Get a custom course package
We may not have any package deals available including this course. If you enquire or give us a call on +1 7204454674 and speak to our training experts, we should be able to help you with your requirements.
Module 1: Introduction to ISO 27002
Module 2: Scope, Terms and Definitions
Module 3: Structure of ISO 27002 Standard
Module 4: Risk Assessment and Treatment
Module 5: Audit Plan and Process
Module 6: Internal Auditor
Module 7: ISMS Audit
Module 8: Cybersecurity Auditing
Module 9: Information Security Audit
Module 10: Information Security in Project Management
Module 11: Components of Information Security
Module 12: Information Security Risk Management (ISRM)
Module 13: Control and Compliance
Module 14: Management Responsibilities
Module 15: Competence and Evaluation of Auditors
Module 16: Lead Auditor
Module 17: Conformity Assessment
Module 18: Themes and Controls
Module 19: Organisational Controls
Module 20: People Controls
Module 21: Physical Controls
Module 22: Technological Controls


The ISO 27002 Lead Auditor Course is meticulously designed to provide participants with the skills and knowledge to conduct comprehensive external audits on Information Security Management Systems based on the ISO 27002 Standard. The following professionals would especially benefit from attending this course:
There are no formal prerequisites for attending this ISO 27002 Lead Auditor Course.
In an increasingly digital world, understanding and implementing robust Information Security practices are paramount for organisations. This course delves into the intricacies of ISO 27002, offering participants a comprehensive view of Information Security Management.
Professionals aspiring to master the ISO 27002 Lead Auditor Training are typically those responsible for overseeing Information Security within their organisations. This includes IT Managers, Security Officers, and Compliance Professionals. Acquiring expertise in this area is crucial for maintaining the integrity and confidentiality of sensitive information, ensuring compliance with regulatory requirements, and safeguarding against cyber threats.
The 5-day training by the Knowledge Academy is designed to equip delegates with the essential skills to conduct effective audits in accordance with ISO 27002 standards. This course not only covers the theoretical aspects but also provides practical insights and tools. Delegates will gain the knowledge needed to assess and enhance Information Security systems, ultimately leading to successful ISO 27002 audits.
Course Objectives
Upon completion, delegates will possess the knowledge and skills necessary to conduct ISO 27002 audits with confidence, ensuring the robustness of Information Security Management Systems in accordance with industry best practices.




To achieve the ISO 27002 Lead Auditor Training, candidates will need to sit for an examination. The exam format is as follows:


Why choose us
Experience live, interactive learning from home with The Knowledge Academy's Online Instructor-led ISO 27002 Lead Auditor Training. Engage directly with expert instructors, mirroring the classroom schedule for a comprehensive learning journey. Enjoy the convenience of virtual learning without compromising on the quality of interaction.
Unlock your potential with The Knowledge Academy's ISO 27002 Lead Auditor Training, accessible anytime, anywhere on any device. Enjoy 90 days of online course access, extendable upon request, and benefit from the support of our expert trainers. Elevate your skills at your own pace with our Online Self-paced sessions.
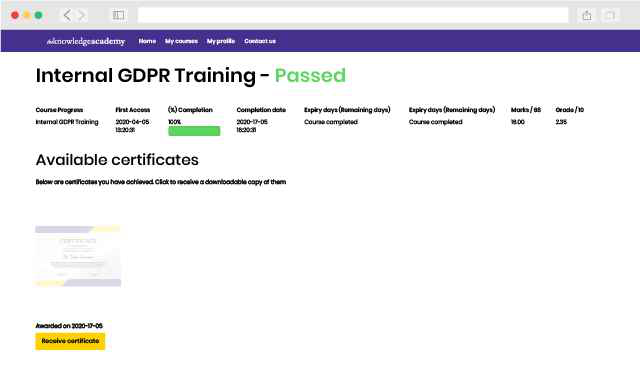
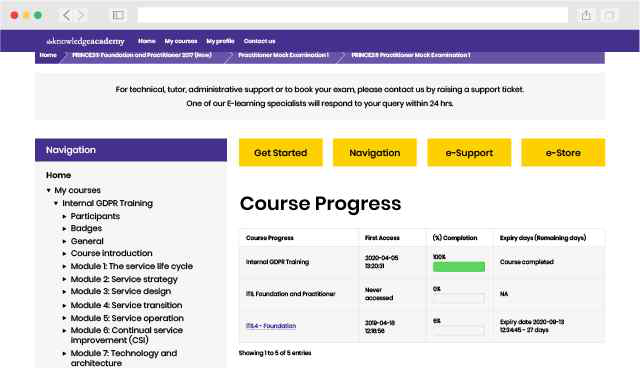
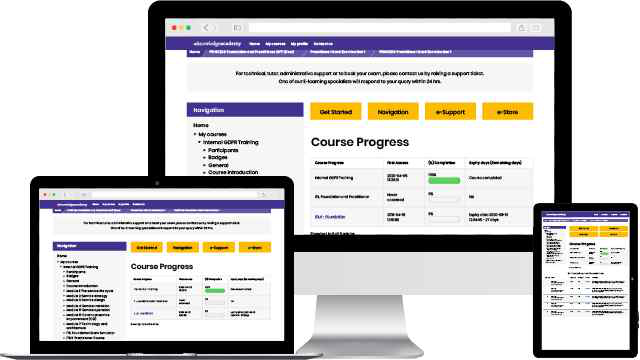
There hasn't been any questions asked about this Topic


You won't find better value in the marketplace. If you do find a lower price, we will beat it.

Flexible delivery methods are available depending on your learning style.

Resources are included for a comprehensive learning experience.




"Really good course and well organised. Trainer was great with a sense of humour - his experience allowed a free flowing course, structured to help you gain as much information & relevant experience whilst helping prepare you for the exam"
Joshua Davies, Thames Water



 Atlanta
Atlanta New York
New York Houston
Houston Dallas
Dallas Denver
Denver Seattle
Seattle Los Angeles
Los Angeles Chicago
Chicago San Francisco
San Francisco Philadelphia
Philadelphia San Diego
San Diego Phoenix
Phoenix Boston
Boston Austin
Austin Detroit
Detroit San Jose
San Jose Tampa
Tampa Colorado Springs
Colorado Springs Portland
Portland Sacramento
Sacramento Minneapolis
Minneapolis San Antonio
San Antonio Irvine
Irvine Las Vegas
Las Vegas Miami
Miami Bellevue
Bellevue Pittsburgh
Pittsburgh Baltimore
Baltimore Fairfax
Fairfax Orlando
Orlando Raleigh
Raleigh Salt Lake City
Salt Lake City Columbus
Columbus Oklahoma City
Oklahoma City Nashville
Nashville Charleston
Charleston Columbia
Columbia Cleveland
Cleveland Cincinnati
Cincinnati Memphis
Memphis Richmond
Richmond Virginia Beach
Virginia Beach Louisville
Louisville Fort Lauderdale
Fort Lauderdale Indianapolis
Indianapolis Des Moines
Des Moines Grand Rapids
Grand Rapids New Orleans
New Orleans Wichita
Wichita Charlotte
Charlotte Hartford
Hartford New Jersey
New Jersey Anchorage
Anchorage Omaha
Omaha Honolulu
Honolulu Albuquerque
Albuquerque Baton Rouge
Baton Rouge Iowa City
Iowa City Albany, NY
Albany, NY Boise
Boise Milwaukee
Milwaukee Tucson
Tucson Kansas City
Kansas City St Louis
St Louis Jacksonville
Jacksonville
 Back to course information
Back to course information
We may not have any package deals available including this course. If you enquire or give us a call on +1 7204454674 and speak to our training experts, we should be able to help you with your requirements.
 If you miss out, enquire to get yourself on the waiting list for the next day!
If you miss out, enquire to get yourself on the waiting list for the next day!

close


Press esc to close

close
Fill out your contact details below and our training experts will be in touch.



Back to Course Information