for an enterprise interact with a computer network on an everyday basis to perform their respective jobs. Secure computer networks help the people within an organisation by increasing their productivity, providing them with better access to data and support more efficient communication. Similarly, the people who utilise such networks also influence it with their behaviour. Even the most minor action of an employee can become a fatal mistake which can lead to an unauthorised person accessing the network, making it highly vulnerable.
An employee might not take such action intentionally, but it may happen due to ignorance or lack of training. Thus, training your staff is vital to building a good Cyber Security Architecture. Educating your employees on how and why they are supposed to follow safety protocols can protect them and your organisation from malicious and external threats.
Take our Cyber Security Risk Management course and be prepared for future cyber-attacks!
Safety practices in Cyber Security
Some organisations' safety protocols also refer to the tools and procedures your employees use every day. Your working policies and standard practices directly impact your staff, thus affecting the Security Architecture in the long run. Therefore, it is essential to integrate safety-based practices within everyday tasks to reinforce the safety standards.
Making your safety policies and standard procedures coherent and concise is equally essential. Even if a Cyber Security design is theoretically flawless in preventing all external threats, it depends entirely on the people in your enterprise abiding by those practices. A perfect Cyber Security design can become useless if people fail to comply with its standards.
Cyber Security framework standards
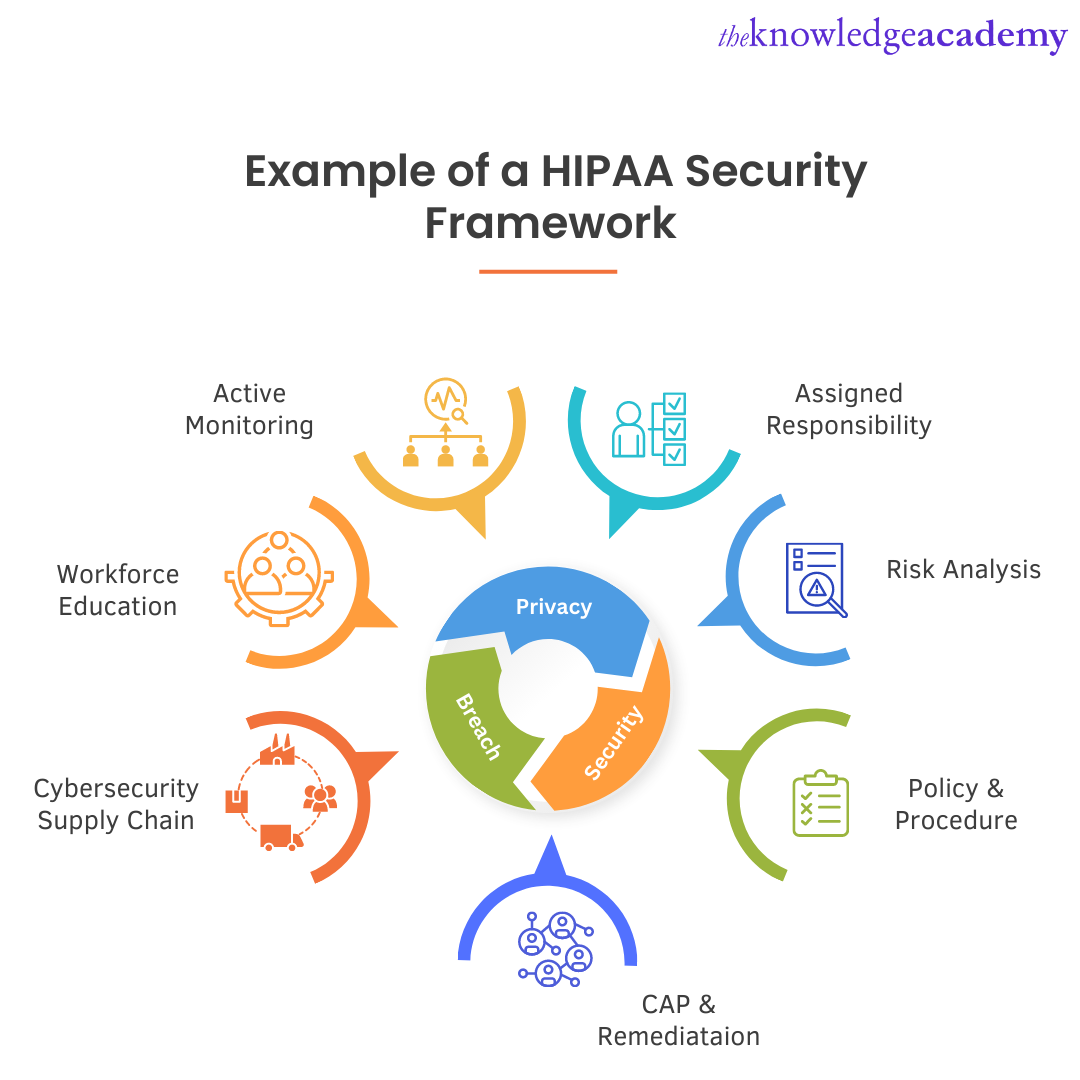
Many enterprises hire a Security Architect to protect a company's resources. A Security Architect is usually responsible for creating a Cyber Security Architecture Framework while keeping the needs and demands of an enterprise in mind.
But when a company can't financially afford the aid of a Security Architect, they adopt a pre-existing framework. Some standards for Security Frameworks like ISO 27001, PCI DSS, CCPA, EU GDPR AND HIPAA are used widely and can be readily adopted by a company. Later these standards and frameworks can be customised according to the individual needs of the company.
Importance of Security Architecture
It is evident that Cyber Security is necessary to protect one's system and network. It's essential in reducing and fighting cyber threats, leading to a trustable enterprise, thus, building good customer relations. But let's understand the purpose of developing an Architecture in Cyber Security. Its core function lies in setting the standards for implementing Cyber Security on the organisation's network or related data, emphasising the need for robust Cyber Security Essentials to establish and maintain a secure framework.
Legal obligations for Cyber Security
Cyber Security strongly influences a company’s reputation, making it more than just a choice. In a competitive environment, where minor differences can affect customer satisfaction, safety protocols are necessary to earn customer trust. It was one of the reasons that made the Standard for Security Framework a legal necessity. This made it mandatory to possess a security-based architecture that adheres to a certain standard.
If a company fails to adhere to a certain cyber-protection standards, there is always a potential for data theft to occur. Under the circumstances where a data leak occurs in an enterprise, your customers have a chance of getting harmed, and it also leads to public distrust. This causes a loss of faith in an enterprise and its services in the eyes of the public, which becomes extremely difficult to gain back.
Cyber Security Architecture implementation becomes a regulatory compliance to ensure such a mishap does not occur. A well-designed Security Architecture ensures the possibilities of cyber security attacks get reduced to a minimum. Most large-scale companies hire a Cyber Security Architect who specialises in creating, designing and implementing a safer and more robust network infrastructure.
Stream-lined information
The improved infrastructure that adheres to Cyber Security Architecture standards has added benefits to all computer network work. One such added benefit of an improved architecture is your data flow becoming smoother and more systematic. This makes data management and monitoring much simpler, giving you easy access to information.
Cyber Security as a profession
A person who specialises in the design, creation and implementation of Cyber Security Standards is known as a Cyber Security Architect or Security Architect. They start their job by evaluating the current safety standard of an enterprise. They do so by testing the existing components of the computer network with a penetration test and ethical hacking, which determines how susceptible a computer network is to actual cyber-attacks.
Some components commonly tested by them for vulnerabilities are the networks like LAN and WAN, as well as the effectiveness of pre-existing defence mechanisms, like the firewall. After making a list of current flaws with the network infrastructure, they suggest physical, network and administrative changes.
Security Architects are also responsible for integrating new technologies or updating the previous ones according to the requirement of an organisation. They create a cost estimation for all necessary changes in the architecture, tallying it with the company-provided budget. They also guide administrative and security teams on properly using new technology.
Although these are general tasks performed by a Security Architect, their roles are not set by a line drawn in the sand. A company’s demand and expectations from a Security Architect vary from one company to other. There are chances a company might expect a Security Architect to gain a complete understanding of their workflow and infrastructure. In contrast, another company might ask them to infiltrate their database as a test for their pre-existing safety measures working as it is supposed to.
Prerequisites for being a Cyber Security Architect
To pursue this career, the essential prerequisite is to have a bachelor's degree or master's specialising in Cyber Security. But the educational requirement for this field offers flexibility and is not limited to people with a specialised Cyber Security degree. If your educational background varies from the prerequisites, you can compensate by taking IT-based classes and certification in Cyber Security specialisation.
Although it might seem like this completes all the basics necessary for approaching this career, the reality is far more complex. A large majority of enterprises prefer to hire a Security Architect with actual hands-on experience with Cyber Security. As a result, the demand for Cyber Security Specialists draws a hard line between candidates with five years or greater experience in the field vs those with less or no experience.
Additionally, a Cyber Security Architect needs to have a specific combination of skills that separates him from other job roles in the Cyber Security field. Some basic hard skills are mandatory in this field with different operating systems such as Windows, Linux and UNIX. They are expected to possess experience with security components such as firewalls and knowledge of wireless connection components, like Routers and switches.
Similarly, a profession as a Security Architect demands a set of soft skills as well. Some such skills are leadership qualities to guide a group of people, attention to detail to detect vulnerabilities and the ability to explain technical concepts to non-technical staff in layperson's terms, hence learning to communicate in a simpler language which is easier to grasp for their team.
Build your Cyber Security based skillset with this CISSP Training course, and raise your career prospect as a Security Architect today!
Career growth and salary in Cyber Security
According to Glassdoor, a Cyber Security Architect has an average annual base pay of £77,311 in the UK. The salary for a Security Architect is bound to vary based on experience and location. Due to the constant virtualisation of enterprises and easier access to technology for the general public, Cybercrimes are only bound to increase over the coming years. This will create a higher demand for Cybersecurity Specialists in the upcoming years.
Conclusion
Cyber Security is an important aspect of network infrastructure. Its architecture refers to the principles, standards and framework set to defend oneself and their enterprise from cyber-attacks. Hopefully, this blog helped you understand the benefits, components and Scope of Cyber Security Architecture.
Interested in building a career as a Security Architect? Then this Microsoft CyberSecurity Architect SC100 is the right fit for you!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 9th Aug 2024
Fri 6th Dec 2024
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course





 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


