We may not have the course you’re looking for. If you enquire or give us a call on +1 7204454674 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

The rising advancements in technology are making hackers even savvier. Hackers now find it easy to break security barriers and carry out more attacks. Phishing is one of the most popular cyber-attacks carried out by cybercriminals.
The number of Phishing attacks per second has gone up to 74% since the last year. In case of a Phishing attack, cybercriminals use technology to steal victims' personal or credit card details. If you want to learn more about Phishing, read on.
Table of Contents
1) What is Phishing?
2) What is the objective of Phishing?
3) Let’s understand how Phishing works
4) Types of Phishing Attacks
5) How to detect the signs of Cyber Security Phishing Attacks?
6) How to minimise the risks of Phishing Attacks in your organisation?
7) Conclusion
What is Phishing?

Phishing is a cybersecurity attack carried out by malicious actors or cyber criminals. Here, malicious actors deceive users by sending messages using the address of a trusted entity or person. Phishing messages target users and allure them to click on malicious links, install malicious files, or provide sensitive information like access credentials.
Phishing is one of the most popular forms of social engineering attacks. It aims to trick or manipulate computer users. Social engineering attacks such as Phishing can be combined with severe threats like network attacks, code injection, and malware.
Become familiar with cyber security by choosing one of our courses on Cyber Security Training!
What is the objective of Phishing?
The two main objectives of Phishing are as follows:
Collect sensitive data
Cybercriminals send several suspicious emails to computer users every day. These emails aim to steal the login credentials of users. For example, some Phishing scammers send several emails to bank account holders. These emails appear similar to the ones sent from an official bank ID.
The objective is to trick users into opening the email and clicking on the link. Once the user has entered the login credentials, such as user ID and password, into the webpage, their data can be accessed by the phisher. Consequently, the phisher can access the bank account of users.
Download Malware
Phishers send emails with infected files attached to them. Whenever the links of these infected files are opened, the ransomware or malware will be downloaded on their system.
Learn how to minimise the risks related to cyber security. Register for our Cyber Security Risk Management course now!
Let’s understand how Phishing works
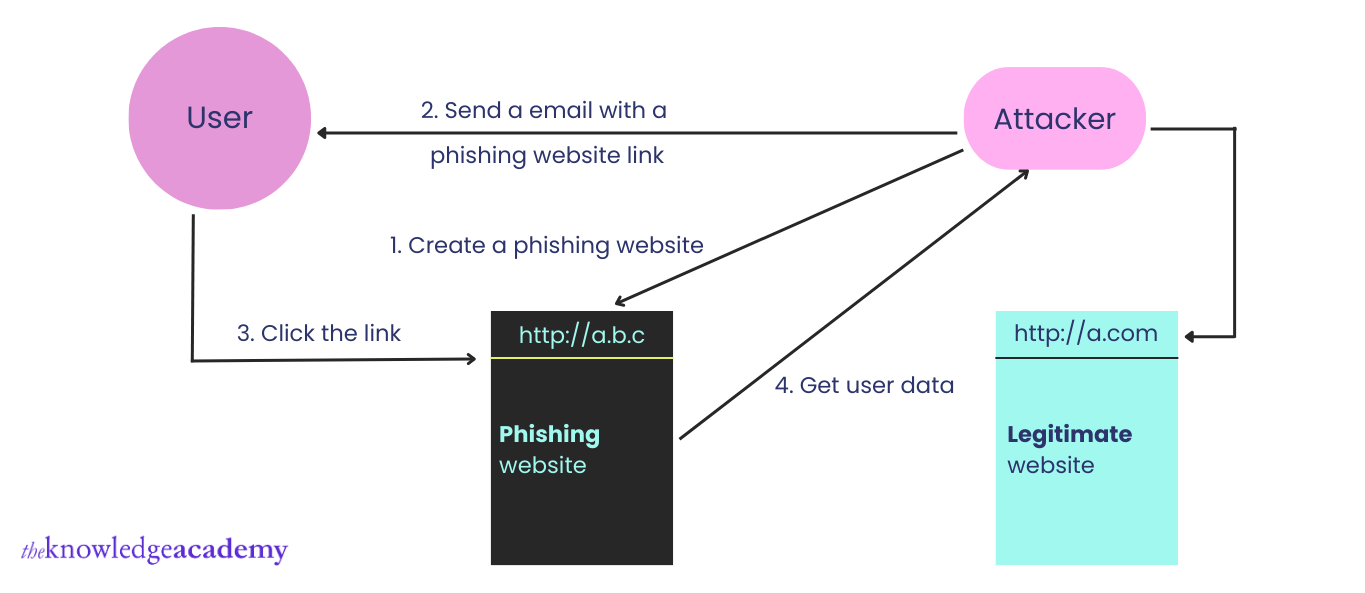
A Phishing attack is carried out through an email, social media post, or a message sent via any other mode of electronic media. A Phisher uses public resources such as social networks to gather personal information and the work experience of the victims.
Besides, the phishers use these sources to collect information like email addresses, job titles, and victims' names. Next, phishers can use such information to compose fake messages. Eventually, these emails are sent to the users through an organisation's fake address or a genuine person's contact number.
These emails include links or attachments that can direct users to malicious websites. Attackers create fake websites that look similar to the ones owned by trusted entities such as universities, workplaces, or banks. Attackers access these websites to gather confidential data such as payment information, passwords, and usernames.
However, users can identify a phishing email and avoid clicking on the link. Some phishing emails use fonts, layouts, and logos, improperly. Also, users can identify these emails due to their low-quality content.
However, several cybercriminals are learning ways to create genuine-looking messages. Cybercriminals also deceive users by using marketing strategies to test the effectiveness of their messages and emails.
Learn how to combat cyber security threats by taking up our Computer Forensics Foundation Training today!
Types of Phishing Attacks
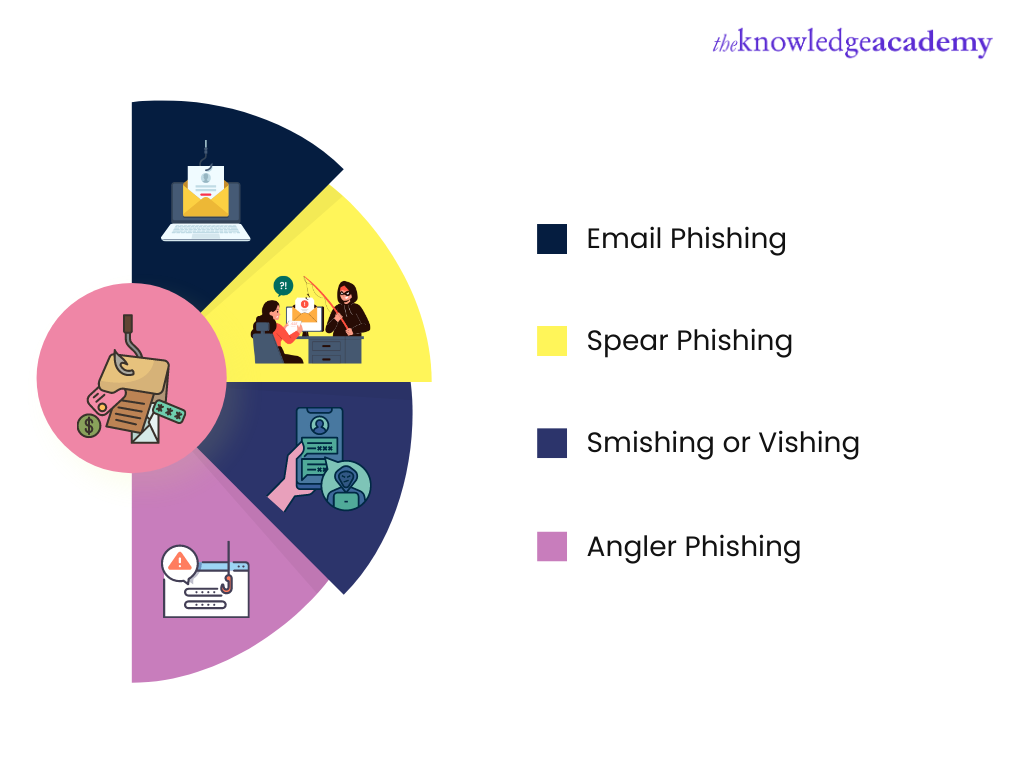
The common types of Phishing attacks are as follows:
Email Phishing
Phishing attacks are carried out by sending an email. Attackers create fake domain names that look like the name of real organisations. Next, they send more than thousands of requests to Gmail users.
Attackers register fake domain names by replacing or adding characters. For example, they can replace the domain name axis.com with axis-bank.com. Several Phishing emails are written with a threat or an urgency. It can prompt the user to click on the link without verifying its authenticity or source. The aim of email Phishing are as follows:
a) Trick the user into clicking a malicious link that will install malware on the system or device.
b) Trick the user into clicking on the fake website’s link and enter personal information.
c) Trick the user into clicking the “reply” button and send personal data.
Spear Phishing
Spear Phishing attacks only a specific group of email receivers. Here, attackers sent malicious emails to victims who had already provided the following information to them mistakenly:
a) Name
b) Name of the organisation
c) Job profile
d) Email address
e) Contact details of their family members or trusted colleagues
Attackers use such information to force the victims to perform certain activities and tasks like transferring funds.
Smishing or Vishing
Smishing is a type of Phishing attack that is carried out with the help of a phone. Here, the attacker sends fake SMS messages. At the same time, vishing attacks are carried out through phone conversations. Vishing doesn’t involve any written communication like other Phishing attacks.
During these conversations, an attacker is disguised as a scam investigator working in a bank or a credit card company. The attacker informs the victims that their bank accounts are being misused. Next, the victims are forced to reveal their credit card information or transfer their money to the criminal’s account.
Angler Phishing
Angler Phishing attacks are carried out with the help of social media accounts. Here, the attacker uses a fake social media account similar to any other reputed organisation’s social media account. Besides, the profile picture of this account is identical to the actual organisation’s social media account.
How to detect the signs of Cyber Security Phishing attacks?
An organisation can detect Phishing signs by following the below-mentioned points:
A sense of threat or urgency
Emails that include harmful or threatening content can be fake. Besides, emails that demand quick action from users or encourage users to click on a specific link should be deleted immediately.
Message style
Messages with numerous grammatical errors or inappropriate use of language indicate a Phishing attack. For example, a message from your colleague written in an amiable tone indicates a Phishing attack. Similarly, if a message from your close friend uses a formal style, it might be suspicious.
Unusual requests
Emails that force you to perform an unusual activity can involve a malicious sender. For example, if you’re asked to install a specific software your organisation isn’t familiar with, it indicates a cybercriminal sent the email.
Linguistic mistakes
Phishing emails consist of several basic grammatical errors or spelling mistakes. Numerous companies are eliminating these issues by allowing email senders to check to spell automatically. Thus, emails that include grammatical or spelling mistakes should be considered fake as they don’t originate from an authentic address.
Inconsistent web addresses
One of the easiest ways to discover potential phishing attacks is to search for mismatched domain names, links, email addresses, etc.
Request for payment information, personal details, or user credentials
Several Phishing emails include fake login pages created by attackers. However, these emails look official. A fake login page contains a login box where users enter their email and provide sensitive financial information. Users who expect an email should refrain from clicking on its link or entering login credentials.

How to minimise the risks of Phishing attacks in your organisation?
Organisations can follow a few steps to minimise the risks related to Phishing attacks:
Train their employees
It is essential to impart training to your employees frequently. As a result, it will help your employees to understand how Phishing is done. Your employees will also be able to identify any Phishing signs. Eventually, it will enable them to report any suspicious activities to the IT Team.
Organisations should help employees to identify trust badges and security stickers used by antivirus or Cyber Security companies. The employees should interact only with websites with stickers or trust badges. Trust badges and security stickers indicate a website is concerned about its safety and isn’t malicious or fake.
Implement email security solutions
Organisations should use modern email filtering solutions. An email filtering solution offers protection against malware and malicious links attached with emails. These links help to detect emails that include malicious attachments, links, inappropriate language, and spam content as it indicates phishing attacks.
Additionally, email security solutions block suspicious emails automatically. Besides, these emails implement sandboxing technology to filter out email that consist of malicious code.
Frequent Phishing attack tests
Phishing tests help security teams to measure the effectiveness of a security awareness training program. It also helps users to determine the source and nature of the attack.
Endpoint protection and monitoring
Endpoint is a physical device that facilitates the exchange of information between different computer networks. The organisation's use of numerous personal devices and cloud-based services is introducing several new endpoints.
However, these endpoints need to be appropriately secured. So, security teams should identify endpoints that are vulnerable to attacks beforehand. Security teams should monitor endpoints regularly to find out security threats. Consequently, they should implement a security solution on compromised devices.
Limiting user access to high-value data and systems
The objective of the phishing method is to trick a human computer operator. Primarily, privileged user accounts are targeted by cybercriminals. Organisations can encrypt their data and systems to prevent the leakage of sensitive data.
Conclusion
The complexity of Phishing attacks is increasing. Most cybercriminals are tricking systems and internet users into clicking on unknown and misleading links. They aim to obtain sensitive information from them or steal a large amount of money.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 6th Sep 2024
Fri 20th Dec 2024







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


