We may not have the course you’re looking for. If you enquire or give us a call on +1 7204454674 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Are you interested in understanding the ins and outs of Cyber Security and the pressing issue of Spamming? Whether you're a budding Cyber Security enthusiast or a professional looking to deepen your expertise, understanding What is Spamming in Cyber Security is invaluable. Before going deep into the complexities of this subject, it's essential to grasp the fundamentals and the broader implications of Spamming in the realm of Cyber Security.
By thoroughly comprehending what Spamming entails in the context of cyber security, you can navigate this tricky landscape with clarity and equip yourself to combat digital threats effectively. Join us in unravelling the mysteries of Spamming in cyber security in this blog, where we'll explore What is Spamming in Cyber Security, types, motives, impact etc.
Table of Contents
1) What is Spamming?
2) Different types of Spam
3) The motives behind Spam
4) How does spam work?
5) Impact of Spam
6) Conclusion
What is Spamming?
In cyber security, Spamming means sending unwanted messages to many people, often for business or malicious reasons. You can use emails, texts, or instant messages to do this. Spamming can be used to share harmful software, take personal info, or trick people with scams and fake messages. It can also slow down or break networks and servers. It's important to be careful when you get emails or messages from people you don't know, and don't click on unknown links or share personal info.

Different types of Spam
Spam comes in different shapes and sizes, infiltrating various aspects of our digital lives. Here, we'll delve into the diverse types of spam that plague the online world, each tailored to disrupt or deceive in its own unique way.
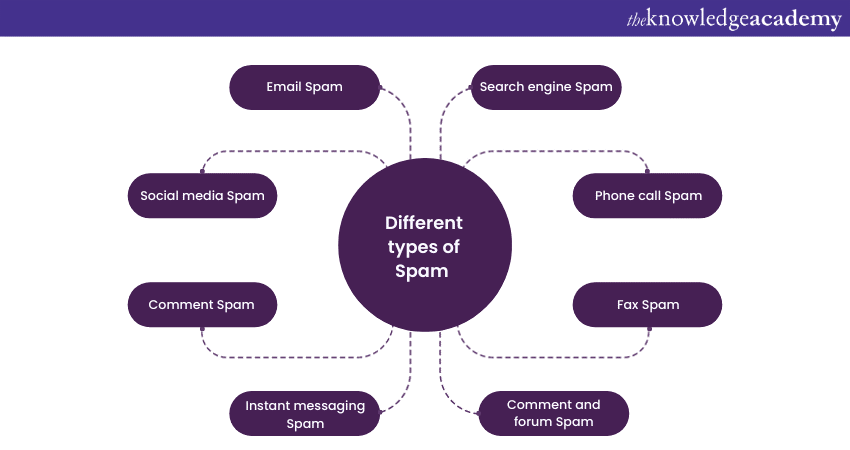
a) Email Spam: One of the most familiar forms of spam, email spam fills your inbox with unwanted messages. These messages often promote products and services or contain deceptive links. They can be annoying and, at times, harmful.
b) Social media Spam: On social platforms like Facebook, Twitter, and Instagram, social media spam rears its head in multiple forms. Fake accounts, fake likes and shares, or the spread of misleading content are common tactics. The goal is usually to either harvest user data or peddle scams.
c) Comment Spam: If you've ever run a blog or a website, you're likely no stranger to comment spam. Spammers leave irrelevant or malicious comments on your posts, often with links to their websites or fraudulent schemes, all in a bid to drive traffic and trick visitors.
d) Instant messaging Spam: Popular messaging apps like WhatsApp and Facebook Messenger aren't immune to spam. Unsolicited messages containing links to malware or phishing websites can disrupt your conversations and pose a security threat.
e) Search engine Spam: Spammers often manipulate search engine results to elevate their websites' visibility. This involves dubious tactics such as keyword stuffing and link farming, fooling search engines into ranking their sites higher.
f) Phone call Spam: While not digital in the traditional sense, phone call spam is a prevalent issue. Robocalls and unsolicited telemarketing calls inundate individuals with unwanted offers and scams, sometimes leading to financial losses.
g) Fax Spam: Yes, even the ageing technology of fax machines is not spared from spam. Fax spam involves the unsolicited sending of advertisements or solicitations via fax, resulting in wasted paper and ink.
h) Comment and forum Spam: Beyond blog comments, forums and online communities also face their share of spam. Posts and comments promoting products, services, or malicious links are common, detracting from genuine discussions.
i) Snail mail Spam: Traditional "snail mail" is not free from spam either. Spammy physical mail includes unsolicited advertisements, promotions, and deceptive offers.
j) Pop-up ads: While not as prevalent as email or social media spam, pop-up ads that forcefully appear on websites can be equally disruptive. They often promote products or contain deceptive content.
k) Blog comment Spam: Blogs frequently attract comment spam, where spammers use automated tools to post irrelevant or promotional comments with links to their websites. The aim is to improve their websites' search engine rankings.
The motives behind spam
Spammers typically have several nefarious objectives, which are discussed below:
Malware distribution
One of the primary motives for spam is to distribute malware. Malicious software like viruses, ransomware, and Trojans can be hidden in email attachments or concealed within the links shared through spam messages. When unsuspecting recipients click on these elements, their devices get infected, giving cybercriminals control over their systems.
Phishing attacks
Phishing is a technique used in spam to trick individuals into revealing sensitive information, such as login credentials, credit card details, or personal identification. These fraudulent messages often impersonate trusted entities, like banks or reputable organisations, creating a sense of urgency to lure recipients into divulging their data.
Botnets
Spammers frequently aim to grow their botnets through spam campaigns. A botnet is a network of compromised devices which can be used for various malicious purposes. These include launching Distributed Denial of Service (DDoS) attacks to flood websites and services, disseminating spam or malware, or even mining cryptocurrencies.
Blackhat SEO
Blackhat Search Engine Optimisation (SEO) is another motive behind spam. In this context, spammers manipulate search engine rankings by using tactics such as keyword stuffing, content duplication, or link farming. The goal is to deceive search engines and artificially boost the visibility of fraudulent or malicious websites, making it more likely for users to encounter them during online searches.
Data harvesting
Many spammers are in the business of collecting data. They're after personal information like email addresses, phone numbers, and social media profiles. This data can be sold on the black market or used for targeted spam campaigns, increasing the likelihood of success in their malicious endeavours.
Promoting scams and fraudulent schemes
Some spam is more straightforward in its intent, aiming to promote scams or fraudulent schemes. These messages often promise unrealistic financial gains, job opportunities, or attractive offers, encouraging recipients to part with their money or personal information. Common examples include advance-fee fraud and pyramid schemes.
Disruptive attacks
While not always financially motivated, some spam is designed to overload networks and servers, causing them to crash. This is often seen in the form of email or DDoS (Distributed Denial of Service) attacks. The goal here is to create chaos, hinder communication, or render online services unusable.
Advertising and marketing
In a more legitimate context, some spam is motivated by advertising and marketing. While the methods may still be unsolicited, the spammers are looking to promote products or services. This might include everything from pharmaceuticals and online casinos to weight loss products.
Enhance your cyber security knowledge and safeguard your digital world. Sign up for our Cyber Security Awareness Course now!
How does spam work?
Spam in Cyber Security is fraudulent, but it's important to understand how it operates. Here's a straightforward explanation of how spam works:
a) Gathering target information: Spammers start by collecting a large list of email addresses, phone numbers, or other contact details. These lists can be obtained from various sources, including data breaches, publicly available directories, or by using automated tools to scrape the internet.
b) Creating Spam messages: Next, they create the spam messages. These messages can be emails, text messages, or comments on websites. They may promote products and services or contain deceptive links.
c) Sending messages in bulk: To reach as many people as possible, spammers use automated software or tools to send the same message to a large number of recipients. They can send thousands or even millions of messages at once.
d) Avoiding detection: Spammers often try to avoid being caught. They may use techniques like hiding their identity by using fake sender information or disguising their message to look legitimate.
e) Tricking recipients: The spam messages are designed to get recipients to take action. This could be clicking on links, opening attachments, or providing personal information. For example, a spam email might claim you've won a prize and ask for your credit card details.
f) Causing disruption or harm: Depending on their motives, spammers may aim to disrupt services, steal personal information, or spread malware. Some just want to promote products or services. In more malicious cases, they want to harm individuals or organisations.
g) Evading countermeasures: As countermeasures like spam filters are improved over time, spammers adapt. They use tricks like changing the content of their messages or the way they send them to keep their spam from being blocked.
Impact of Spam
The impact of Spam in Cyber Security is far-reaching, affecting your finances, trustworthiness, legal standing, personal security, and even the functionality of online platforms. That's why it's essential to be cautious and vigilant when dealing with unsolicited messages. Spam can have many real-life consequences that are discussed below:
a) Financial losses: Sometimes, spam can trick you into spending money on things that don't exist or aren't what they claim to be. You can lose your hard-earned cash to scams.
b) Reputation damage: If you fall for a spam message, it can damage your reputation. People may not trust you if they know you've been fooled by spam or if your email or social media account is used to send spam to others.
c) Legal trouble: Spamming is often against the law. If you're caught sending spam, you can face fines, lawsuits, or even jail time. Businesses that send spam can be fined heavily.
d) Data breaches: Spam is often the first step in a data breach. If a spammer gets into your computer or a company's network, they can steal sensitive information, like your personal data or even your credit card details.
e) Overloaded systems: Spam can overwhelm email servers and websites, causing them to slow down or crash. This can disrupt work, communication, and online services.
Secure your digital assets with a comprehensive Cyber Security Risk Management Course. Sign up today!
How to protect yourself from Spam?
Through the implementation of the protective measures given below, you can significantly reduce your exposure to spam and its potential risks. Being vigilant and informed about common spam tactics is your best defence against Spam attacks.
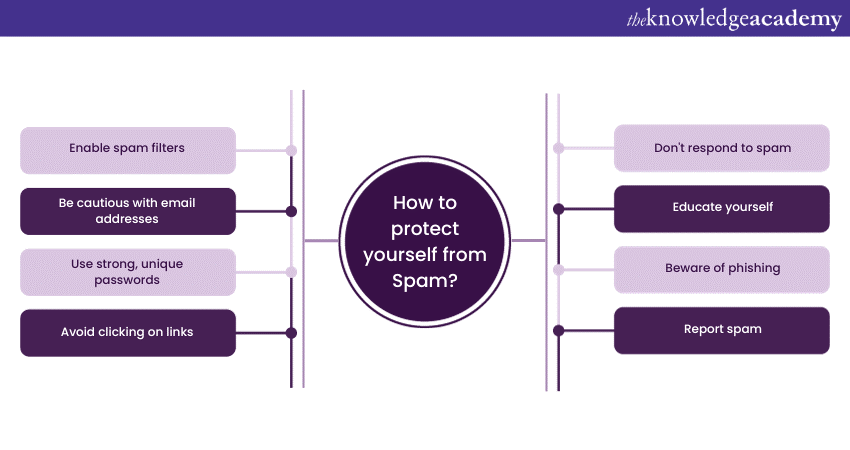
a) Enable spam filters: Most email providers and messaging apps have built-in spam filters. Make sure they're active. These filters automatically divert suspicious messages into a separate spam folder, keeping your main inbox clean.
b) Be cautious with email addresses: Avoid sharing your email address on public forums or untrusted websites. Spammers often scrape the internet for email addresses, so keep yours as private as possible.
c) Use strong, unique passwords: A strong, unique password for your email and online accounts can prevent unauthorised access and reduce the chances of spam. Consider using a password manager to generate and store secure passwords.
d) Avoid clicking on links: Don't click on links or download attachments from unknown senders or suspicious emails. Double-check the sender's address and content for any red flags, even if a message looks legitimate.
e) Don't respond to spam: Engaging with spam messages, even to unsubscribe, can confirm to spammers that your email address is active. It's best to delete these messages without any response.
f) Educate yourself: Learn to recognise common spam tactics. Be wary of unsolicited offers, requests for personal information, and generic greetings. Watch out for poor grammar, misspellings, and unusual sender addresses.
g) Beware of phishing: Spam is often used for phishing. Be cautious of emails or messages asking for personal or financial information. Verify the sender's identity through trusted means before sharing any sensitive data.
h) Report spam: Most email services and social media platforms provide options to report spam. Use this feature to help these platforms improve their filtering and to alert them to new spam trends.
i) Use anti-spam software: Consider using third-party anti-spam software or security suites. These tools can provide an additional layer of protection against spam and other online threats.
j) Check website links: Hover over website links to see where they lead before clicking. Make sure the destination URL matches the website's content, especially in emails.
Conclusion
Understanding "What is Spamming in Cyber Security?" is a vital step in safeguarding your digital presence and the integrity of online ecosystems. Implementing practical measures, such as enabling spam filters, practising caution with email addresses, and staying informed about evolving spam tactics, empowers you to use the digital space with confidence. With respect to Cyber Security, awareness and proactive measures are your strongest allies against the persistence of Spam.
Improve your Cyber Security skills with our courses on Cyber Security Training. Join today!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 6th Sep 2024
Fri 20th Dec 2024







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


