We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
In today's interconnected world, the need for robust Ethical Hacking and Cyber Security practices has become increasingly vital. Both Cyber Security and Ethical Hacking are crucial in protecting our digital landscape from malicious activities. While they share a common goal of securing computer systems and networks, there are fundamental differences between these two domains.
If you wish to understand a detailed comparison of Ethical Hacking and Cyber Security, including their roles, this blog is just for you. Keep reading to learn the key distinction between these crucial practices.
Table of Contents
1) What is Ethical Hacking?
2) Roles of Ethical Hacking
3) What is Cyber Security?
4) Roles of Cyber Security
5) What is the difference between Ethical Hacking and Cyber Security?
6) Conclusion
What is Ethical Hacking?
Ethical Hacking or white-hat hacking is a process of the intentional Hacking of computersystems, networks, or applications by security experts. These professional, Ethical Hackers, who are also called white hats, are authorised to find the weaknesses and the possible entrance points for the black hats.
Ethical Hackers are allowed to hack the systems, which makes their actions legal and for the purpose of security improvement.
Roles of Ethical Hacking
Ethical Hacking plays a major role in the security and integrity of Information Systems. Here are the key roles of Ethical Hackers:
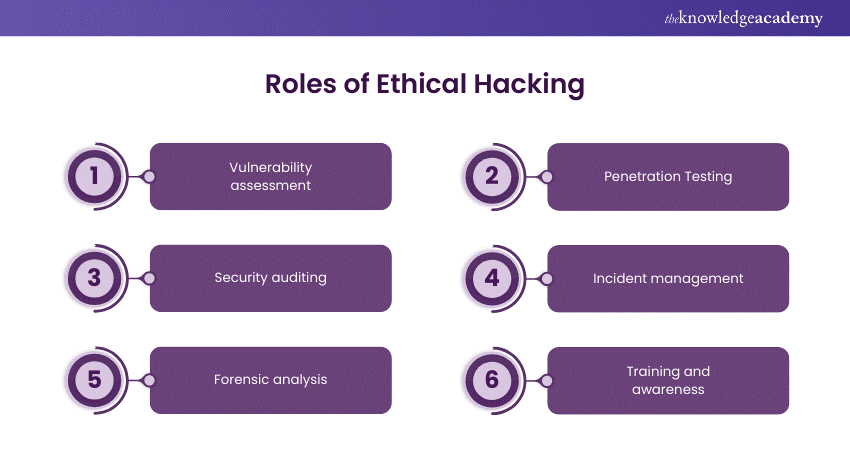
a) Vulnerability assessment: Ethical Hackers carry out assessments to find out which systems, networks, and applications are vulnerable. This means the process of detecting the weak spots which include the software that is outdated, the faulty configurations, and the vulnerability to the malware attacks.
b) Penetration Testing: While vulnerability assessments find the possible security weaknesses, Penetration Testing is the one that uses these weaknesses to evaluate the possible breaches. Through this, the organisations are able to find out the real effectiveness of their current security systems in the real world.
c) Security auditing: Ethical Hackers are engaged in a thorough examination of the existing security policies and procedures. This involves the check of the compliance to the required standards and rules to ensure that the safety procedures are current.
d) Incident management: If there is a security breach, Ethical Hackers deal with the problem by looking into it and thus, the situation is prevented from happening again.
e) Forensic analysis: After the breach, Ethical Hackers usually carry out forensic analysis, which includes the cause and the method of the attack. This study is significant for the knowledge of the causes of the breaches and the ways to prevent them in the future.
f) Training and awareness: Ethical Hackers are not only responsible for the preservation of the company but they also train the employees the best security practices. They also inform them about the newest Cyber Security risks and how to prevent them.
What is Cyber Security?
Cyber Security is the process of protecting computer systems, networks, devices, and data from illegal access, attacks, or damage. It is about the various methods and tactics that are used to protect information and infrastructure from the dangers that are present in the digital world.
This field is essential not only for individual privacy and security but also for the operational integrity of businesses and national infrastructure security.
Roles of Cyber Security
Cyber Security professionals play diverse roles, each critical to maintaining the digital fortress of an organisation:
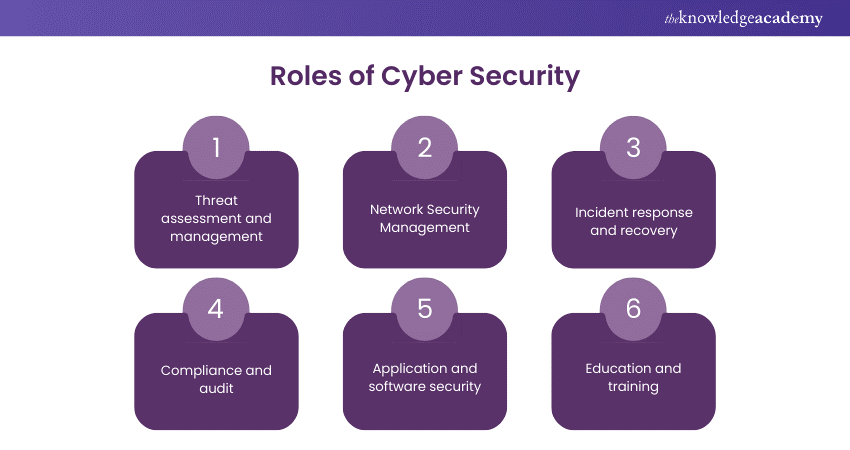
a) Threat assessment and management: The specialists find the possible risks to the organisation's digital assets and suggest ways to cope with them. This includes the monitoring of the new and the upcoming cyber dangers.
b) Network Security MCyber Security standards and regulations. Cyber Security specialists do the security audits to check the security posture of the organisation against these standards.
c) Application and software security: This role is about creating security in the applications and the software, from the design to the development and the updates, so that they are free from vulnerabilities.
d) Education and training: Cyber Security specialists instruct and mentor other employees in the best practices for security and the newest cyber threats. Thus, they spread security awareness in the company.
Learn the basics of Ethical Hacking with our Ethical Hacking Professional Course!
What is the difference between Ethical Hacking and Cyber Security?
Cyber Security safeguards systems and data against cyber threats, whereas Ethical Hacking evaluates weaknesses through simulated attacks. Here are some of the differences between Cyber Security and Ethical Hacking:
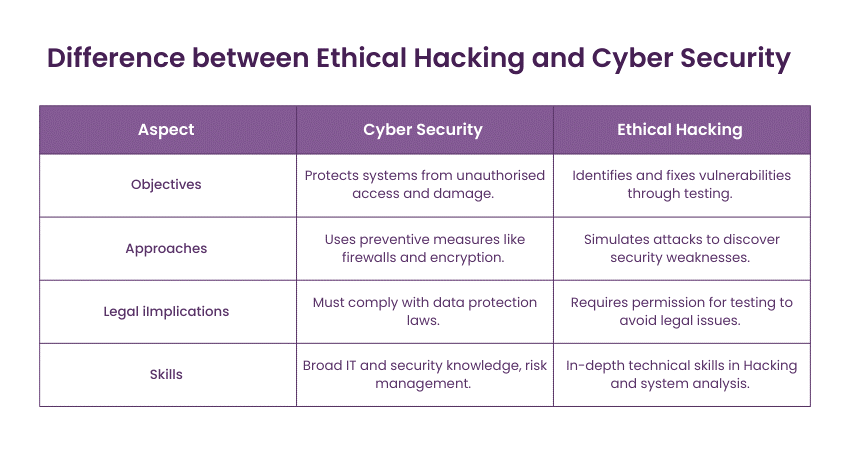
Objectives and approaches
Cyber Security safeguards computer systems, networks and data from unauthorised access, theft and damage. The major objective is to guarantee the confidentiality, integrity, and availability of information. These experts utilise preventive measures like firewalls, encryption, and access controls to protect the systems and reduce cyber threats.
On the other hand, Ethical Hacking, also called Penetration Testing, finds security flaws by imitating real-world attacks. Ethical Hacking experts use the perspective of the attackers to find vulnerabilities which could be exploited. The main purpose is to boost the security by detecting the weak points and offering suggestions for the better.
Legal implications
Another considerable disparity between Cyber Security and Ethical Hacking is the legal aspect. The Cyber Security experts work within the legal framework, obeying the laws and regulations regarding data protection and privacy. Their activities concentrate on the defensive strategies aimed at the systems and data protection from malicious actors. The adherence to legal rules is of great value in the area of Cyber Security.
On the other hand, Ethical Hacking, although performed with permission and authorisation, can face legal problems if it is not done correctly. Ethical Hackers are required to get the consent from the system owners before they conduct Penetration Testing or vulnerability assessments. They also should follow the ethical rules and make sure that their actions do not create any harm or disturbance. The act of obeying the laws is vital to prevent the legal problems.
Skills and expertise
Cyber Security and Ethical Hacking need different skills and knowledge. Cyber Security professionals have a wide knowledge of Information Technology (IT), network security, risk management, and compliance. They understand security frameworks, encryption protocols, and incident response procedures. The robust analytical and problem-solving skills go hand in hand with the identification of vulnerabilities and the implementation of suitable controls.
On the other hand, Ethical Hacking experts need to have technical knowledge in various Ethical Hacking Tools, techniques, and methodologies. They should have detailed understanding of system weaknesses, network protocols, and attack methods. They keep on learning new things to be aware of the new growing threats and the vulnerabilities.
Gain the skills to safeguard sensitive information with our Cyber Security Awareness Course – join today!
Conclusion
Ethical Hacking and Cyber Security are two distinct but related fields. Cyber Security protects systems and data from threats, Ethical Hacking, on the other hand, identifies the vulnerabilities. Each of them is very important for the security of a digital environment, protecting the information, quality and availability. Thus, they are the pillars of the whole security system, which makes it stronger.
Learn how cyber-attacks are executed with our Cyber Security Risk Management Course – join today!
Frequently Asked Questions

The Cyber Security measures should be updated regularly to defend against new and evolving threats. Normally, businesses should analyse and modify their Cyber Security strategies at least once a year or even more if they have particular security problems.

Ethical Hacking is one of the essential elements of Cyber Security. It is a tool to detect and fix system loopholes that can be used by criminal Hackers. Ethical Hackers make organisations more secure by creating simulations of possible security breaches, which shows that their information systems are strong enough to resist cyber threats.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Cyber Security Courses, including the Certified Cyber Security Professional Course, Cyber Security Awareness Course, and Cyber Security Risk Management Course. These courses cater to different skill levels, providing comprehensive insights into Information Security Risk Management.
Our IT Security & Data Protection Blogs cover a range of topics related to Cyber Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cyber Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Ethical Hacking and Penetration Testing Training
Ethical Hacking and Penetration Testing Training
Fri 14th Jun 2024
Fri 20th Sep 2024
Fri 13th Dec 2024









 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


