We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Today one of the primary business issues for companies is effectively managing Cyber Security Risks. As organisations prepare for a digital transformation, online threats have also increased. Cyber Security Risk Management is critical for companies, as they maintain the systems and networks while preventing Cyberattacks. In 2021, companies went through 31% more attacks as compared to previous years, according to Accenture’s State of Cybersecurity Resilience 2021 report.
As the reliance on technology increases, the risk of Cyber Security breaches also grows. The growth in the frequency of Cyberattacks and Cyber Risk is due to the increased use of technology as a value driver. Initiatives like outsourcing, use of third-party vendors, remote access, and others focus on driving growth and improving business efficiency. However, these also increase the Cyber Risk exposure of the company. Due to this, Cyber Security Risks have become more of a technology issue rather than an organisational problem.
This blog introduces Cyber Security Risks, their various types and ways to manage these risks and vulnerabilities.
Learn Cyber Security skills from top experts.
Table of Contents
1) What is Cyber Security?
2) What is Cyber security Risk?
3) Economic importance of Cyber attacks
4) Difference between risk, threat, and vulnerability
5) Compliance ≠ Risk Management
6) Compliance and security are not the same thing.
7) Types of Cyber Security Risks
8) Who manages Cyber Security?
9) Conclusion
What is Cyber Security?
Cyber Security is the use of technologies, processes and practices to protect an organisation’s intellectual property, customer data and other confidential information from unauthorised access by cyber criminals. Cybercrime is becoming more frequent and severe and there is a great need for better Cyber Security Risk Management as part of every organisation’s enterprise risk profile.
No matter what your organisation’s risk tolerance is, you need to incorporate Cyber Security planning as part of your enterprise Risk Management process and regular business operations. It’s one of the biggest threats to any business.
Want to learn about different types of Ransomwares, Spyware, and Malware? Join the Cyber Security Awareness Course – today!
What is Cyber Security Risk?

Cyber Security Risk, or IT Security Risk, is the chance of losing or damaging something because of the company’s information or communication systems. It is linked to the lack of privacy in systems and networks. Such risks reveal the possibility of a bad effect on the company’s activities. This meaning of Cyber Security Risk shows a possible negative event caused by a Cyberattack or a data leak on the organisation. The main goal of these threats is to break into the network, ruin the data, and take secret and private information from a company’s servers.
Cyber Security Risks can cause money loss, damage the reputation or steal intellectual property. Many things can make Cyber Security Risks worse. These can be things like a planned illegal security break to get information and data or because of bad security systems.
Not managing the Cyber Security Risk can make an organisation face Cybercrimes and Cyberattacks that can make the company lose money and data. Also, these events can affect how people see the organisation. These situations also hurt the trust of the company. After these events, it can be hard for the company to get back the lost data or stop future attacks. So, strong Cyber Security actions are very important for companies.
Economic importance of cyber attacks
General IT security systems help eliminate simple security risks. But they could be more effective in reducing attacks from advanced cyber attacks. With access to advanced technologies, hackers and Cybercriminals can carry out complex and sophisticated Cyberattacks. It helps them gain access to information and data of companies. The chances of Cyberattack increase because companies are now recording and storing vast amounts of Personally Identifiable Information (PII) on their servers and clouds. Such information attracts hackers and Cybercriminals. They can sell or even hold companies at ransom in exchange for the data.
The number of devices connected to organisations' networks for accessing and sharing data has increased. Technological advancements have made it easier for stakeholders such as staff and customers to access information easily and quickly. Thus, the risk of future attacks like Ransomware and bugs increases.
Cyberattacks can come from many potential sources, for example, hostile foreign powers, coordinated hacking attacks, etc. In addition, Cyber laws and policies are becoming stricter to help eliminate such risks and provide better security for data and IT infrastructure. Companies are now adopting different tools and systems that can help mitigate such risks.
The costs of such attacks are significant for businesses. Due to this, there is an increased focus on determining ways to manage and reduce such risks. The importance of identifying, addressing, and communicating a potential breach far outweighs the preventive value of traditional Cyber Security controls.
When an organisation becomes a victim of such attacks, it must spend significant resources like time and money to secure its systems and IT infrastructure. The company also has to experience damage to its reputation and image. It is apart from bearing the cost of fixing the damages caused by the attack.
Data breaches and Cyberattacks have a significant negative impact on businesses. Thus, a robust Cyber Security Risk Management policy will help the company to eliminate such risks.
Join the Certified Cyber Security Professional (CCS-PRO) course to learn Phishing, Web Security, and Hacking.
Difference between risk, threat, and vulnerability
The number of things to consider in Cybersecurity is limitless. IT security has three essential aspects - Threats, Risks, and Vulnerabilities.
Vulnerability
It is a weakness or shortcoming in a system. Generally, vulnerabilities exist in infrastructure or databases but can also be in processes and control measures. Dealing with some vulnerabilities can be very simple when it is known to the relevant persons. But, when a vulnerability is unknown, i.e., IT professionals do not know about exposure, it can be dangerous and cause significant damage. The more vulnerabilities there are, the more the chances of Cyber Security Risks in the systems and networks.
Threat
A threat has the power to exploit vulnerabilities in the system that can affect the confidentiality and integrity of the system and data. It can also be defined as when an attacker or hacker has the opportunity and possesses the capability to influence the networks adversely. Malware and Ransomware are some of the commonly known types of threats.
Risk
Risk is the probability of a harmful event that can significantly damage the network and systems. Organisational risk can fluctuate daily because of both internal and external factors. A Cyber Security Risk encompasses the potential of an adverse event and the impact it may have on the infrastructure. Such risks can never be eliminated, unlike a threat or vulnerability. Advancement in Cyber Security technology helps in significantly minimising the risks.

Compliance ≠ Risk Management
Sometimes, organisations do not perform Risk Management to improve their outcomes. Instead, they do it for ‘compliance’ reasons, such as:
a) Meeting external expectations (like regulations)
b) Satisfying customers’ needs
This can make Risk Management a superficial activity. This can also make organisations think they have dealt with a risk, when they have only followed a procedure that may cause (unwanted) problems.
Compliance and security are not the same thing
Some people call Risk Management done for compliance reasons ‘defensive Risk Management’. This kind of Risk Management can make organisations care too much about saving their image (or avoiding legal troubles or other external penalties). Defensive Risk Management is about showing that you did not do anything wrong if something bad happens. The focus is on showing that you took some action.
This does not have to be a bad thing. Compliance needs are hard to avoid in many sectors. But, if you do defensive Risk Management, you should:
a) Make sure staff know that Cyber Risk Management aims to satisfy external expectations (not to meet specific security goals)
b) Know the drawbacks of the Risk Management methods that you use to be compliant
c) Use more methods that deal with the drawbacks of compliance (this guidance can help you with some types of methods).
Learn the basics of Ethical Hacking with the Ethical Hacking Professional course.
Types of Cyber Security Risks
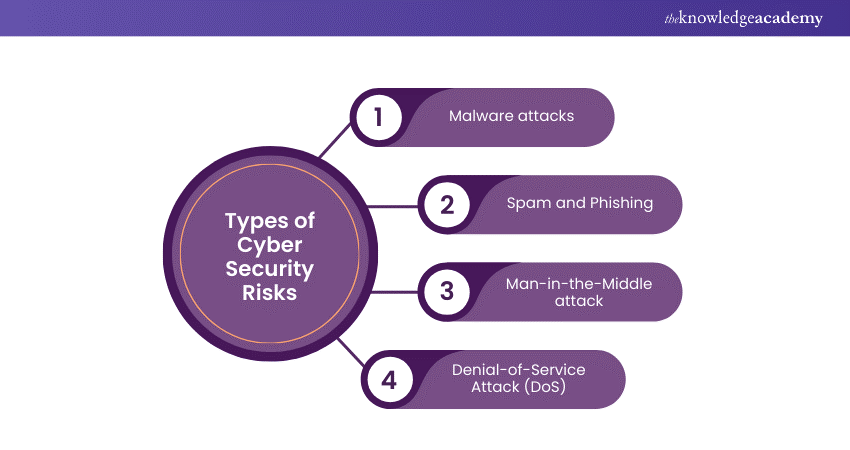
Technological development has given birth to several Cyber Security Risks. Some of them are as follows:
1) Malware attacks
It is malicious software such as spyware, viruses or worms. It is inserted in a system to compromise the data's confidentiality, integrity or availability. Today, it is one of the most prominent external threats and can cause widespread damage and disruption to the network. Significant efforts are required to fix the damage and manage the situation.
Malware gets activated when the user clients on a malicious link or attachment, which results in downloading dangerous software. Malware, once activated, can block access to network components, install harmful software, secretly collect information about the user, and disrupt individual parts of the computer systems and networks. Following is a list of malwares usually used to initiate attacks:
a) Viruses: A piece of code inserts itself into an application. The application runs and the malicious code executes.
b) Worms: Malware that uses software flaws and hidden entrances to access an operating system. The worm can perform attacks such as Distributed Denial of Service (DDoS) once it is in the network.
c) Trojans: Malicious code or software that pretends to be a harmless program, hiding in apps, games or email attachments. A user downloads the trojan unknowingly, allowing it to take control of their device.
d) Ransomware: A user or organisation cannot access their own systems or data because they are encrypted. The attacker usually asks for a ransom to be paid in exchange for a decryption key to restore access, but there is no guarantee that paying the ransom will restore full access or functionality.
e) Cryptojacking: Attackers put software on a victim’s device, and start using their computing power to create cryptocurrency, without their awareness. Affected systems can lose speed and cryptojacking kits can harm system stability.
f) Adware: A user’s browsing habits are monitored to identify behaviour trends and preferences, enabling advertisers to send the user personalised ads. Adware is similar to spyware but does not require installing software on the user’s device and is not always used for harmful purposes, but it can be used without the user’s permission and violate their privacy.
g) Fileless malware: does not install any software on the operating system. It modifies native files such as WMI and PowerShell to execute malicious actions. This type of attack is hard to spot (antivirus cannot detect it), because the altered files are seen as valid by the system.
2) Spam and Phishing -
Spam consists of unwanted messages and emails, while Phishing is described as a form of social engineering aimed at getting access to sensitive information. Phishing attempts generally are made to appear as if from a trustworthy person or business. It is one of the most common and easy-to-use methods of Cybercrime.
3) Man-in-the-Middle attack
A Man-in-the-Middle (MitM) attack is when an attacker intercepts the communication between two parties, for example, a user and an application. The attacker can listen to the communication, take confidential data, and pretend to be each party in the communication. Examples of MitM attacks include:
a) Wi-Fi eavesdropping: An attacker creates a Wi-Fi connection, pretending to be a trustworthy entity, such as a business, that users may join. The fake Wi-Fi enables the attacker to spy on the activity of connected users and capture data such as payment card information and login details.
b) Email hijacking: An attacker imitates the email address of a valid organization, such as a bank, and uses it to deceive users into giving up confidential information or sending money to the attacker. The user follows instructions they believe come from the bank but are in fact from the attacker.
c) DNS spoofing: A Domain Name Server (DNS) is tampered with, sending a user to a harmful website that looks like a genuine site. The attacker may redirect traffic from the real site or take the user’s credentials.
4) Denial-of-Service Attack (DoS)
A Denial-of-Service attack floods the target system with too much traffic, preventing the system from working properly. An attack that uses multiple devices is called a distributed Denial-of-Service (DDoS) attack. DoS attack techniques include:
a) HTTP flood DDoS: The attacker sends HTTP requests that look valid to overload an application or web server. This technique does not need high bandwidth or corrupted packets, and usually tries to make the target system use as many resources as possible for each request.
b) SYN flood DDoS: Starting a Transmission Control Protocol (TCP) connection sequence involves sending a SYN request that the host must reply to with a SYN-ACK that confirms the request, and then the requester must reply with an ACK. Attackers can take advantage of this sequence, using up server resources, by sending SYN requests but not replying to the SYN-ACKs from the host.
c) UDP flood DDoS: A remote host is bombarded with User Datagram Protocol (UDP) packets sent to random ports. This technique makes the host look for applications on the affected ports and reply with “Destination Unreachable” packets, which drains the host resources.
d) ICMP flood: A flood of ICMP Echo Request packets swamps the target, using up both inbound and outbound bandwidth. The servers may try to reply to each request with an ICMP Echo Reply packet, but cannot match the speed of requests, so the system slows down.
Who manages Cyber Security?
Cyber Security has become an essential part of the operations of companies. It is now imperative for organisations to ensure that their systems and networks are safe and do not become a victim of a Cyber attack.
Many companies think that IT professionals are solely responsible for ensuring Cyber Security in their systems. However, this is not true. Every company employee has a duty to keep the systems secure. Moreover, the company also needs to have a clear Incident Response Plan that defines the roles and responsibilities of every person.
Conclusion
Cyber Security is essential for companies and business processes due to rapid technological advancements. It has become imperative for organisations to determine ways to reduce Cyber Risks. This blog aimed at introducing Cyber Security Risks and presenting their various types. We hope that you understand the different types of Cyber Security Risks and their impact on business organisations' operations.
Learn the common network application operations and attacks with the CCNA Cyber Security Operation Training.
Frequently Asked Questions

The most common Cyber Security risk is human error. Whether through phishing attacks, weak passwords, or lack of awareness, employees often unintentionally compromise security. Addressing this risk requires robust training programs, regular security awareness initiatives, and implementing technical safeguards to minimize the impact of potential errors.

High risk in Cyber Security refers to vulnerabilities or threats with significant potential for harm to an organisation's digital assets. This includes sophisticated malware, unpatched software, weak passwords, and human errors. Failure to address high-risk factors can lead to data breaches, financial losses, and reputational damage. Implementing robust security measures is crucial to mitigate these risks and safeguard sensitive information.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Cyber Security Training, including Certified Cyber Security Professional (CCS-PRO), Cyber Security Awareness etc. These courses cater to different skill levels, providing comprehensive insights into becoming a Cyber Security Expert.
Our IT Security & Data Protection covers a range of topics related to Cyber Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Cyber Security Risk Management
Cyber Security Risk Management
Fri 13th Sep 2024
Fri 20th Dec 2024
Fri 24th Jan 2025
Fri 2nd May 2025
Fri 22nd Aug 2025
Fri 21st Nov 2025









 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


