We may not have the course you’re looking for. If you enquire or give us a call on +1 7204454674 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Nowadays, Technology and the Internet have become inseparable. These two have become essential pillars of an organisation and its strategy for success. If an organisation wants to expand its business, it is easier to do so using the power of the internet and technology. But at the same time, they also need to be wary of the current challenges in Cyber Space. Any organisation serious about its security must recognise Cyber Security Vulnerabilities.
According to Statista, almost 15 million records were exposed to Cyber threats in just the third quarter of 2022, about 37 per cent higher than the previous quarter. Cyber Security Vulnerabilities are often overlooked, and proper awareness can improve an organisation's security on a vast scale. Not only that, but it can also prevent and avoid any unnecessary loss to an organisation's reputation and finances.
In this blog, we will see the significance of Cyber Security Vulnerabilities and how to manage and safeguard your systems and network.
Table of Contents
1) What is a Vulnerability in Cyber Security?
2) Let's find out the causes of Vulnerabilities
3) Types of Cyber Security Vulnerabilities with Examples
4) Risks Associated with Vulnerabilities
5) Let’s Learn how to manage Vulnerability in Cyber Security
6) Conclusion
What is Vulnerability in Cyber Security?
Cyber Security Vulnerabilities are areas of weak points where Computer Systems and Networks are susceptible to attacks and threats. Vulnerability in Cyber Security means any weakness the attackers can use to gain access to your systems.
Cyber Security Vulnerabilities can act as a gateway or entry point for future cyber-attacks and intrusions. Hackers will constantly test out these areas of weakness and can exploit them if they see an opportunity.
Get a clear picture of Cyber Security and how it impacts businesses - sign up for our Cyber Security Awareness course today!
Let's find out the causes of Vulnerabilities
Vulnerabilities can be caused by anything like a missing software update to poor password management. Misconfigurations in software and hardware can also lead to Vulnerabilities. The other causes of vulnerabilities are the following:
a) Improper Password Management
Managing your passwords safely and securely is essential to an organisation's security. Leakage in the password can lead to several threats like exposure to Data. Attackers with malicious intent can use it to gain access and spy on your systems without your knowledge, and by the time you get aware of the incident, the damage is done.
b) Flaws and Glitches in the System
A system riddled with glitches and other technical flaws could lead to Vulnerable systems and can be exposed to attacks. To prevent this, report such flaws immediately to your supervisor or system administrator.
c) Bugs
Using software that contains bugs can slow down the work and lead to External attacks. Sometimes hackers deliberately alter software and implant bugs to hack the host system. To avoid this, always download software from reputed sources and ensure the Systems Administrator or your Supervisor authorises them.
d) Social Engineering
Hackers may target victims using Phishing emails and social media to trick them into revealing Sensitive Data. This type of attack comes under Social Engineering. It is partly due to human errors and could be caused by negligence & lack of awareness.
e) Other Familiar Threats
These threats could be Anything from using a malicious code or tool to attack the victim's systems and networks.
f) Internet threats
Apart from these, a simple activity of using the internet can lead to Vulnerability if you are not careful. Attackers can use malware like spyware to access the host system to obtain data. To prevent this, always clear cookies and caches, as well as your browsing history and avoid downloading tools and extensions from an unknown source.
Sign up for our Cyber Security Risk Management Course to learn about real threats impacting Cyber Security.
Types of Cyber Security Vulnerabilities with Examples
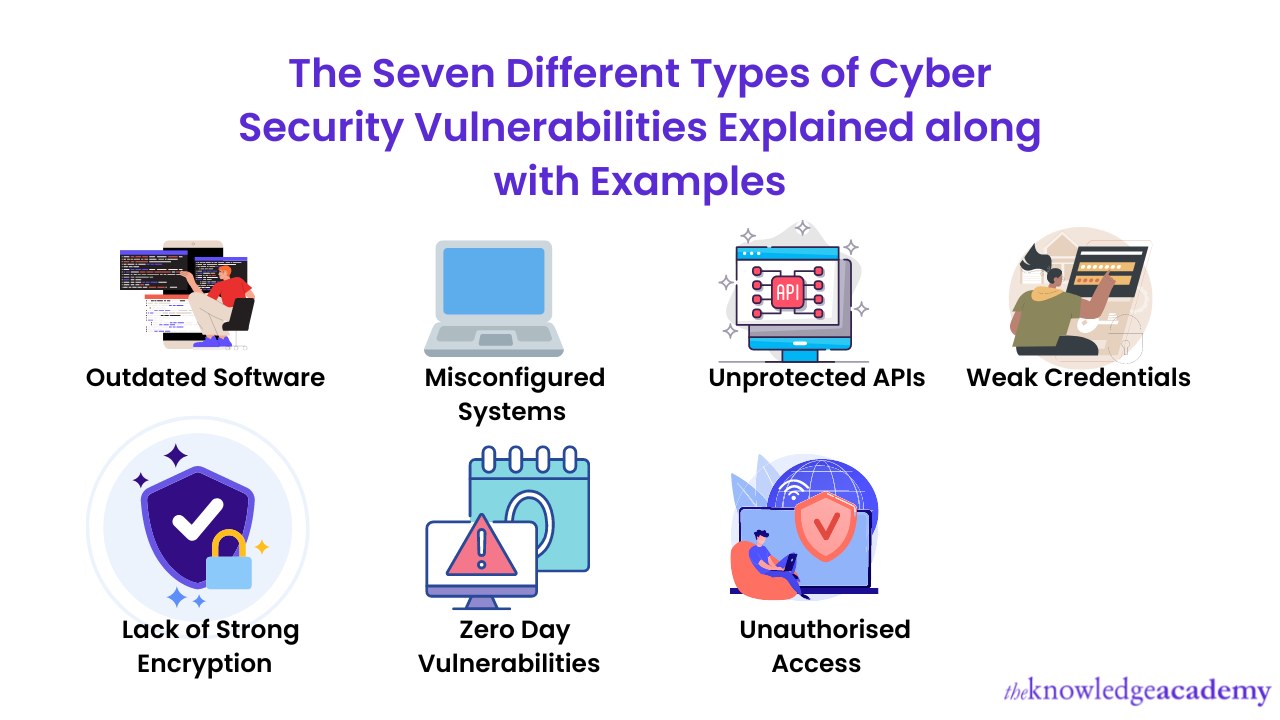
Let's look at the seven types of Cyber Security Vulnerabilities with examples.
a) Outdated software
A system that uses software that is not up to date can compromise the security of the host system and leave the entire network vulnerable. Attackers can use the victim's system as a base to launch further attacks on the other systems in the network.
Software Developers regularly release updates with new features and are far superior in dealing with the latest threats. But if a person uses outdated software even after the latest updates are released, it could lead to attacks.
To overcome this issue, have a schedule to regularly check for and update the software to the latest version.
Example: Using an out-of-date antivirus software or operating system.
b) Misconfigured Systems
If a system is not configured according to the organisation's security policy, that would also result in Vulnerabilities. And misconfiguration in network settings can open the door for Cyber Attacks and be hard to defend against. To avoid this, use the up-to-date drivers from your network devices and adopt a new security policy that is on par with the current threats.
Example: Using a system that doesn't contain the organisation's safety and monitoring tools.
c) Unprotected APIs
Unprotected APIs are one of the most common types of Vulnerability in Cyber security. APIs act like a bridge between applications and the internet. In an organisation, APIs are most likely used in a private network to secure the communication between the Applications and their components that require internet access.
Example: Sharing access to your cloud drives with unauthorised individuals or trying to access them in an unprotected public network can lead to Vulnerability.
d) Weak Credentials
People often use the same set of passwords for almost all applications and logins. This pattern of reusing the same passwords for everything can be very dangerous in the long run and could easily compromise the security and integrity of an organisation. Attackers can use spyware to launch attacks like “Brute Force Attack” to identify the passwords and other credentials of the victim quickly.
To avoid this issue, try using strong and unique passwords for every application. And make sure that these passwords don't have a pattern or clues. Most importantly, they should be meaningless and random to prevent such intrusions.
Example: Using a weak password like 1234, Abcde or using a password with a pattern like using Birthdays and names like James1956.
e) Lack of Strong Encryption
Although encryption can't prevent Hacking, it can slow down the attacking momentum. This is crucial as it can give you time to respond and take countermeasures. Encryption is like an added shield to your armour. Strong encryption can lead to stronger protection and act like a fortress against attacks.
Example: Try encrypting files using a password when transferring data. This option is available in simple file types like WinZip and WinRAR; many software is available for professional-level encryption.
f) Zero Day Vulnerabilities
A zero-day Vulnerability is a flaw or set of weaknesses uncovered by an attacker but is unknown to the software developer and the organisation that uses the software. Technically, this means that the software developer has 0 days to work on this issue to fix it. And, they can't work on the update as they're yet to discover the problem.
This Vulnerability is arguably one of the most severe security threats to an organisation. And it is impossible to protect against such attacks since only the attacker knows about the weakness. Using a sophisticated security solution can give protection against these attacks.
Example: Any attack that went unnoticed from a few days to several weeks until it's discovered can be considered a Zero-day Vulnerability.
g) Unauthorised Access
When an organisation gives its employees more access than necessary, it could also lead to a data breach. It can be prevented by limited but required access. There are many ways to do that; one way would be to use POLP (Principle of Least Privilege). POLP ensures that only people with authorisation have access to the systems and Data. Besides that, it also allows organisations to monitor effectively and gives them more control.
Example: Restricting access to install, modify or remove any software tool and only giving such access to System administrators or Supervisors.
Risks Associated with Vulnerabilities
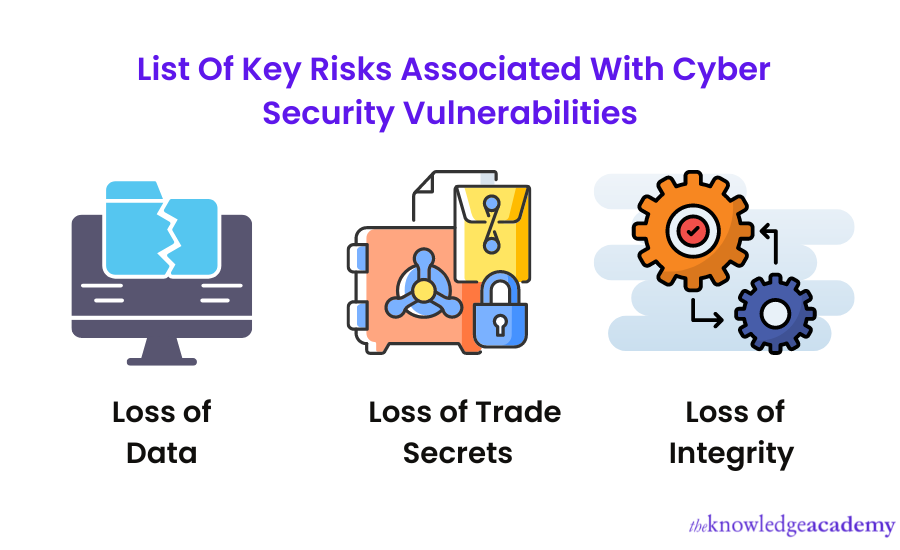
Vulnerability in Cyber Security could have severe consequences if they are not addressed immediately and could jeopardise an organisation's growth potential. Some of the risks associated with these Vulnerabilities are listed below:
a) Loss of Data:
Hackers can use techniques like SQL Injection, Spyware, Brute Force Attacks, and other methods to access a victim's system. Once an attacker gains access to an organisation's system, there is a high probability of their Data getting stolen. These could be anything from Internal Communication to sensitive Data containing Client information.
b) Loss of Trade Secrets
Trade secrets are arguably the most valuable information to a company, and once leaked outside, it could impact the value of their products and profitability.
c) Loss of Integrity
If an organisation has to announce that its systems have been compromised by an intrusion, clients could lose trust in them, and as a result, it would lose business.
Let’s Learn how to manage Vulnerability in Cyber Security
Now that you know the risks let's find out how to manage and safeguard our systems against these Vulnerabilities. The purpose of Vulnerability management is to identify, assess and prevent Vulnerabilities in the future.
1) Detect: The first step is to detect and identify the threat. Conduct regular scans and perform penetration tests
2) Verification: The next step is to reaffirm the threat and level of risk involved
3) Reduce or Minimise the Damage: Once the risk level is reaffirmed, try to minimise the damage by taking appropriate countermeasures
4) Safeguard: Safeguard your systems and devices from future attacks by regularly updating the software
Conclusion
From reading this blog, we hope you understand everything about Cyber Security Vulnerabilities, their types, the risks involved, and how to manage them. At the same time, you have also learned about the potential impacts they can cause if left unchecked.
If interested, check out our courses on Cyber Security Training and empower your knowledge base.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 6th Sep 2024
Fri 20th Dec 2024







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


