We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

The Certified Information Systems Auditor (CISA) certification is an excellent leverage to help IT auditors and entry-level individuals advance in their careers. It trains individuals to conduct audits, process control activities, and monitor information and business systems. This certification is among the most demanded programs by organisations worldwide and requires immense dedication, commitment, and resilience from prospective candidates. There are several CISA Domains that you can learn from this blog.
There are more than 150,000 active members of ISACA and over 10,000 active CISA certification holders, according to a report by ISACA. This blog discusses the five CISA Domains of the exam, their sub-domains and the knowledge which candidates must prepare before studying the domain subject areas.
Table of Contents
1) Understanding the CISA Domains
2) An Introduction to the 5 Domains of CISA
a) Domain 1 - Auditing Process of Information Systems
b) Domain 2 – IT Governance and Management
c) Domain 3 – Acquisition, Implementation, and Development of IS
d) Domain 4 – Operations and Resilience of IS
e) Domain 5 – Protection of information assets
3) Conclusion
Understanding the CISA Domains
The Certified Information Systems Auditor (CISA) is one of the most demanded career options available to professionals in the IT industry. Candidates may require about four to eight months to prepare for their CISA exam attempt, depending on their work experience and knowledge. The professionals keen on getting accredited with the CISA certification must complete the courseware that covers all five domains referred to as modules. The examination ensures that the candidate professionals, like the IT auditors, are prepared to handle real-world situations.

An introduction to the 5 Domains of CISA
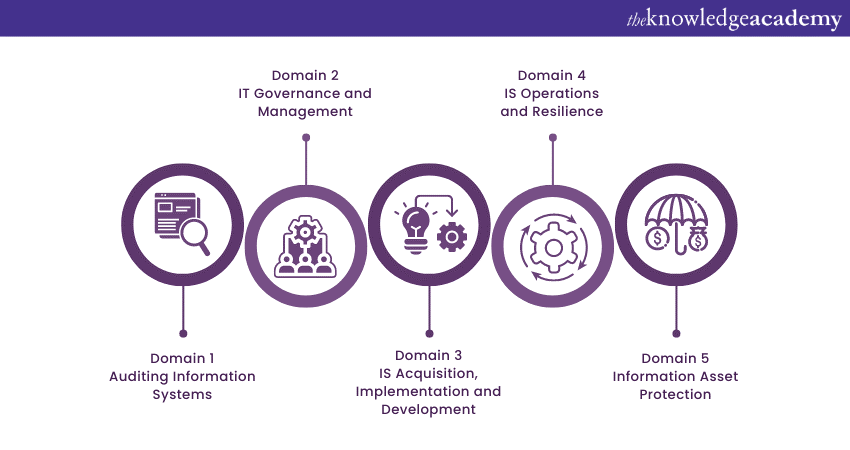
The five CISA Domains covered include their subdomains, which are graded on 200 to 800 points. Furthermore, participants must achieve at least 450 points or more to be eligible for the examination. They will be allotted four hours for the exam, which contains 150 questions in the multiple-choice format.
The ISACA has defined the five exam domains for candidates in the following manner:
Domain 1 – Auditing information systems
The first CISA Domains of the exam comprises the basics of IT auditing and how to provide the appropriate auditing services. These services align with the necessary best practices for controlling and protecting information systems. Furthermore, the domain also encompasses developing and implementing a complex IT audit. The candidate will be tested to determine whether they can apply these industry standards and work environment regulations.
They are also expected to be familiar with the IT assurance standards of the ISACA and the rules, techniques, and tools of the audit process. Candidates will be introduced to the audit services of the organisation through the process of auditing information systems. This IS audit process abides by the ISACA's viewpoint of the audit regulations. It also encompasses the motto that helps organisations protect and control their information systems.
The most important segments of the first domain also contain the risk-based technique of the IS audit. It must be ensured that the crucial detail areas need to be audited correctly. Additionally, the candidates should know how to organise specific audits to recognise if the information techniques are secure and in control. More importantly, they need to be capable of fulfilling the planned objectives of the audit process.
Furthermore, candidates must be capable of communicating the outcome of the IT audit process. They then must prepare suggestions for their stakeholders via audit reports and meetings. They need to be well-versed in research audits to understand the changes made by the management system.
This domain of auditing information systems contains the following sub-domains:
a) Evolution of an IS audit process
b) Control the self-assessment
c) Conduct an IS audit
d) Internal controls
e) Analysing risk
f) IT assurance and audit guidelines of the ISACA
g) IS audit function management
Acquire the knowledge of security tools and IT audits for CISA by signing up for the CISA Training course now!
Domain 2 – IT Governance and Management
The second CISA domain focuses on the management and governance of IT systems. It tests candidates' capabilities to recognise crucial issues and offers suggestions to safeguard information and other associated technologies. Furthermore, the domain concentrates on providing the necessary leadership training and assurance. It also assesses whether the structure of the organisation and its processes are ideal for achieving its goals and strategies.
Candidates getting examined in this domain must be able to evaluate an organisation's IT standard. Their demonstration of the standard encompasses aspects such as the IT processes and directives for system maintenance and implementation. They also must include the development of IT strategies and their alignment with the organisation's goals.
The second domain also examines the candidates' ability to assess the performance, direction and decisions involved in the company's IT governance structure. Most of the preparation consists of verifying the alignment levels with the company's regulatory needs. Furthermore, business continuity is another focal point of the domain because it is important to learn about a company's Business Continuity Plan (BCP) with a recovery plan for IT disasters.
Other IT audit management and governance tasks encompass the controls for checking the company's procedures, policies and standards. Additionally, the main performance factors of the IT structure must be evaluated if the management team receives adequate information.
This domain of IT management and governance contains the following subdomains:
a) Business continuity auditing
b) Procedures and policy
c) Management of risk
d) Management of IS practices
e) Process and Maturity models
f) Planning business continuity
g) IS organisational structure and responsibilities
h) Corporate governance
i) IT governance
j) Information Security strategy
k) Allocation practices and investment in IT
l) Monitoring practices and IT assurance for senior and board management
Domain 3 - Acquisition, Implementation, and Development of IS
The third CISA Domains covers the aspects of acquisition, implementation, and development of IT systems. Candidates should be prepared to write about developing strategies, governing projects, testing methodologies, and managing releases.
The activities to be done in this domain are all practical tasks. Therefore, applicants are expected to understand how to calculate the investments for the business case of information systems. The calculation must include subsequent acquisitions to assess whether the business case will fulfill its goals.
Candidates need to know how to analyse the process of IT contract management and the selection of suppliers to ensure the satisfaction of the company's service needs. Further tasks in the third domain involve the assessment of the company's organisational framework and project control. This assessment work must be done simultaneously while the organisation manages its risk and reviews its business steps to recognise if the project is going according to plan.
Candidates are expected to be capable of evaluating controls of information systems during the time of development. Additionally, the testing segment of the compliance procedure must be performed with the company's standards and policies, among other needs. Candidates should be able to assess the readiness of the information systems for migration purposes. As a result, they will understand whether the project outcomes and deliverables of the organisation are being fulfilled. Finally, they need to determine the post-implementation reviews of the IT system to recognise if the project submissions are being satisfied.
The third domain of the CISA contains the following subdomains:
a) Audit of application controls
b) Audit of acquisitions and maintenance
c) Maintenance practice of information systems
d) System development techniques
e) Process enhancement practices
f) Business application development
g) Business realisation
h) Alternative methods of development
i) Infrastructure acquisition practices
Domain 4 – Operations and Resilience of IS
The fourth CISA Domains tests a candidate's knowledge of IS operations and business resilience. The ISACA tests candidates, expecting them to evaluate the IT service management framework and internal practices. It will also help candidates to know whether control and service levels require necessary adjustments by the company and if strategic needs are being satisfied in time.
Candidates need to prepare themselves by studying the organisation of reviews for information systems. This takes place so they understand whether to proceed to achieve the organisation's goals. Furthermore, the domain tests candidates on their ability to assess operational activities like scheduling and configuring jobs, managing capacity and work, upgrades and patch releases, and so on.
Additionally, the domain examines a candidate's ability to assess database management practices. The candidate's data integrity knowledge and database optimisation are tested. They must also know how strategic objectives can be achieved throughout the project lifecycle.
The fourth domain has been designed to ensure that candidates are familiar with assuring the processes in information systems. The ISACA considers that IT auditors must be capable of evaluating the end-users of computing systems and the resilience of IT systems.
The fourth domain of the CISA contains the following subdomains:
a) Disaster recovery plan
b) Information systems operations
c) Information systems hardware
d) Information systems software
e) Information systems network infrastructure
Candidates will find it easier to tackle the fourth domain of the CISA examination by preparing themselves with the following topics beforehand:
a) Frameworks of IT service management and service-level agreements.
b) Third-party performance monitoring methods and compliance with various regulatory requirements and service agreements.
c) An elementary understanding of Enterprise Architecture (EA) and functionalities of fundamental technologies like system software, database management systems, middleware, and so on. Candidates should also know about system resiliency techniques and tools like clustering and removing single points of failure.
d) Important concepts pertaining to IT asset management, licensing software, managing source code, and inventory best practices.
Domain 5 – Protection of information assets
The fifth CISA domain is one of the most important, covering about 25 percent of the exam subject areas. This domain encompasses all the topics related to information security. The role of an IT auditor requires them to assure the confidentiality and availability of information assets.
Furthermore, the assurance the auditors provide also includes evaluating the policies, standards, and procedures in information security. The design and implementation of many controls like system and logical security controls, data classification processes and environmental controls follow these aspects of IS.
Candidates should prepare for this domain because it is one of the most essential sections of the CISA exam. The ISACA has designed this certification considering the security challenges in business and training aspiring professionals to tackle real-world situations. The fifth domain encompasses a quarter of the exam questions.
ISACA expects its prospective CISAs to be capable of evaluating the procedures meant for alignment with the policies and standards of an organisation. They also need to assess whether the procedures for storing, transporting and disposing assets are sufficiently protected. Furthermore, they must determine the effectiveness of the information security program and whether it aligns with the organisation's objectives.
Candidates will find it easier to tackle the fifth domain of the CISA examination by preparing themselves with the following topics beforehand:
a) General industry practices and requirements like laws regarding information security and the reporting of security controls.
b) Privacy-related principles
c) Practices associated with protecting information assets include physical access controls for identifying, authenticating and restricting end users to authorised hardware.
d) Security controls associated with system software and database management systems.
e) The security risks related to the virtualisation of hardware or network resources, using wireless devices, and personal devices.
f) Knowledge of security concepts for voice communication protocols like VoIP (Voice Over Internet Protocol) and PBX (Private Branch Exchange), configuration and maintenance of network security control, encryption techniques like RSA (Rivest Shamir Adleman) and AES (Advanced Encryption Standard), and public key infrastructure (PKI) and digital signature techniques (asymmetric cryptography).
g) The security risks related to peer-to-peer computing and web-based technologies like social networks, blogs and message boards.
h) The security processes are designed to store, retrieve, and transport confidential information assets.
i) The procedures utilised to implement security awareness programs.
j) Understanding the techniques used to attack information systems and the tools designed to prevent and mitigate these attacks, including the security testing techniques, like Penetration testing and Vulnerability scanning.
k) Understanding the processes associated with monitoring and response to various security incidents like escalation procedures, forensic investigation processes, data preservation, and evidence procedures.
l) Learning about factors contributing to fraud risk in relation to information asset protection.
Conclusion
The ISACA's CISA certification has proven to be a distinguished award for professionals preparing to become IT auditors. They are trained to tackle real-world situations after being CISA certified. The preparation leading to a successful exam attempt is like a candidate's rite of passage, which even IT auditors can undertake.
The certification is beneficial for entry-level individuals and experienced professionals. Investing in the certification makes them more capable of evaluating information systems and providing leadership to their organisation. It takes only the keenest and most determined professionals to be eligible candidates for the CISA exam, and it gives them access to existing CISAs who can guide them adequately. We hope you enjoyed reading about the five CISA Domains and their importance in the information management sector.
Learn about the audit process for information systems by signing up for the Certified Information Systems Auditor course now!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 CISA Certified Information Systems Auditor
CISA Certified Information Systems Auditor
Sat 11th May 2024, Sun 12th May 2024
Tue 28th May 2024
Sat 15th Jun 2024, Sun 16th Jun 2024
Mon 24th Jun 2024
Sat 13th Jul 2024, Sun 14th Jul 2024
Mon 22nd Jul 2024
Sat 10th Aug 2024, Sun 11th Aug 2024
Mon 19th Aug 2024
Sat 14th Sep 2024, Sun 15th Sep 2024
Mon 16th Sep 2024
Sat 12th Oct 2024, Sun 13th Oct 2024
Sat 9th Nov 2024, Sun 10th Nov 2024
Mon 25th Nov 2024
Sat 7th Dec 2024, Sun 8th Dec 2024
Mon 16th Dec 2024
Mon 20th Jan 2025
Mon 17th Feb 2025
Mon 17th Mar 2025
Mon 28th Apr 2025
Mon 19th May 2025
Mon 16th Jun 2025
Mon 21st Jul 2025
Mon 18th Aug 2025
Mon 15th Sep 2025
Mon 20th Oct 2025
Mon 17th Nov 2025
Mon 15th Dec 2025







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


