We may not have the course you’re looking for. If you enquire or give us a call on +61 272026926 and speak to our training experts, we may still be able to help with your training requirements.

close
Press esc to close
Stage 2 is Do. This involves the application and operation of the ISMS, the security policy, controls, processes and procedures.
Stage 3 is Check. This means monitoring and reviewing the ISMS. To do this, process performance needs to be assessed and where relevant measured against security policy, practical experience and targets. The results then need to be reported to management for them to review.
The final stage is to act. This involves maintaining and improving the ISMS; taking correct and anticipatory actions, based on the management review results in order to achieve continual improvement of the ISMS.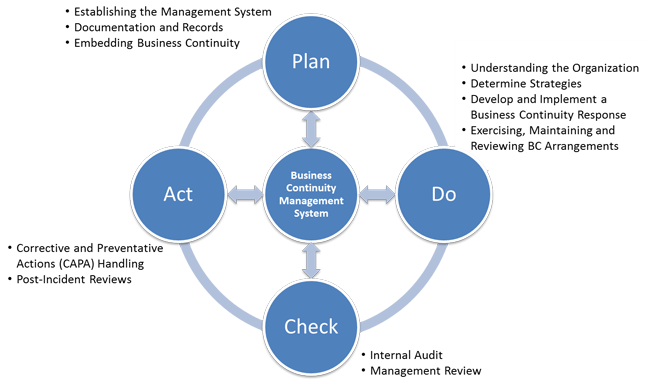

close


Press esc to close

close
Fill out your contact details below and our training experts will be in touch.



Back to Course Information