We may not have the course you’re looking for. If you enquire or give us a call on +1 7204454674 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

A Cyber Security Breach results from unauthorised access to data, applications, or networks, disrupting established security procedures. Such Breaches pose a significant threat to an organisation's reputation due to potential data loss.
Large-scale incidents, like the Yahoo data breaches in 2016, where 3 billion user accounts were exposed, underscore the severity of these breaches. The frequency of reported Security Breaches continues to rise, impacting millions daily. Thus, it is crucial to learn about these Breaches and prevent your organisation from any type of malicious attack.
Want to know how can you do that?Read this blog to understand and learn more about Cyber Security Breaches and how to reduce the chances of one in your organisation.
Table of Contents
1) What is a Cyber Security Breach?
2) Types of Security Breaches
3) How does a Cyber Security Breach happen?
4) Examples of Security Breaches
5) What to do if you experience a Cyber Security Breach?
6) How to protect your data against a Security Breach?
7) Conclusion
What is a Cyber-related Security Breach?
Now, let's first understand Cyber Security Breach definition. When an outsider gets illegal access to a company's secure systems and data, it indicates a security breach. To access restricted regions, cybercriminals or harmful software applications breach security protocols.
A Security Breach is an early-stage violation that can result in system damage and data loss. It refers to an attacker's successful attempt to obtain unauthorised access to a company's computer systems. Sensitive data theft, Information Technology (IT) system corruption or manipulation, malicious website property destruction and reputation-damaging behaviour are all breaches.
Moreover, Security Breaches have legal consequences. Corporations may be subject to fines or other penalties if laws are broken, and specific sensitive data is compromised.
Types of Security Breaches
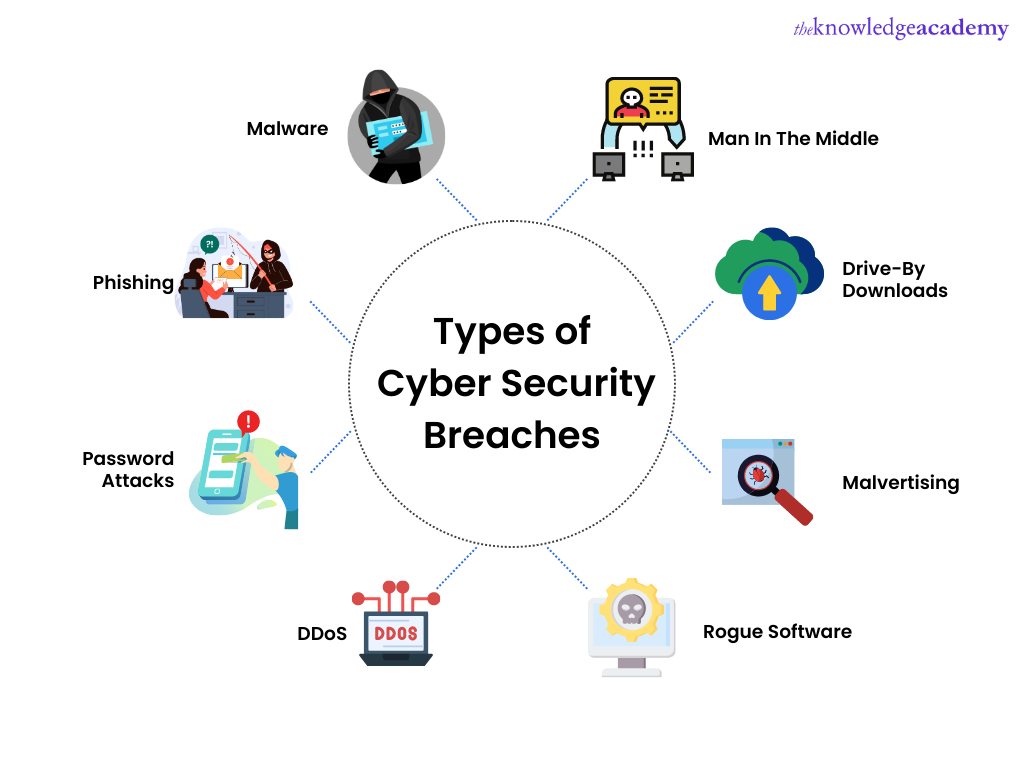
There are several types of security breaches based on how access to the system was gained. Some them include the following:
a) Exploits: Target software vulnerabilities, enabling unauthorised access or control over systems.
b) Malware, spyware, and viruses: infiltrate systems to damage, disrupt, or steal sensitive information.
c) Man-in-the-Middle (MitM): Attackers intercept communication between parties, allowing attackers to eavesdrop or manipulate data.
d) Social Engineering: Exploits human psychology, deceiving individuals into revealing sensitive information.
e) Password attacks: Involve unauthorized attempts to access systems by guessing or stealing login credentials.
f) Advanced Persistent Threats (APTs): Stealthy and prolonged attacks, aiming to compromise systems or data over an extended period, often orchestrated by skilled attackers.

How does a Cyber Security Breach happen?
Cyber Security Breaches represent multifaceted challenges, originating from diverse vectors that necessitate a comprehensive understanding:
a) Phishing attacks: Cybercriminals use deceptive strategies to induce users to interact with malicious links or attachments. This deceptive practice can result in the installation of malware or the theft of sensitive credentials, compromising overall security.
b) Malware: Insidious software infiltrates systems through various means, including phishing attacks, drive-by downloads, or infected removable media. Once embedded, malware can execute various malicious activities, from stealing data to spying on users or disrupting operational functionalities.
c) Zero-day attacks: These sophisticated attacks exploit software vulnerabilities that vendors are unaware of, posing a significant challenge due to the absence of available patches. Combating zero-day threats demands proactive and adaptive security measures.
d) Social engineering: This method involves manipulating individuals through pretexting, impersonation, or bribery to reveal sensitive information. Heightening awareness and imparting Cyber Security education are critical in thwarting social engineering attempts.
Insider threats: Breaches stemming from individuals with authorised access, intentional or accidental. Robust internal controls, employee education, and continuous monitoring mechanisms are essential to mitigate the risks associated with insider threats.
Examples of Security Breaches
A Security Breach at a large corporation always makes the news. Examples of Security Breaches include the following:
a) Equifax: In 2017, a website application bug cost the corporation 145 million Americans' personal information. This included their names, social security numbers, and license numbers. The attacks took place from May to July over three months, but the Security Breach was not disclosed until September.
b) Yahoo: A spear phishing email campaign led to the Yahoo security breach, which compromised over 3 billion user accounts. Names, phone numbers, security questions, and passwords with inadequate encryption were among the data that were disclosed.
Many of those passwords have found their way to the dark web, which serves as the foundation for databases of credentials that have been stolen and are currently exploited by attackers. The breach happened in 2013 and 2014; however, it wasn't until 2016 that it was found.
c) Facebook: In 2018, Facebook had internal technical issues that resulted in the loss of 29 million users' sensitive data. This security breach was one of the most embarrassing breaches as the accounts that were hacked, including the one belonging to the company's CEO, Mark Zuckerberg.
Learn about the various cyberattacks with our Cyber Security Risk Management Course – join today!
What to do if you experience a Cyber Security Breach?
To protect yourself you must take immediate action if you discover that your company has experienced a Cyber Security Breach, or your computer has been compromised. Keep in mind that a Security Breach on one account may indicate that other accounts are also vulnerable, mainly if you often conduct transactions across them or share passwords.
Further, notify any banks or other organisations you have accounts with if there is a possibility that a Breach may affect your financial information. Make sure all of your account passwords are changed. You should also update any PIN codes or security questions and answers linked to the account.
Moreover, you can also freeze your credit. This prevents identity theft and borrowing in your name using your data. Check your credit report to find out if someone is utilising your information to apply for debt.
Also, determine as precisely as possible which data may have been taken. That will help you gauge how serious the situation is. For example, you must take immediate action to protect your identity if tax information and social security numbers have been compromised. More important than just losing your credit card information is this.
After a data breach, don't immediately reply to inquiries from a corporation for personal information; this could be a Social Engineering scam. To find out if the requests are genuine, take some time to read the news, visit the company's website, or even give them a call at their customer service number.
Watch out for more forms of Social Engineering Attacks. For example, even without financial information, a hacker accessing a hotel's account might call guests to inquire about their most recent experiences.
After building a rapport of confidence, the criminal may, offer the customer a refund for the parking fees and request their card details so they may process the payment. If the call is persuasive, most clients wouldn't hesitate to provide those details. Take action against unrecognised accounts and watch for any new activity on your accounts.
Do you want to master Cyber Security? Try our Certified Cyber Security Professional (CCS-PRO) Course – join today!
How to protect your data against a Security Breach?
Here's how you can protect your data against a Cyber Security Breach:
1) Create secure passwords: It is certainly the best advice. Upper- and lowercase letters, digits, and symbols make a strong password. Therefore, it will be difficult for hackers to access your account. This is considered one of the most effective methods to protect your data.
2) For each account, use a separate password: If not, hackers will simultaneously access all of your accounts. As an example, they broke into your Facebook account. Additionally, your bank account uses the same password that you do. Therefore, they, too, can access it.
3) Don't leave accounts inactive; instead, close them: This lessens your exposure to a security breach. You might not be aware that a hacked account exists if you don't use it, and it could serve as a backdoor to your other accounts if you do.
4) Regularly update your passwords: One characteristic of many publicly disclosed security breaches is that they took place over a long time, with some not being disclosed for years. You run a lower risk of danger from unexpected data breaches if you regularly update your passwords.
5) Remote surveillance: Your network is continuously monitored by remote monitoring. You can collaborate with an IT services company to avoid hiring IT professionals full-time to check your systems.
6) Keeping only what is necessary: Track the data you store on your machines and periodically remove what is unnecessary. The number of locations where you keep sensitive information should be kept to a minimum, and you should keep track of where each location is.
7) Before disposal, destroy: Make sure anything containing sensitive information has been destroyed appropriately before discarding it. As an example, cross-cut paper files. Use software intended to completely erase data from devices like outdated phones, computers, or hard drives. The data is not entirely erased by just removing the files or reformatting.
8) Do a file backup: Some data breaches result in file encryption and a ransomware demand to decrypt the files and restore user access. In the case of a breach, your data will be protected if you have a second backup on a removable drive.
9) Protect physical data: Physical acts can result in data breaches, so it's crucial to protect all data, including physical files. Make sure that physical records are kept in a safe area with access limited to those employees who require it.
10) Educate employees with best practices: Employees should be well-versed in the websites that can endanger company systems, such as file-sharing portals. The same remains true for any mobile devices people use while working. You should encourage them to limit their work computers to business-related tasks and leave other activities to their home computers, mainly if they perform remote work.
11) Checking bank statements: You can stay secure by keeping an eye on your bank accounts and credit reports. Even years after the first data breach, stolen data may still reappear on the dark web. This may imply that an attempt at identity theft happens years after you've forgotten about the data leak that exposed that account.
12) Secure data: Ensure any confidential information you submit by email is encrypted before you send it. If using a Wi-Fi network, be careful to set up a private, exclusive network just for your team. You can mandate that employees not use Wi-Fi while handling the most sensitive data since cybercriminals might use it to intercept data.
Conclusion
Cyber Security Breaches might seem unavoidable as IT systems expand in size and complexity and become challenging to maintain. However, you can reduce the chances of a breach by staying aware of your risks and implementing preventive measures. Hope, this blog helps you understand what a breach in Cyber Security is along with Cyber Security breach examples and how to protect your data to prevent Cyber Attacks.
With the help of the Computer Forensics Foundation Training Course, learn forensic investigation.
Frequently Asked Questions

Phishing attacks stand out as one of the most common Cyber Security Breaches. These deceptive tactics involve tricking users into clicking on malicious links or opening infected attachments. By exploiting human vulnerabilities, attackers seek unauthorised access, install malware, or steal sensitive information, making phishing a prevalent and persistent Cyber Security threat.

The term breach in Cyber Security refers to the unauthorised access or compromise of a system, network, or data. It implies a violation of established security measures, allowing external parties to infiltrate and potentially exploit sensitive information. The use of breach underscores the intrusion's disruptive nature, indicating a breach in the protective barriers that should safeguard digital assets.

The Knowledge Academy's Knowledge Pass, a flexible prepaid voucher system, offers the freedom to enrol in courses over a 12-month period. Start your limitless learning adventure with us and embrace education that knows no bounds.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy offers various Cyber Security courses, including Certified Cyber Security Professional Training, Cyber Security Awareness Course, and Social Engineering Training. These courses cater to different skill levels, providing comprehensive insights into What is Cyber Resilience.
Our IT Security & Data Protection blogs cover a range of topics related to Cyber Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cyber Security skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 6th Sep 2024
Fri 20th Dec 2024







 Top Rated Course
Top Rated Course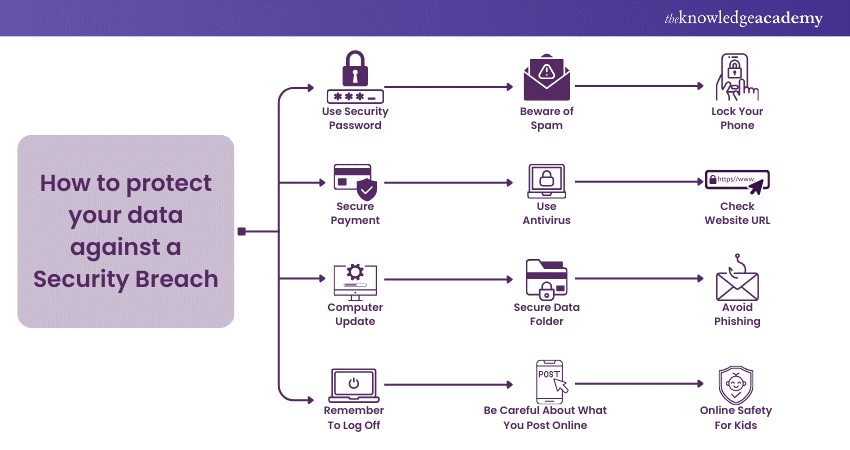



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


