We may not have the course you’re looking for. If you enquire or give us a call on +1 7204454674 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

A study by Gartner revealed 88% of business executives consider Cybersecurity Breaches to be a direct threat to their operations. This is indicative of the shifting perspective on the impact of cybercrimes on the routine operations of a business entity.
Today, companies constantly upgrade Cyber Security policies to deal with different threats. It holds significant importance for companies as data security continues to be an essential measure of performance and reliability. There are different types of threats in Cyber Security that organisations have to deal with and combat. Companies must develop and implement highly effective Cyber Security measures and systems to mitigate the threats.
In recent years, the frequency of cyberattacks and breaches has increased substantially. It is the most significant danger to companies, as such an event can adversely impact business operations. In this blog, we will cover seven types of Cybersecurity Breaches that you should be aware of going into 2023.
Table of Contents
1) What are Cyber Security Breaches?
2) Seven types of Cyber Security Breaches
3) Top Cyber Security Breaches
4) How to prevent Cybersecurity Breaches?
5) Conclusion
Join Cyber Security Training courses to learn ways to protect your data and strengthen organisations' security systems, as cyber-attacks are increasing yearly!
What are Cyber Security Breaches?
When hackers bypass security protocols to obtain unwanted access to data and networks, it is known as a Cybersecurity Breach. It is also known as a security violation and influences the company negatively. The organisations must spend time, money, and other resources on fixing the breach and implementing systems that ensure such incidents do not repeat in the future.
Today, companies spend millions to monitor their systems to identify and mitigate incidents of security breaches before they cause damage to the company. Understanding security breaches and their mitigation plans is critical because it can help avoid such situations altogether. If the company falls victim to such attacks, it can ensure it does not lose essential data. A security breach can be the result of any of the following:
1) Human error
2) Old and unpatched vulnerabilities in Cyber Security
3) Malware
4) Theft of portable data-carrying devices like hard disks and flash drives
5) Insider leak
Register today for the Cyber Security Awareness course to better understand modern cyber threats!
Seven types of Cyber Security Breaches
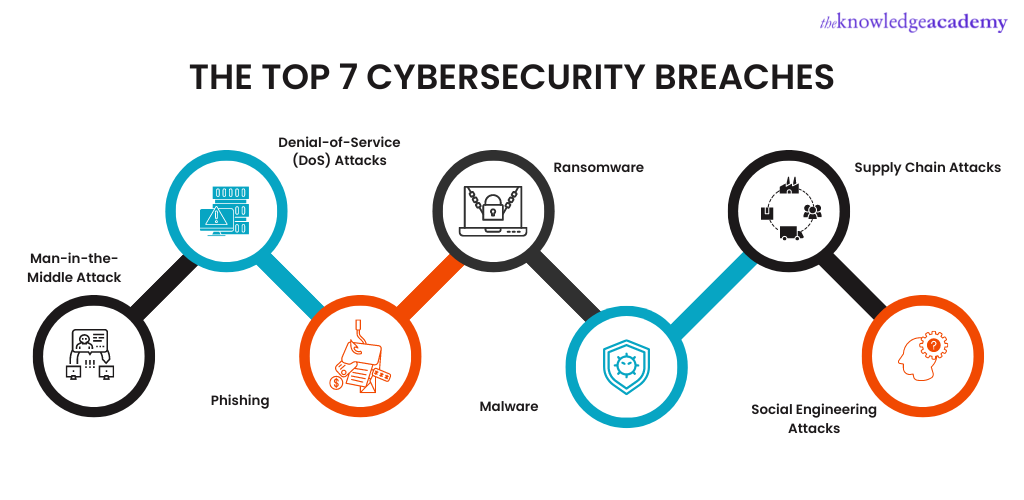
A security breach is said to happen when an unauthorised individual or application gains access to a network or data. Cybersecurity Breaches have rapidly increased in recent years as attackers use the latest technologies to execute attacks. Following are some of the top Cybersecurity Breaches:
Man-in-the-Middle Attack
This attack aims to steal personal information like account details, login credentials, and others. When an attacker gets between a conversation between a user and an application, it is known as Man-in-the-Middle (MITM) Attack. The attacker either eavesdrops on the conversation or impersonates one of the parties and makes it appear as a regular exchange of information.
Cybercriminals position themselves in the middle of a data transaction or online communication to carry out such attacks. Generally, sites that require authentication with a private and public key, such as banks and e-Commerce sites, are the targets of MITM attacks.
Denial-of-Service (DoS) Attacks
An attack in which the cyber-criminal aims to render a system useless for the users by disrupting the normal functioning of the device is known as DoS. In such attacks, the target machines are flooded with requests till it stops functioning. It results in the Denial-of-Service to the users. Usually, such an attack is carried out from a single computer system. The primary aim of such an attack is to deny services to the users and disrupt their functions and processes.
Phishing
It is a social engineering attack where the attacker steals users' data, such as passwords, social security numbers, etc. In this attack, the cyber-criminal appears to be from a trusted source and tricks the victim into opening malicious emails or text messages. Clicking on such links can lead to the installation of malware or the revealing of sensitive private information.
It is a widespread cyber-attack and can be highly dangerous because it is usually executed on government networks and bank websites as they contain sensitive information. Email and Spear phishing is the most common types of phishing scams.
Ransomware
It is malware designed to deny users access to files and data stored on their computers or other devices. The attacker encrypts the files to prevent access and demands a ransom from the users to gain access to the data.
Recently it has become a widespread and popular cyber-attack and caused significant damage to individuals and business organisations. These attackers are now also targeting hospitals and disrupting such organisations' ability to deliver effective healthcare services. Moreover, it has been observed that even when users pay the ransom, the attackers still do not share the decryption key. Instead, they demand more ransom.
Malware
It is described as intrusive software designed to damage and destroy computers and systems. It is a blanket term used for any software with malicious intent. Most online threats are classified as some form of malware. It can be in several states, such as viruses, worms, ransomware, spyware, and trojan horses.
Each malware has its methods of attack. They can range from stealthy to subtle. Providing remote attacker access to an infected machine, sending spam from the infected device to target users, and stealing sensitive data are some of the main objectives of malware.
Supply Chain Attacks
These are also known as Value-Chain or Third-Party Attacks. These happen when an attacker infiltrates users' systems through an outside partner or a member of the supply chain to access data. Such attacks are designed to exploit an organisation's and its vendors' trust. The attackers compromise the IT systems of one supply chain member and move up the ladder. This way, they exploit the trust and relationship between the supply chain partners to execute the attack and gain access to sensitive, valuable information.
Social Engineering Attacks
It is a manipulation technique that exploits human errors to give attackers access to sensitive private information. It is also termed 'human hacking' and focuses on attracting users into exposing their data, spreading malware infections, or giving access to restricted systems. These attacks are based on the processes used by people to think and act. Attackers focus on manipulating the target users to motivate them to take specific actions they otherwise would not have taken.
Understand the different types of cyber-attacks with the Cyber Security Risk Management course.
Top Cyber Security Breaches
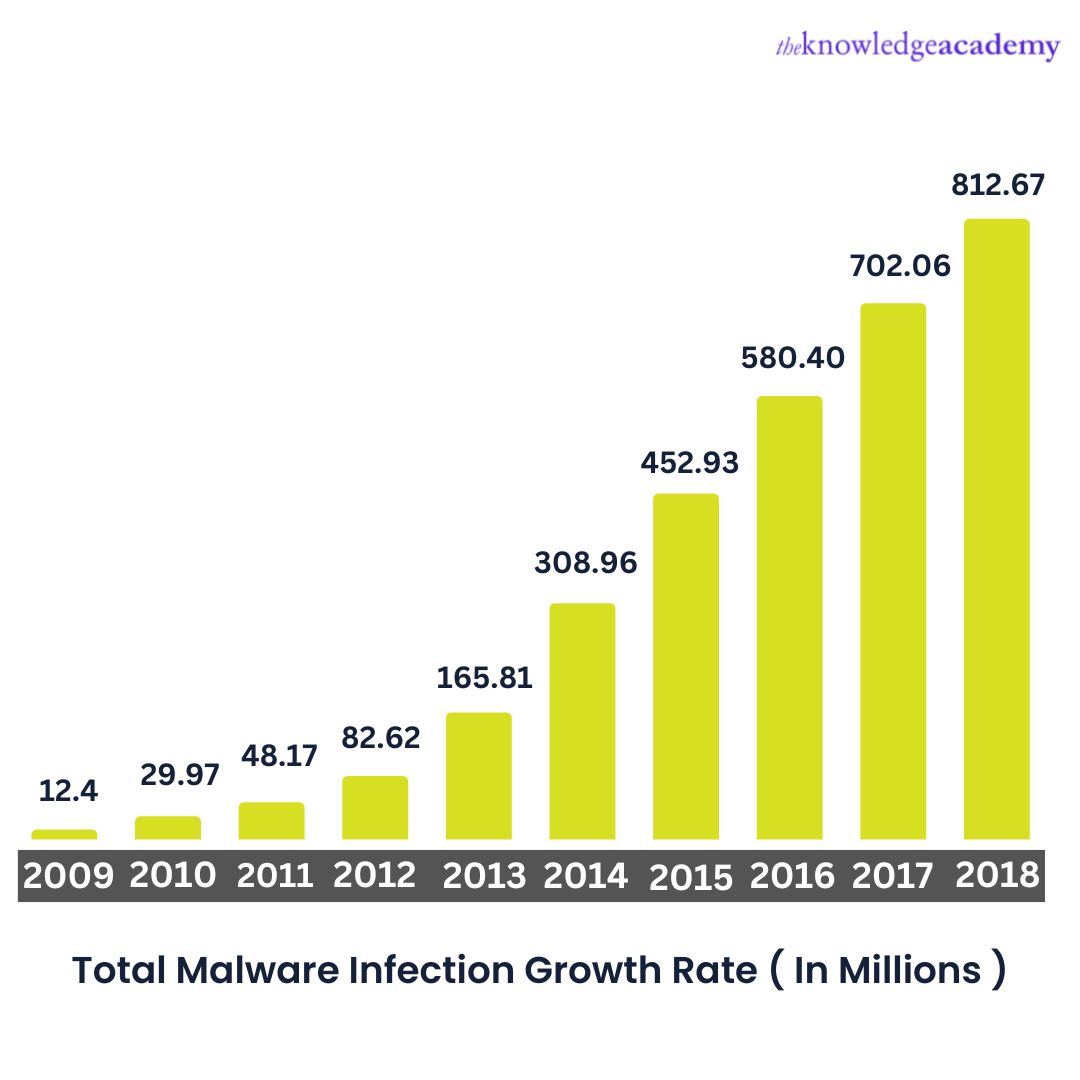
Cybersecurity Breaches have increased substantially in recent years. These have forced organisations to increase their budget for developing and maintaining the security of their networks and systems. Following are a few of the recent Cybersecurity Breaches.
Twitter data breach - In January 2023, data of over 200 million Twitter users were circulated among hackers in December 2022. The whole data acquired through the attack was published on BreachForums. The compromised data included email addresses, names, and usernames but did not include passwords and other sensitive data. Attackers exploited a vulnerability in the Application Programming Interface (API) to access Twitter's servers. The attack was executed in multiple ransomware attempts.
LinkedIn data breach - In June 2021, LinkedIn found data of more than 700 million users posted for sale on Dark Web forums. As a result of this attack, nearly 92% of the total user base of LinkedIn was affected. The data stolen by the attackers included email addresses, phone numbers, full names, geolocation records, and more.
SHEIN data breach - In October 2022, the fast fashion brand SHEIN was fined £1.5 million after failing to disclose a data breach that affected nearly 40 million users. The incident occurred in 2018 when a malicious third party gained unauthorised access to the company's payment systems.
The company's payment processor contacted the brand and disclosed that cyber criminals had infiltrated its payment systems and stolen credit card data. However, the company failed to take action and continued its operations as usual, compromising the security of the user’s data.
Want to become a pro at Cyber Security? Take our one-day Certified Cyber Security Professional (CCS-PRO) course.
How to prevent Cybersecurity Breaches?
From the above examples, it is clear that Cybersecurity Breaches are affecting businesses and people alike. Companies can access various resources and tools to prevent Cyber Security attacks and safeguard their data.
One of the fundamental ways to avoid a Cybersecurity breach is by using robust IT security management systems. Such a system should consist of endpoint security software, firewall management software, anti-viruses, and others.
These systems ensure that the data is well-protected and that the company does not fall victim to a security breach. Apart from this, businesses must also focus on hiring well-trained and experienced security professionals who can maintain the systems, detect a breach and take preventive actions.
Learn Forensic Investigation with Computer Forensics Foundation Training course.
Conclusion
Cybersecurity has become a fundamental aspect of the functioning of a business. Companies now spend millions on securing their systems to prevent becoming the victim of a cyber-attack. In this blog, we presented and discussed seven types of Cybersecurity Breaches. We also gave examples of a few recent security breaches.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 6th Sep 2024
Fri 20th Dec 2024







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


