We may not have the course you’re looking for. If you enquire or give us a call on +352 8002-6867 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

One of the most sought-after certifications in information technology, risk management, and governance is Certified in Risk and Information Systems Control (CRISC). To help you prepare effectively for the exam, here is a list of commonly asked CRISC Exam Questions and their answers.
CRISC-certified professionals are increasingly being hired by organisations nowadays owing to the rise in business risks, especially cyber threats. According to Statista, one of the leading risks businesses face is cyber threats, affecting 34% of organisations worldwide in 2023. Read this blog to learn about the CRISC Exam Questions and answers and tips to enhance your exam preparation and increase your chances of success.
Table of Contents
1) What is the CRISC certification?
2) Exam format and structure
3) Sample CRISC Exam Questions and Answers
a) During a risk assessment, the risk owner should primarily be responsible for
b) Which of the following best describes residual risk?
c) Which of the following is a key role of the risk committee in an organisation?
4) Conclusion
Looking to crack the CRISC EXAM, refer to our blog on "CRISC Study Material"
What is the CRISC certification?
The CRISC certification is a globally recognised credential offered by the Information Systems Audit and Control Association (ISACA). It validates the knowledge and expertise of professionals in risk management, information systems control, and governance. CRISC-certified professionals possess the skills to identify and manage IT risks and implement adequate organisational controls.
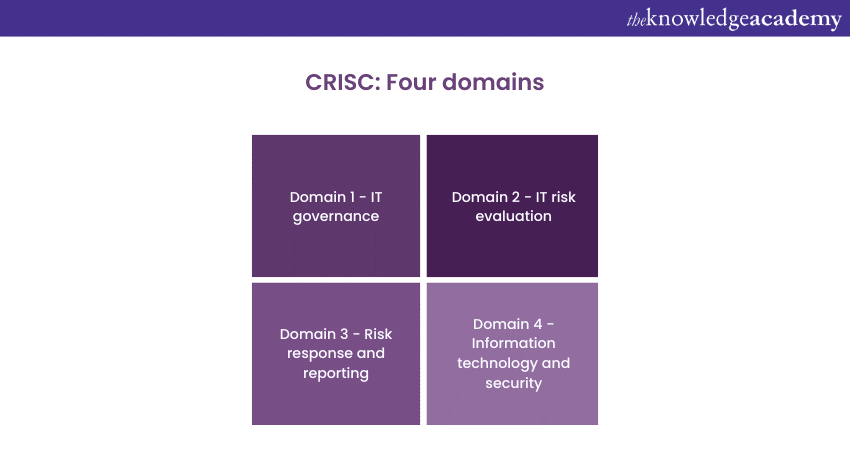
The CRISC certification focuses on four key domains - IT governance, IT risk evaluation, risk response and reporting, and Information Technology and security. These domains encompass the core competencies required to address the challenges associated with IT risk management in today's digital landscape.
Whether you are an IT auditor, risk professional, IT consultant, or aspiring to work in these domains, the CRISC certification can significantly enhance your expertise and credibility. It equips you with the knowledge and skills to manage and mitigate risks effectively, align IT initiatives with business goals, and provide valuable insights for decision-making processes.
Advancing your career in risk management with our CRISC Training courses now!
Exam format and structure
The CRISC exam assesses your knowledge and understanding of the critical domains relevant to risk and information systems control. Understanding its format and structure is essential for adequate preparation and time management during the test. Here are some of the crucial details about the CRISC test format and structure:
1) Number of questions: It consists of 200 questions in total, where 150 of them are multiple-choice questions
2) Time limit: You have four hours (240 minutes) to complete the test
3) Domain weightage: It covers four domains, each with a specific weightage. The domains and their respective weightage are as follows:
Domain 1: IT Risk Identification (27%)
Domain 2: IT Risk Assessment (28%)
Domain 3: Risk Response and Mitigation (23%)
Domain 4: Risk and Control Monitoring and Reporting (22%)
4) Passing score: ISACA does not disclose the passing score for the CRISC exam. The scoring is based on a scaled model, which considers the difficulty level of the questions. ISACA uses a scale from 200 to 800, where the passing score is 450/800.
5) Exam delivery: It is computer-based and is administered at designated testing centres. It is essential to schedule your exam in advance and arrive at the test centre well-prepared and on time.
It is crucial to have a solid understanding of the domains and their interrelationships to succeed in the CRISC exam. It is recommended to allocate sufficient study time to each domain based on its weightage to ensure comprehensive coverage of the content.
Interested in making a career in CRISC, refer to our blog on "CRISC Benefits"

Sample CRISC Exam Questions and Answers
It is important to understand the exam format, structure, and type of questions which can be asked to confidently approach your CRISC assessment and optimise your chances of success. Here is a list of sample CRISC Questions and answers, along with explanations:
1) Which of the following best describes an inherent risk?
a) Risks that can be eliminated through controls
b) Risks that are specific to an individual process
c) Risks that are inherent like an activity or process
d) Risks that can be transferred to a third party
Answer: c) Risks that are inherent like an activity or process
Explanation: Inherent risks are risks that exist within the nature of an activity or process, regardless of any controls that may be in place. These risks cannot be eliminated but can be mitigated through appropriate controls.
2) What is the primary purpose of conducting a risk assessment?
a) To identify potential vulnerabilities in the IT infrastructure
b) To assess the financial impact of a risk event
c) To prioritise risks based on their likelihood and impact
d) To establish a risk mitigation plan
Answer: c) To prioritise risks based on their likelihood and impact
Explanation: The primary purpose of conducting a risk assessment is to evaluate and prioritise risks based on their likelihood and potential impact on the organisation. This helps focus resources on the most critical risks and develop an effective risk management strategy.
3) Which of the following is an example of preventive control?
a) Intrusion detection system
b) Incident response plan
c) Business continuity plan
d) Security awareness training
Answer: a) Intrusion detection system
Explanation: An intrusion detection system is a preventive control that aims to detect and prevent unauthorised access to the organisation's systems and networks. It monitors network traffic for suspicious activities and triggers alerts or takes actions to mitigate potential threats.
4) During a risk assessment, the risk owner should primarily be responsible for:
a) Identifying and assessing risks
b) Implementing risk mitigation measures
c) Monitoring and reporting on risk status
d) Approving risk response strategies
Answer: b) Implementing risk mitigation measures
Explanation: The risk owner is primarily responsible for implementing risk mitigation measures once identified and assessed. They work closely with relevant stakeholders to implement appropriate controls and countermeasures to address identified risks.
5) Which of the following risk response strategies is most suitable for a high-impact risk with a low likelihood of occurrence?
a) Accept
b) Transfer
c) Avoid
d) Mitigate
Answer: b) Transfer
Explanation: Transferring the risk involves shifting the potential impact of the risk to a third party, such as through insurance or outsourcing. This strategy is suitable when the risk's potential impact is high, but the likelihood of occurrence is low.
6) Which of the following is NOT a component of the risk management process?
a) Risk assessment
b) Risk monitoring
c) Risk avoidance
d) Risk treatment
Answer: c) Risk avoidance
Explanation: Risk avoidance refers to eliminating a risk or avoiding activities that would expose the organisation to the risk. While it is a risk response strategy, it is not a component of the risk management process.
7) Which of the following risk response strategies is characterised by reducing the impact of a risk event?
a) Accept
b) Transfer
c) Mitigate
d) Ignore
Answer: c) Mitigate
Explanation: Mitigating risk involves implementing controls or countermeasures to reduce the impact or likelihood of the risk event occurring. It aims to minimise the potential negative consequences associated with the risk.
8) Which of the following is an example of a quantitative risk assessment technique?
a) Delphi technique
b) Risk categorisation
c) Business impact analysis
d) Monte Carlo simulation
Answer: d) Monte Carlo simulation
Explanation: Monte Carlo simulation is a quantitative risk assessment technique that uses probabilistic modelling to simulate various scenarios and assess the impact of uncertainties on project outcomes. It provides numerical estimates and statistical analysis of potential risks.
9) Which of the following is a characteristic of an effective risk management framework?
a) Static and inflexible
b) Focused only on financial risks
c) Supported by senior management
d) Implemented after risk events occur
Answer: c) Supported by senior management
Explanation: An effective risk management framework requires support and commitment from senior management. Their involvement ensures that risk management is prioritised, resourced appropriately, and integrated into the organisation's overall strategy and decision-making processes.
10) Which of the following best describes residual risk?
a) Risk after implementing controls
b) Risk before implementing controls
c) Unknown risk
d) Transferred risk
Answer: a) Risk after implementing controls
Explanation: Residual risk refers to the risk level after implementing controls or mitigation measures. It represents the risk that the organisation is still exposed to despite its risk management efforts.
11) Which of the following is a common technique for identifying risks?
a) Probability distribution analysis
b) Cost-benefit analysis
c) SWOT analysis
d) Regression analysis
Answer: c) SWOT analysis
Explanation: SWOT analysis (Strengths, Weaknesses, Opportunities, Threats) is a technique commonly used to identify risks and assess the internal and external factors that could impact the organisation's objectives. It helps in understanding the risks and aligning risk management strategies accordingly.
12) Which of the following is a key role of the risk committee in an organisation?
a) Implementing risk management processes
b) Assessing the effectiveness of internal controls
c) Monitoring cybersecurity threats
d) Developing risk response strategies
Answer: b) Assessing the effectiveness of internal controls
Explanation: The risk committee is responsible for overseeing the organisation's risk management activities. One of its key roles is to assess the effectiveness of internal controls in mitigating risks and ensuring compliance with relevant policies and regulations.
Conclusion
CRISC is a globally recognised certification which can be acquired upon meeting various prerequisites and passing the test. We hope this blog helped you learn about the various aspects of the CRISC Exam Questions, like its format and structure and familiarise yourself with the type of questions that can be expected for the test.
Sign up for our Certified In Risk And Information Systems Control (CRISC) course and gain the knowledge and skills needed to excel in risk and information systems control now!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified in Risk and Information Systems Control (CRISC)
Certified in Risk and Information Systems Control (CRISC)
Sat 23rd Nov 2024
Mon 9th Dec 2024
Mon 27th Jan 2025
Mon 7th Apr 2025
Mon 14th Jul 2025
Mon 24th Nov 2025







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


