Get a custom course package
We may not have any package deals available including this course. If you enquire or give us a call on +61 272026926 and speak to our training experts, we should be able to help you with your requirements.
Module 1: Information Systems
Module 2: Information Security
Module 3: Information Security Types
Module 4: Major Challenges to Information Systems Security
Module 5: Common Information Security Risks
Module 6: Information Security Technologies


The Information Systems Security Management Training Course is designed to equip individuals with the skills and knowledge required to manage and maintain the security of information systems within organisations. This CISSP Training Course will benefit the following professionals:
There are no formal prerequisites for this Information Systems Security Management Training Course. However, prior experience in Information Technology (IT) is recommended but not mandatory. Also, familiarity with security concepts might prove to be beneficial for the delegate.
This Information Systems Security Management Training Course offers a comprehensive exploration of Information Systems Security Management. In today's interconnected world, understanding the principles of security is crucial. It equips individuals with the skills to safeguard data and mitigate cyber threats, ensuring the resilience and integrity of organisation's digital assets.
Proficiency in Information Systems Security Management is essential, and professionals aiming to master this subject include Cybersecurity Experts, IT Managers, System Administrators, and anyone responsible for ensuring the confidentiality, integrity, and availability of data. These professionals are the first line of defence against cyberattacks, and this course empowers them to excel in this critical role.
This intensive 1-day Information Systems Security Management Course equips delegates with the fundamental knowledge and tools needed to manage and secure information systems effectively. Delegates will gain a deep understanding of security principles, risk management, access control, cryptography, and network security. Practical insights, real-world scenarios, and hands-on exercises ensure that delegates leave with tangible skills to enhance their organisation's security posture.
Course Objectives
After completing this CISSP Course, delegates will be armed with the knowledge and skills required to contribute to the enhanced security of their organisations and further their careers in the field of cybersecurity.




Why choose us
Experience live, interactive learning from home with The Knowledge Academy's Online Instructor-led Information Systems Security Management Training. Engage directly with expert instructors, mirroring the classroom schedule for a comprehensive learning journey. Enjoy the convenience of virtual learning without compromising on the quality of interaction.
Unlock your potential with The Knowledge Academy's Information Systems Security Management Training, accessible anytime, anywhere on any device. Enjoy 90 days of online course access, extendable upon request, and benefit from the support of our expert trainers. Elevate your skills at your own pace with our Online Self-paced sessions.
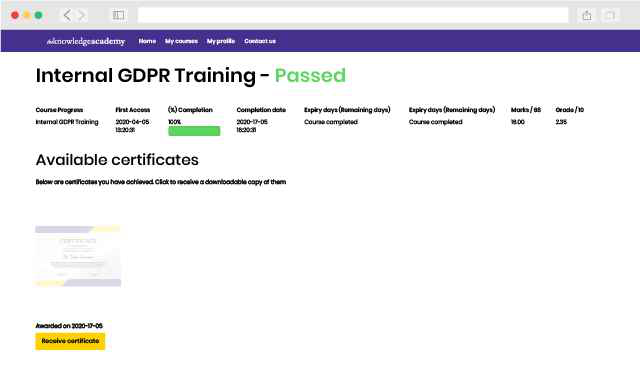
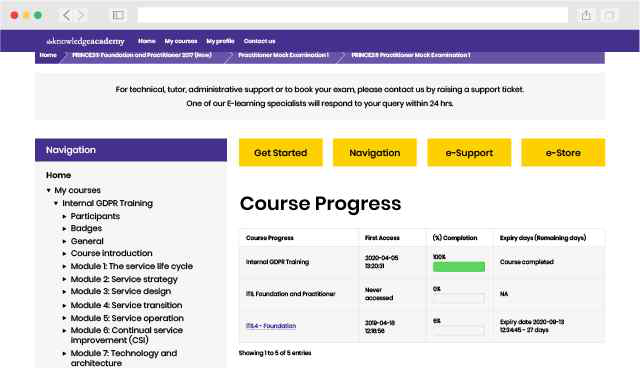
Experience the most sought-after learning style with The Knowledge Academy's Information Systems Security Management Training. Available in 490+ locations across 190+ countries, our hand-picked Classroom venues offer an invaluable human touch. Immerse yourself in a comprehensive, interactive experience with our expert-led Information Systems Security Management Training sessions.

Boost your skills with our expert trainers, boasting 10+ years of real-world experience, ensuring an engaging and informative training experience

We only use the highest standard of learning facilities to make sure your experience is as comfortable and distraction-free as possible

Our Classroom courses with limited class sizes foster discussions and provide a personalised, interactive learning environment

Achieve certification without breaking the bank. Find a lower price elsewhere? We'll match it to guarantee you the best value
Streamline large-scale training requirements with The Knowledge Academy’s In-house/Onsite Information Systems Security Management Training at your business premises. Experience expert-led classroom learning from the comfort of your workplace and engage professional development.

Leverage benefits offered from a certification that fits your unique business or project needs

Cut unnecessary costs and focus your entire budget on what really matters, the training.

Our Information Systems Security Management Training offers a unique chance for your team to bond and engage in discussions, enriching the learning experience beyond traditional classroom settings

The course know-how will help you track and evaluate your employees' progression and performance with relative ease


You won't find better value in the marketplace. If you do find a lower price, we will beat it.

Flexible delivery methods are available depending on your learning style.

Resources are included for a comprehensive learning experience.




"Really good course and well organised. Trainer was great with a sense of humour - his experience allowed a free flowing course, structured to help you gain as much information & relevant experience whilst helping prepare you for the exam"
Joshua Davies, Thames Water



 Who is CISSP for?
Who is CISSP for? History of CISSP
History of CISSP Benefits of CISSP for Individuals
Benefits of CISSP for Individuals Benefits of CISSP for Businesses
Benefits of CISSP for Businesses CISSP Case Studies
CISSP Case Studies CISSP Methodologies
CISSP Methodologies CISSP Examinations and Format
CISSP Examinations and Format What is an Exam Pass Guarantee?
What is an Exam Pass Guarantee? How long is my CISSP Certification valid for and what are CPEs?
How long is my CISSP Certification valid for and what are CPEs? How do I pass a CISSP exam and what happens if I fail?
How do I pass a CISSP exam and what happens if I fail? How do I book a CISSP course?
How do I book a CISSP course? What organisations use CISSP?
What organisations use CISSP? CISSP Job Roles
CISSP Job Roles How to add CISSP to your CV
How to add CISSP to your CV How to add CISSP to your LinkedIn
How to add CISSP to your LinkedIn
 Back to course information
Back to course information
We may not have any package deals available including this course. If you enquire or give us a call on +61 272026926 and speak to our training experts, we should be able to help you with your requirements.
 If you miss out, enquire to get yourself on the waiting list for the next day!
If you miss out, enquire to get yourself on the waiting list for the next day!

close


Press esc to close

close
Fill out your contact details below and our training experts will be in touch.



Back to Course Information